I am a neophyte, I'm trying to configure my project on gitlab to be able to integrate it with a kubernetes cluster infrastructure pipeline. While I am configuring gitlab asked for a certificate and a token. Since kuberntes is deployed on azure, how can I create/retrieve the certicate and required token? Possibly which user / secret in the kuberntes service does it refer to?
CodePudding user response:
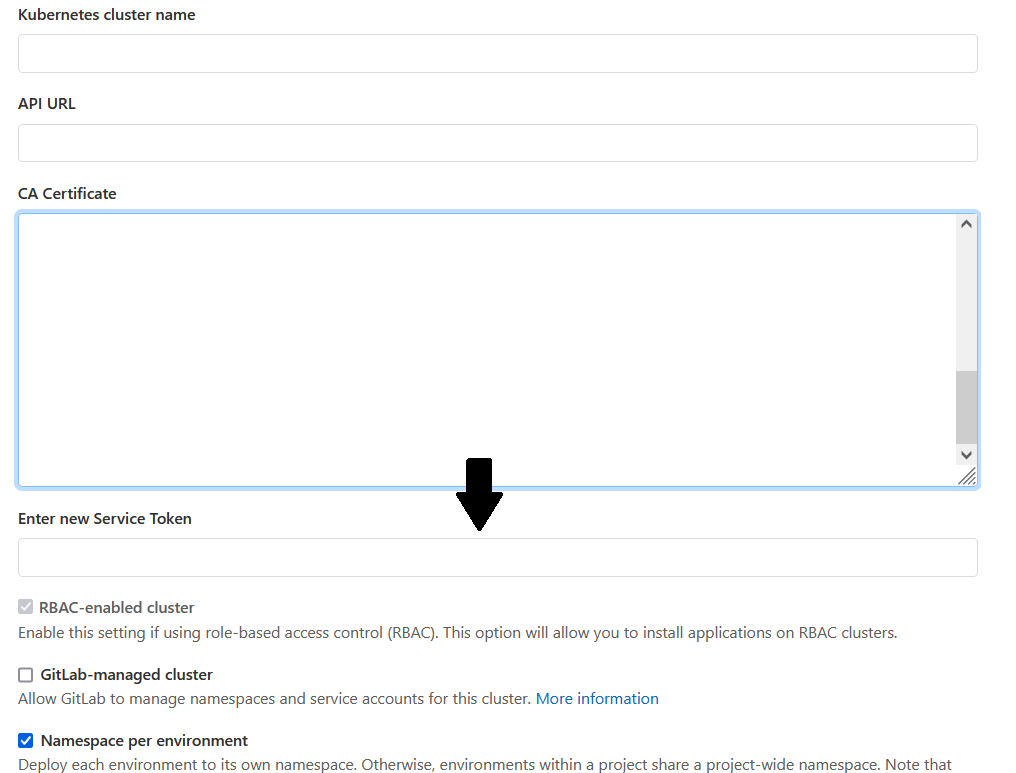
You can get the default values of CA certificate using the below steps :
CA Certificate:
CA certificate is nothing but the Kubernetes certificate that we use in the config file for authenticating to the cluster.
