I'm relatively new to Azure and I'm working to figure out how to integrate usage into our legacy applications. There no plans to rewrite/migrate these applcations to .Net Core.
I have a .Net Framework (Not Core) Asp.Net web application. I have it hosted in an Azure App Service. I've created an Azure Key Vault service and secret. Using the App Service's system defined identity, I've added access to the Key Vault instance.
How do I access the Key Vault and contained secret from an Asp.Net application? Pretty much all the examples/samples I've seen were .Net Core based.
Would a similar approach work with a .Net Framework console application?
CodePudding user response:
- Configuration builders in ASP.NET provide a way to modify and override the values from your
web.configfile by usingKey Vault.
Steps to Implement
Add secrets to the Key Vault - Steps to create Key Vault
It’s important that the secrets must have the same name as the app settings you would like to replace with them. Example if you have an app setting with the key
MyConnStrin yourWeb.configfile, you must create a secret with the same name and the same value in Key Vault.Give access to your Web App to the secrets stored in Key Vault. Use Web App’s managed identity feature.
a. Enable System Managed Identity on the Web App:
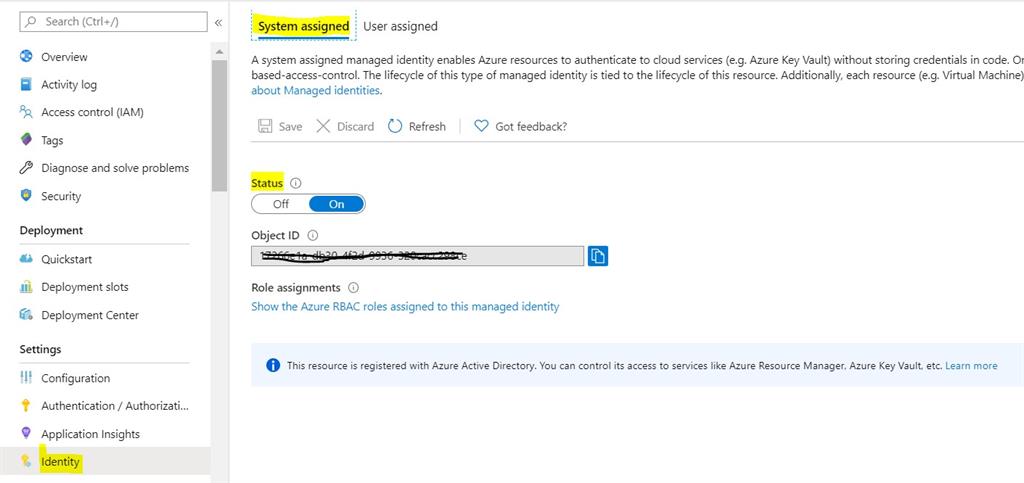
b. Grant access to the web app on the Key Vault with relevant permissions
Go to your Key Vault and navigate to Access Policies in the left navigation:
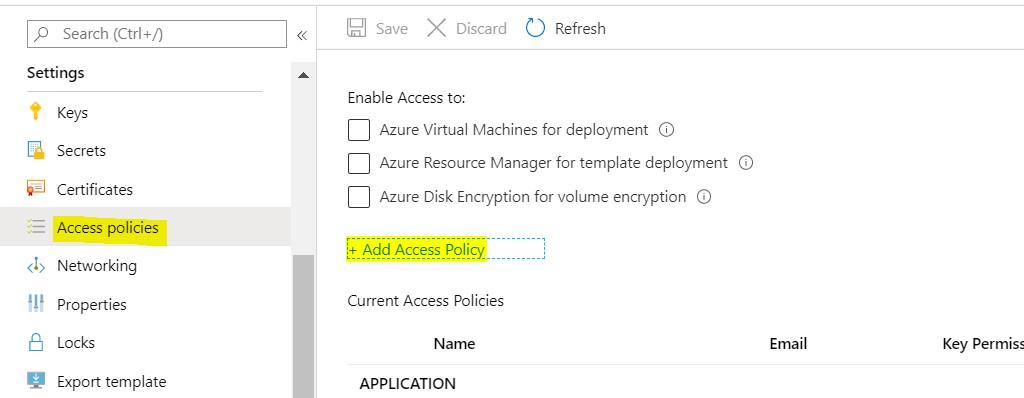
- Select the required permissions.
- Add the below NuGet packages to your project:
_Microsoft.Azure.KeyVault_
_Microsoft.Azure.KeyVault.WebKey_
_Microsoft.Azure.Services.AppAuthentication_
_Microsoft.Configuration.ConfigurationBuilders.Azure_
_Microsoft.Configuration.ConfigurationBuilders.Base_
_Microsoft.IdentityModel.Clients.ActiveDirectory_
_Microsoft.Rest.ClientRuntime_
_Microsoft.Rest.ClientRuntime.Azure_
- Modify your
appsettingsandconnectionstringstag in yourWeb.config
<appSettings configBuilders="AzureKeyVault">
<add key="KEY_VAULT_NAME" value="from key vault" />
</appSettings>
<configBuilders>
<builders>
<add name="AzureKeyVault" vaultName="${KEY_VAULT_NAME}" type="Microsoft.Configuration.ConfigurationBuilders.AzureKeyVaultConfigBuilder, Microsoft.Configuration.ConfigurationBuilders.Azure, Version=2.0.0.0, Culture=neutral" />
</builders>
</configBuilders>
- In you .cs file add,
var MyKey=ConfigurationManger.AppSettings["KEY_VAULT_NAME"];
- Add a break point on the configuration value, you can see the application is reading from Azure Key Vault instead of the value provided in the configuration file.
Please refer MS Doc for more information.
The above solution works great when I'm running the web application deployed in the Azure App Service. When I attempt to run locally, I get an exception..
Configuration Error Description: An error occurred during the processing of a configuration file required to service this request. Please review the specific error details below and modify your configuration file appropriately.
Parser Error Message: The configBuilder 'AzureKeyVault' failed while processing the configuration section 'appSettings'.: Error in Configuration Builder 'AzureKeyVault'::GetValue(AppName)
