Currently my S3 policy is like this below.
What I want to do is restrict read/write S3 access from a lambda. And enable public read access to S3.
{
"Version": "2012-10-17",
"Statement": [
{
"Effect": "Allow",
"Principal": {
"AWS": "*"
},
"Action": "s3:GetObject",
"Resource": "arn:aws:s3:::s3-static-resource-v/*"
},
{
"Effect": "Allow",
"Principal": {
"AWS": "arn:aws:iam::678100228133:role/vr-resource-CustomS3AutoDeleteObjectsCustomRes-1H51E87NWQJ81"
},
"Action": [
"s3:GetBucket*",
"s3:List*",
"s3:DeleteObject*"
],
"Resource": [
"arn:aws:s3:::s3-static-resource-v",
"arn:aws:s3:::s3-static-resource-v/*"
]
}
]
}
I guess I should add the lambda arn in Principal,
so I changed,
"Principal": {
"AWS": "*"
},
to lambda arn, but
"Principal": {
"AWS": "arn:aws:lambda:ap-northeast-1:67810022843r:function:vr-dev-lambda"
},
but it shows
Invalid principal in policy
How can I set here?
CodePudding user response:
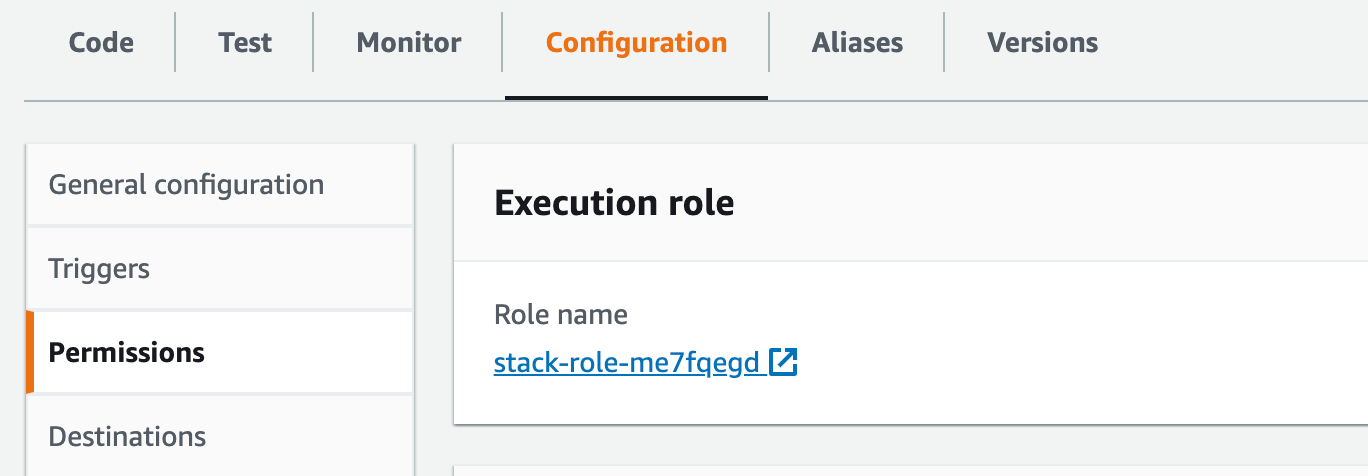
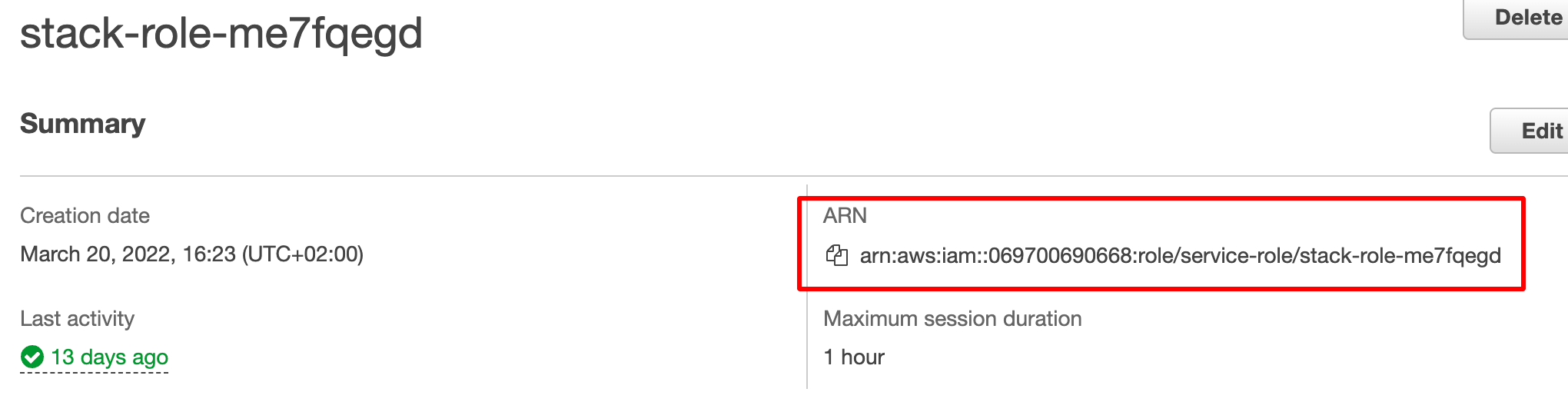
Lambdas have an execution roles attached to them. For example:
If you want to limit the S3 access to your Lambda, you would want to specify the ARN of this execution role.