Trying to have tags automatically added to objects post-upload following this guide https://heywoodonline.com/posts/Automatically Tagging Uploads to S3.html But when the function runs I'm getting the following error
[ERROR] ClientError: An error occurred (AccessDenied) when calling the PutObjectTagging operation: Access Denied
Traceback (most recent call last):
File "/var/task/lambda_function.py", line 37, in lambda_handler
raise e
File "/var/task/lambda_function.py", line 22, in lambda_handler
response = s3.put_object_tagging(
File "/var/runtime/botocore/client.py", line 386, in _api_call
return self._make_api_call(operation_name, kwargs)
File "/var/runtime/botocore/client.py", line 705, in _make_api_call
raise error_class(parsed_response, operation_name)
I've checked the Role that's created found in the Configuration menu config menu Role
Editing that brings me to this policy, which I've added a bunch of Actions to.
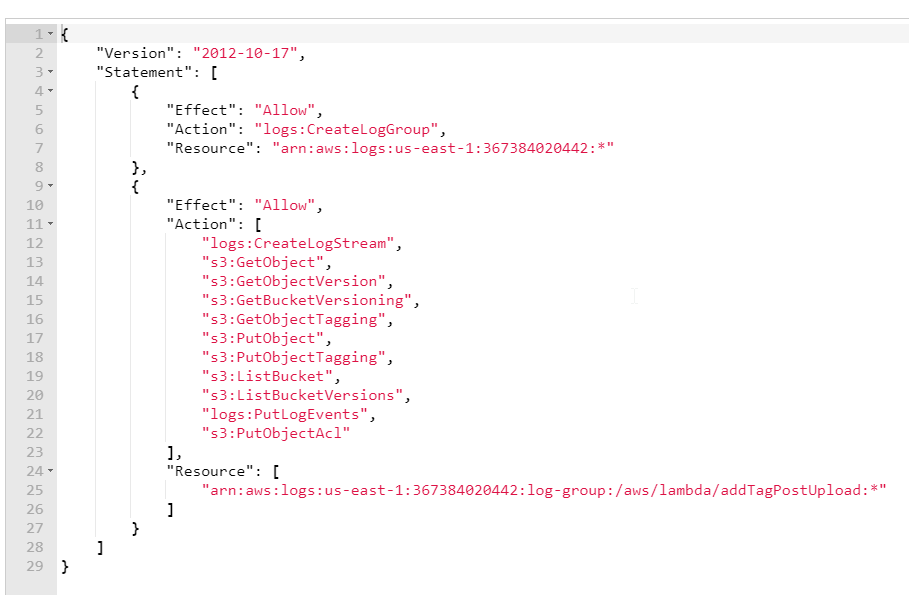
Anything I add to the policy seems to be ignored as I continue to get the same Access Denied error.
Other similar posts to stackOverflow do not mention what policy needs to be edited but when I search the roles there is only one with the title I gave it. It's got to be the one.
What am I missing?
EDIT: FIXED! I added a new resource to the above policy and it worked as needed.
"Resource": [
"arn:aws:logs:us-east-1:367384020442:log-group:/aws/lambda/addTagPostUpload:*",
"arn:aws:s3:::*/*"
]
CodePudding user response:
You policy only mentioned 'logs' resources and not s3 resources. Unless you specify what s3 resources your s3 actions have permissions on, it does not matter what you put in actions. Right now the policy says you have s3 and logs action permissions on the specified cloudwatch log group and nothing else