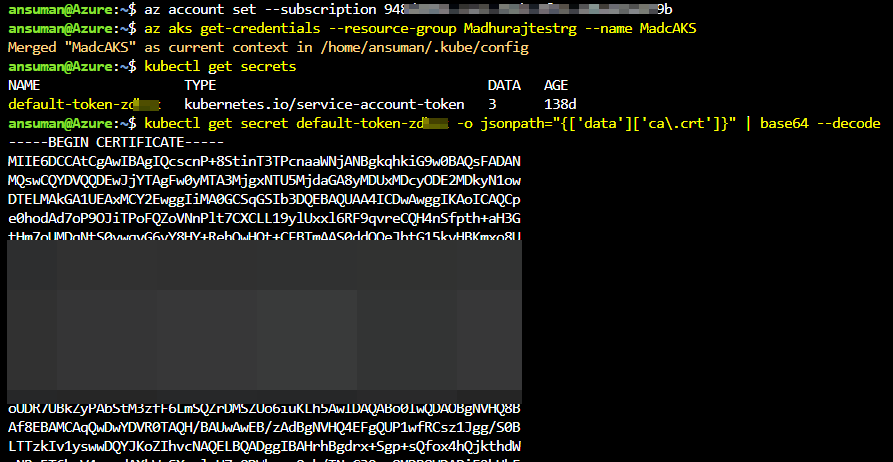
- Connect to AKS cluster,
az aks get-credentials — resource-group <RG> — name <KubeName> - Run
kubectl get secrets, after you run command in output you will get a default token name , you can copy the name. - Run
kubectl get secret <secret name> -o jsonpath="{['data']['ca\.crt']}" | base64 --decodeto get the certificate , you can copy the certificate and use it in setting the runner.
Output:
Token :
The token will be of the service account with cluster-admin permissions which Gitlab will use to access the AKS cluster , so you can create a new admin service account if not created earlier by using below steps:
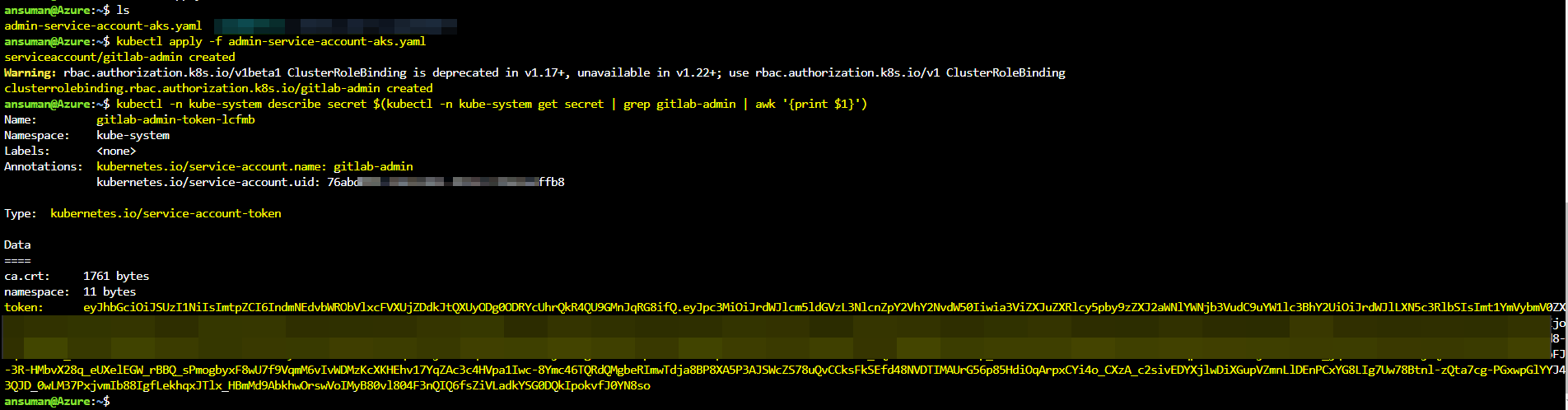
Create a Yaml file with below contents :
apiVersion: v1 kind: ServiceAccount metadata: name: gitlab-admin namespace: kube-system --- apiVersion: rbac.authorization.k8s.io/v1beta1 kind: ClusterRoleBinding metadata: name: gitlab-admin roleRef: apiGroup: rbac.authorization.k8s.io kind: ClusterRole name: cluster-admin subjects: - kind: ServiceAccount name: gitlab-admin namespace: kube-systemRun
kubectl apply -f <filename>.yamlto apply and bind the service account to the cluster.Run
kubectl -n kube-system describe secret $(kubectl -n kube-system get secret | grep gitlab-admin | awk '{print $1}')to get the token for the Gitlab Admin we created in the file and bind with the cluster in the previous step. You can copy the token value and use it in the runner setting .
Output: