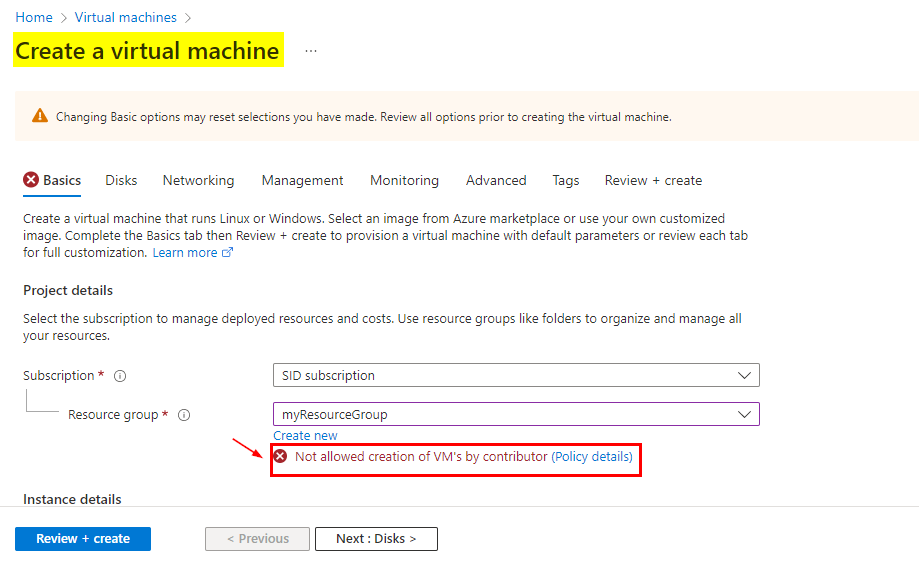
I have written some automation (using az command line) that creates virtual machines for us.
However, since users have contributor access to the various subscriptions they login to the portal and create the vm's manually.
I would like to prevent the users from creating the vms by logging into the portal.
How do I leverage Azure Policy to enforce this ?
CodePudding user response:
I tried to reproduce this scenario on my end and was able to restrict users with Contributor Role from creating VM via Portal.
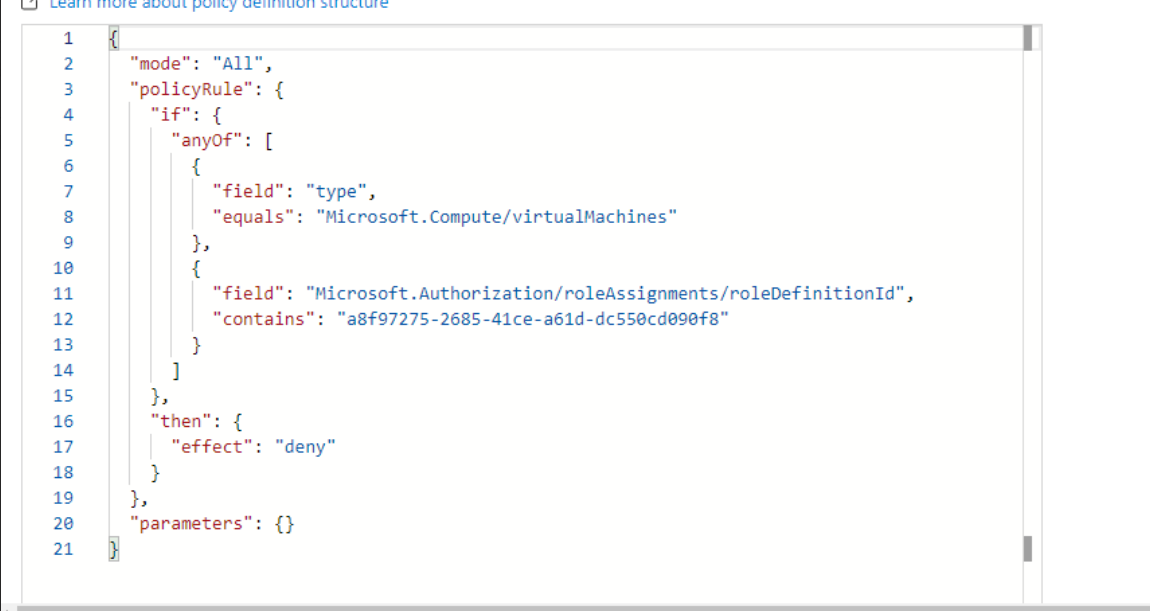
I created one Policy Definition like below: -
"parameters": {},
"policyRule":
{
"if": {
"anyOf": [
{
"field": "type",
"equals": "Microsoft.Compute/virtualMachines"
},
{
"field": "Microsoft.Authorization/roleAssignments/roleDefinitionId",
"contains": "a8f97275-2685-41ce-a61d-dc550cd090f8"
}
]
},
"then":
{
"effect": "deny"
}
}
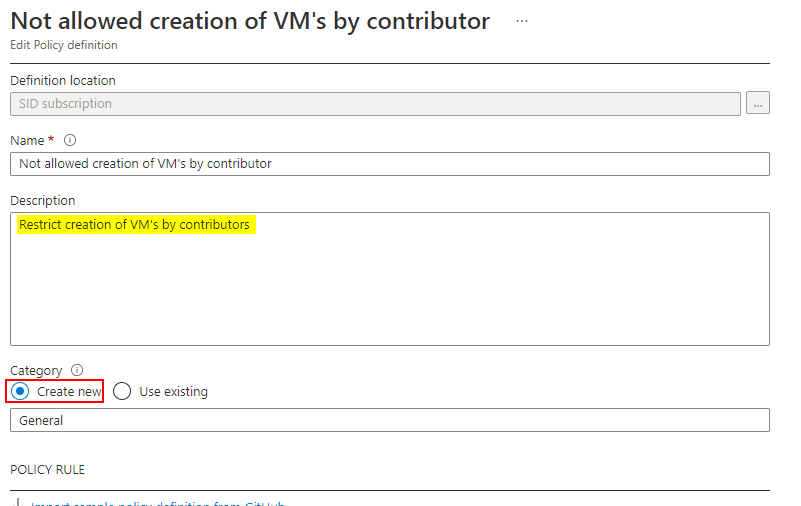
 And assigned this policy at the subscription level: -
And assigned this policy at the subscription level: -
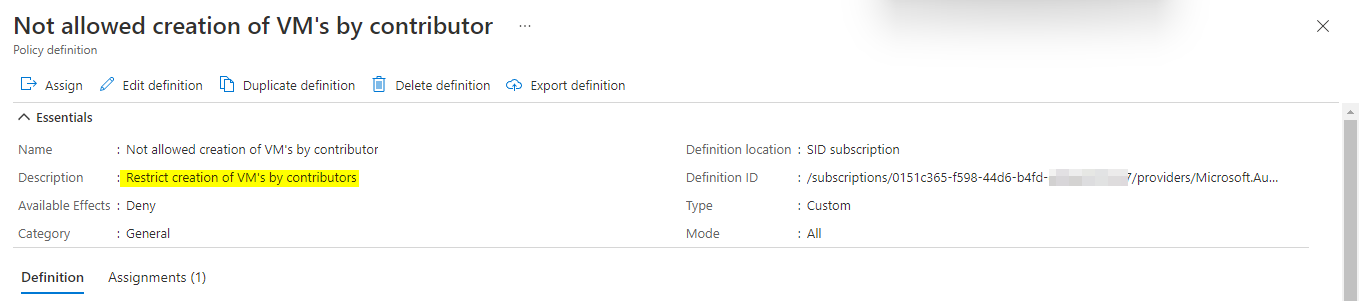
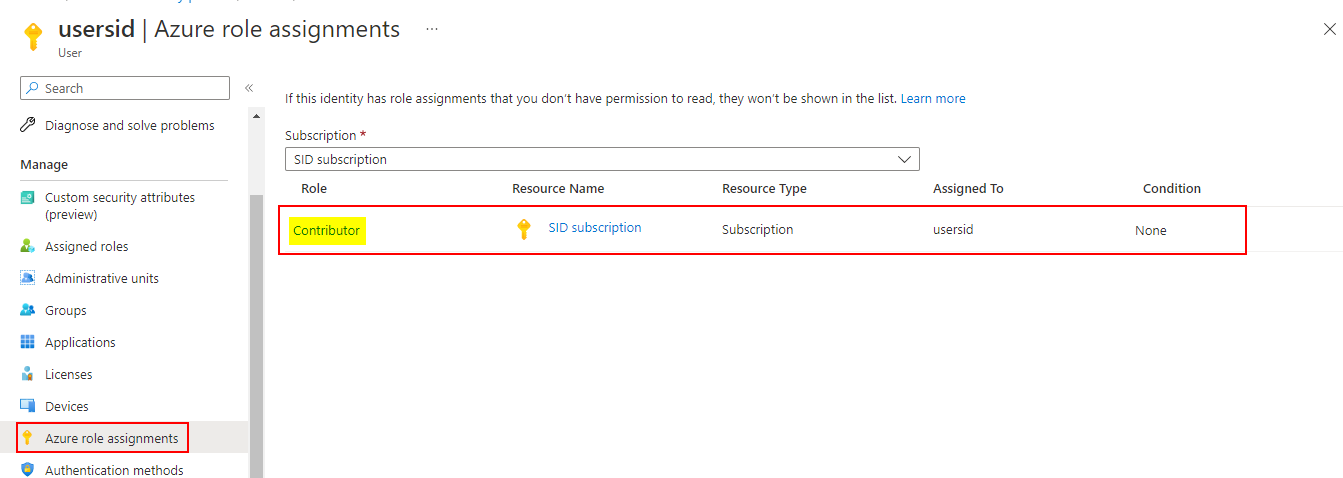
I have one user with Contributor role like below:
Now, when the user with Contributor role tried to create a VM, the VM creation was disallowed by the Policy like below: