I have set up a bucket on Amazon AWS using the Amplify, CLI console. I've followed the documentation for the Amplify iOS SDK, and have the following setup code on the iOS app:
do {
try Amplify.add(plugin: AWSCognitoAuthPlugin())
try Amplify.add(plugin: AWSS3StoragePlugin())
try Amplify.configure()
} catch {
print(message: "An error occurred setting up Amplify: \(error)")
}
When I try to download a resource I get the following error:
StorageError: The HTTP response status code is [403].
I am using the following code:
var url: URL = //url to download to
var key: String = //key for the file as specified in S3
operation = Amplify.Storage.downloadFile(key: key,
local: url) { [weak self] progress in
guard let _ = self else { return }
print(message: "progress: \(progress.fractionCompleted)")
} resultListener: { [weak self] result in
guard let _ = self else { return }
switch result {
case .success:
print(message: "success!")
case .failure(let error):
print(message: "error: \(error)")
}
}
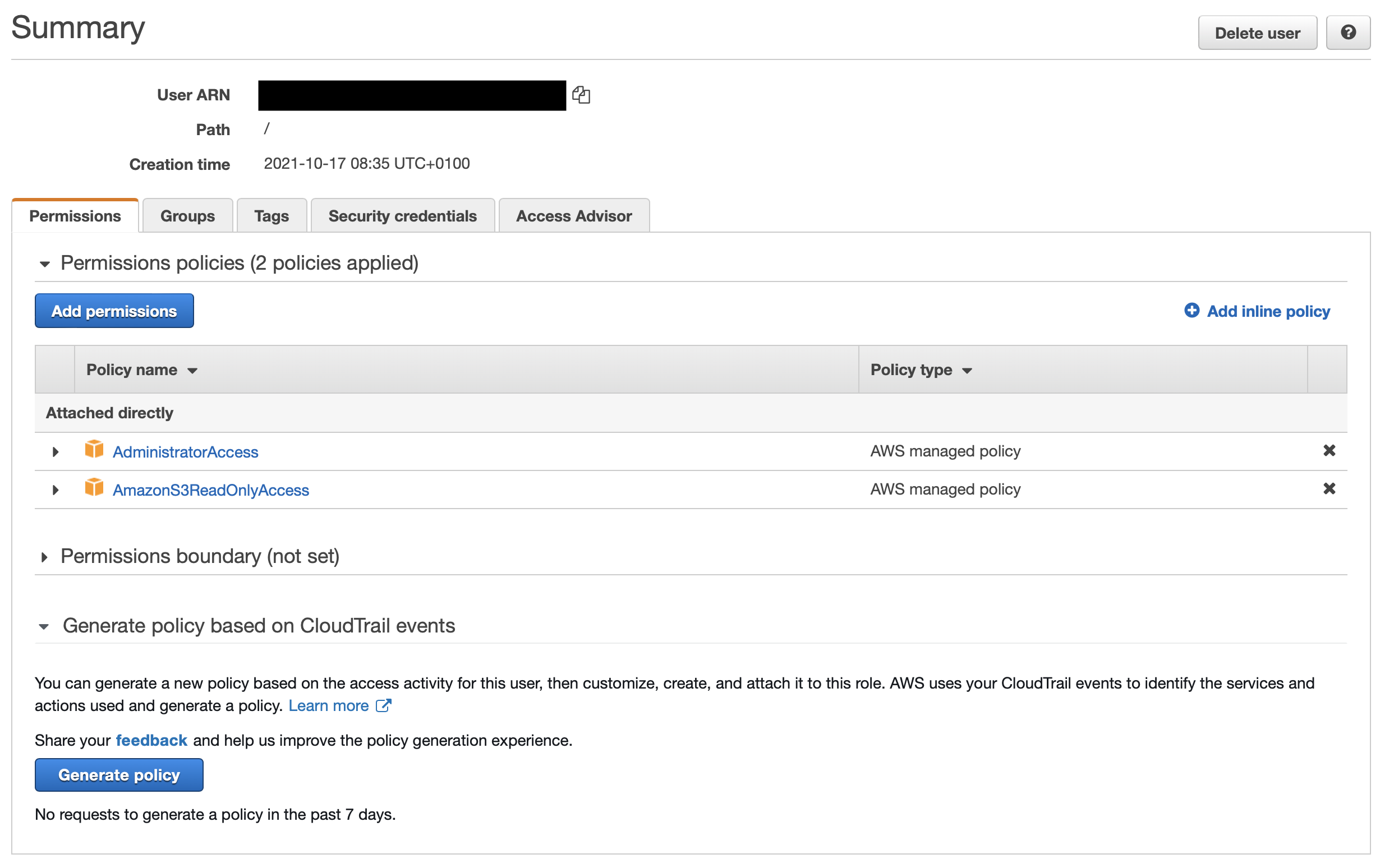
The user I set up via amplify configure has AdministratorAccess and AmazonS3ReadOnlyAccess policies attached:
What am I missing?
