I'm trying to build an Enterprise App in Azure that will support SSO using OpenID Connect and User Provisioning using a SCIM API.
When I create the application using the OpenID Connect approach I don't have an option to enable user provisioning. If I do the Non-gallery approach I can enable user provisioning and test out my SCIM API. Am I missing something? Why is that option not available for OpenID Connect?
I followed this diagram to pick the correct SSO. 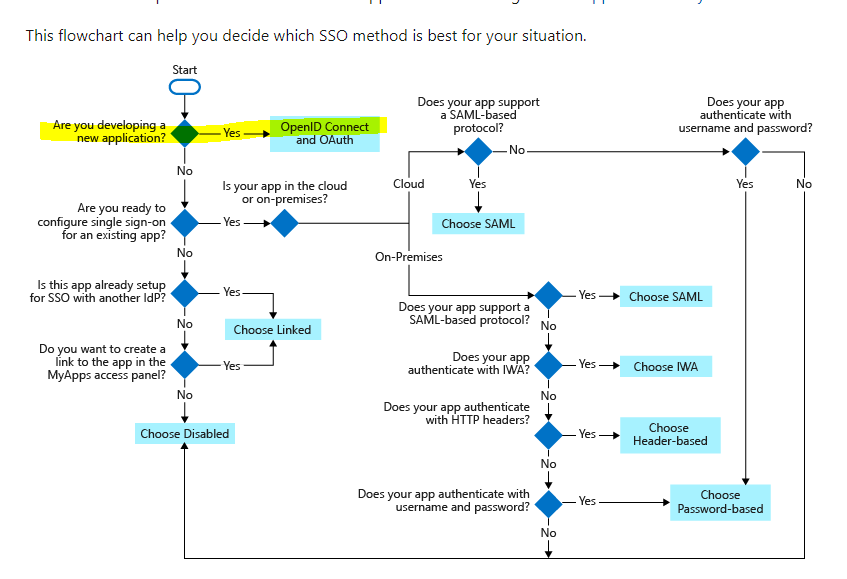
Then selected the "App you're developing" option in Azure.
Once I go to the Provisioning part the "Get started" button is disable:
BUT if I choose the Non-Gallery option when creating the application the Provisioning part is enabled and allows we to step through the wizard to wireup to a SCIM API:
CodePudding user response:
According to Azure ad app-provisioning-known-issues -microsoft docs
If you create an app registration, the corresponding service principal in enterprise apps won't be enabled for automatic user provisioning. Your app needs to be in the gallery to have provisioning enabled.For that You'll need to either request the app be added to the gallery, if intended for use by multiple organizations, or create a second non-gallery app for provisioning.
To get your app in the gallery, see how to-app gallery listing
See SaaS App Integration Tutorials for use with Azure AD | Microsoft Docs
References:
- Azure AD Enterprise application not showing 'automatic' provisioning mode - Stack Overflow
- Problem configuring user provisioning to an Azure Active Directory Gallery app | Microsoft Docs
CodePudding user response:
You've already identified what works right now - non-gallery OIDC apps can't support SCIM provisioning today, so you'll need a second app. We're (Microsoft) looking to enable the ability to enable SCIM provisioning on non-gallery OIDC apps, but there are some security/privilege escalation issues that need to be addressed first.