CodePudding user response:
The user-created via amplify configure is used by Amplify for provisioning of resources - you've assigned AdministratorAccess and AmazonS3ReadOnlyAccess policies to your Amplify user but not to the unauthenticated user role, which is what is used by Amplify guest users.
Find the role name for the unauthenticated role first, by signing in to the 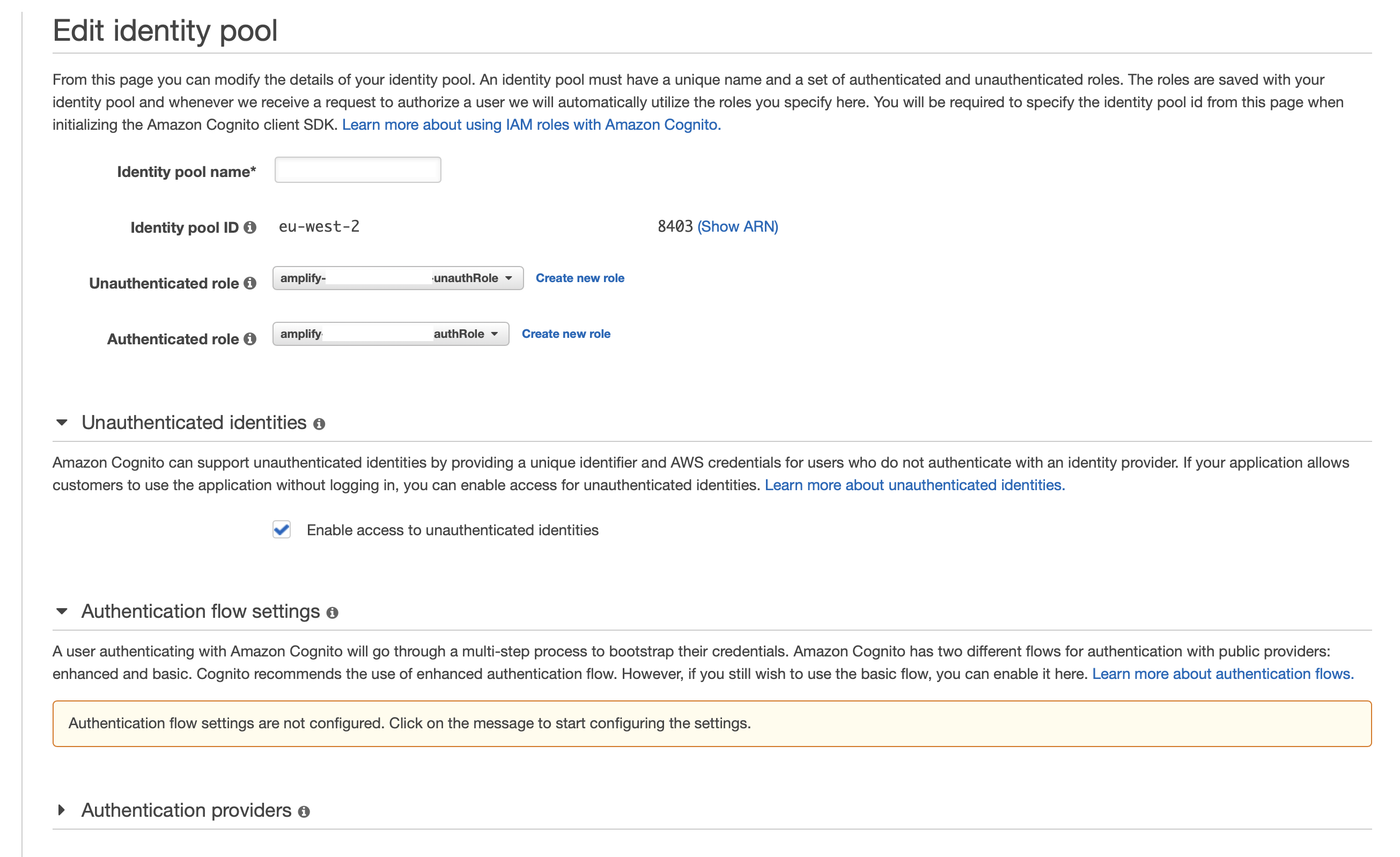
The current role being used for guest/unauthenticated users will be in the dropdown.
Lookup the role name inside the IAM console & then attach the AWS-managed AmazonS3ReadOnlyAccess policy to the role.
Your unauthenticated users should now have access to read files from the S3 buckets & you should no longer get a 403 Access Denied error.