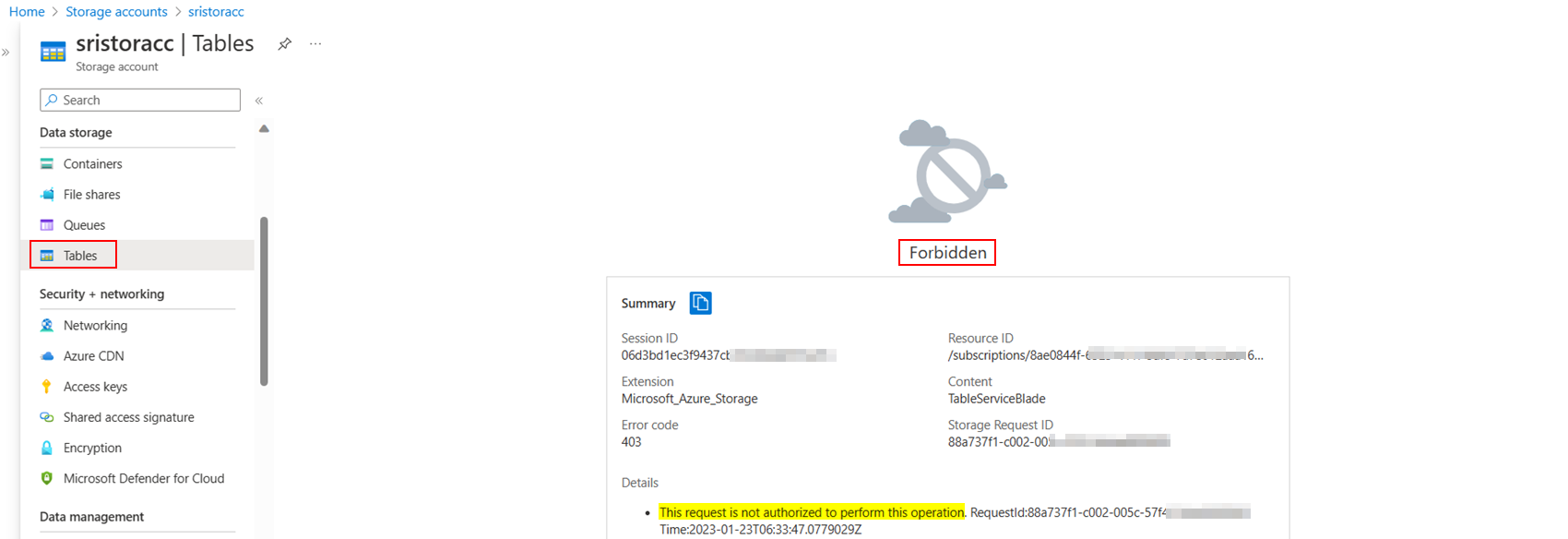
I am receiving an Access Forbidden message when I attempt to access an Azure storage table that I created in Pulumi.
I have tried accessing the storage table in the Azure portal and in Azure Storage Explorer.
{"odata.error":{"code":"AuthenticationFailed","message":{"lang":"en-US","value":"Server failed to authenticate the request. Make sure the value of Authorization header is formed correctly including the signature.\nRequestId:XXXXXXXX-XXXX-XXXX-XXXX-XXXXXXXXXXXX\nTime:2023-01-20T23:21:57.8113163Z"}}}
The following code does not resolve the access forbidden issue:
var sas = Pulumi.Azure.Storage.GetAccountSAS.Invoke(new()
{
ConnectionString = storageAccount.PrimaryConnectionString,
HttpsOnly = true,
SignedVersion = "2017-07-29",
ResourceTypes = new Pulumi.Azure.Storage.Inputs.GetAccountSASResourceTypesInputArgs
{
Service = true,
Container = true,
Object = false,
},
Services = new Pulumi.Azure.Storage.Inputs.GetAccountSASServicesInputArgs
{
Blob = true,
Queue = true,
Table = true,
File = true,
},
Start = DateTime.Now.ToString("yyyy-MM-ddTHH:mm:ssK"),
Expiry = DateTime.Now.AddYears(1).ToString("yyyy-MM-ddTHH:mm:ssK"),
Permissions = new Pulumi.Azure.Storage.Inputs.GetAccountSASPermissionsInputArgs
{
Read = true,
Write = true,
Delete = false,
List = true,
Add = true,
Create = true,
Update = true,
Process = true,
Tag = true,
Filter = true
},
});
Update:
I'm researching how to use an 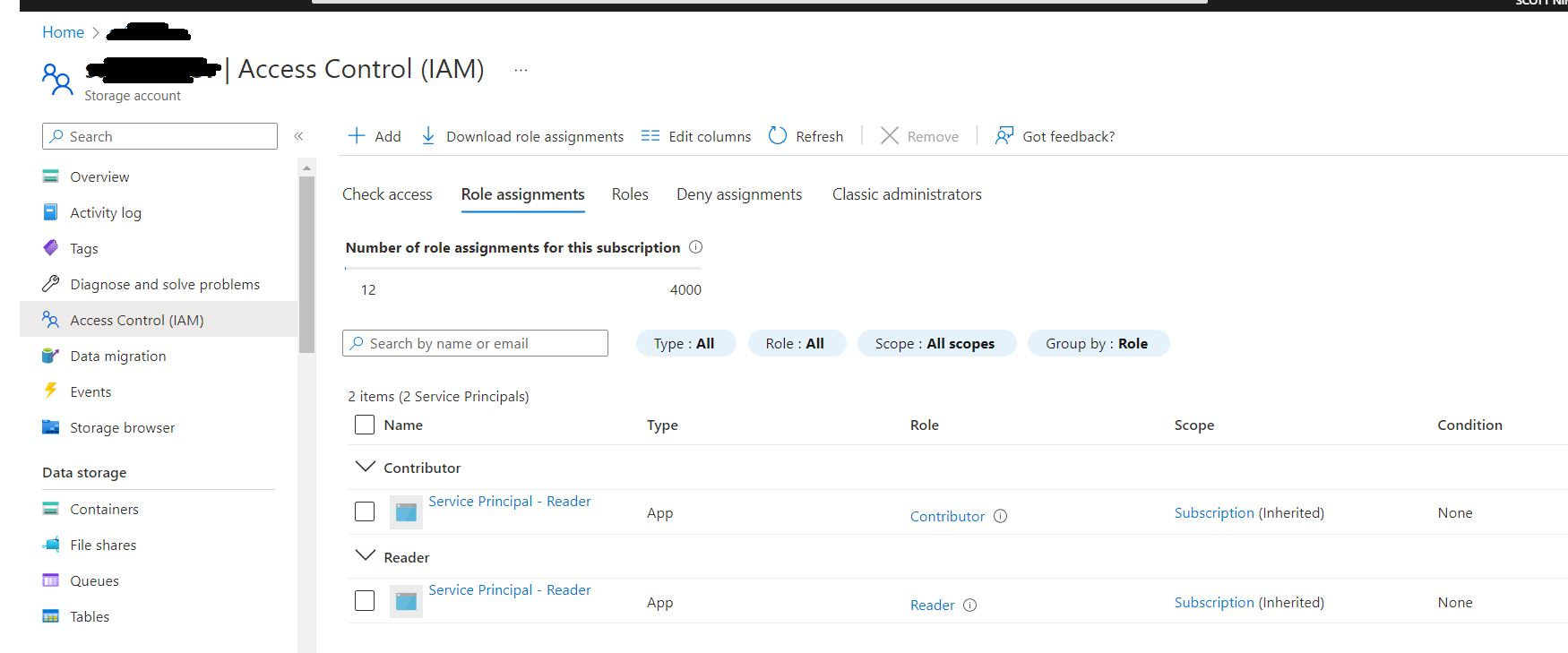
CodePudding user response:
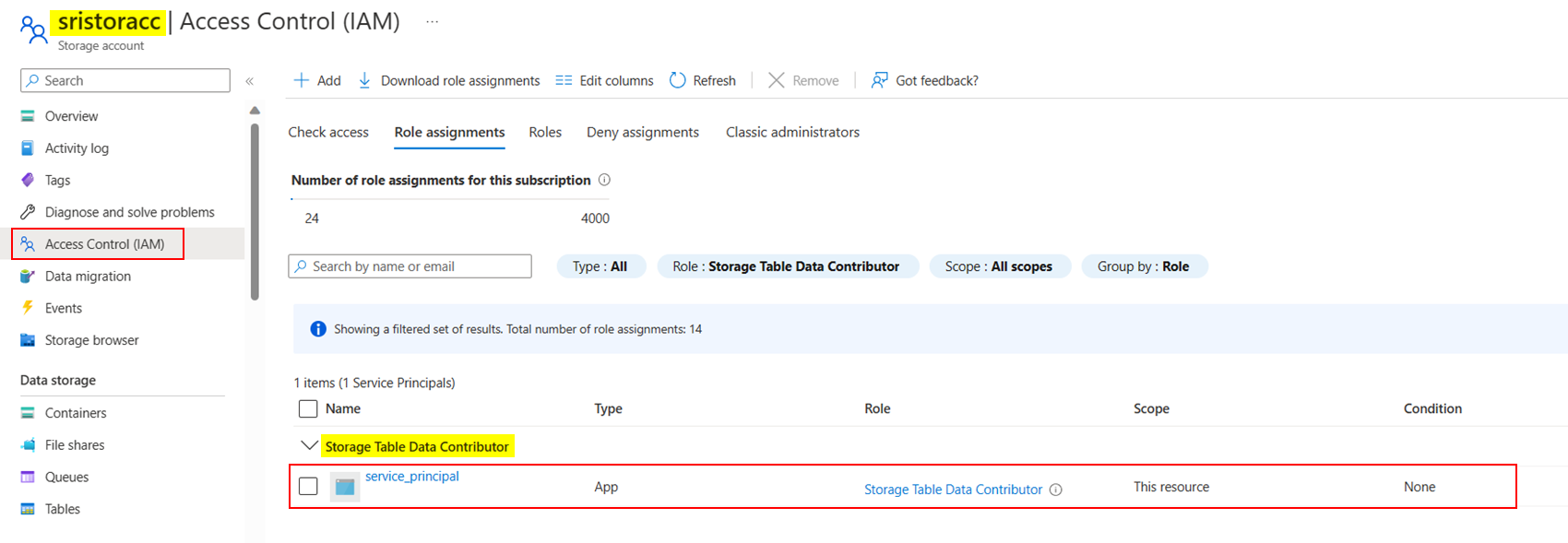
I agree with @Gaurav Mantri, you need to assign Storage Table Data Contributor role to your Service Principal.
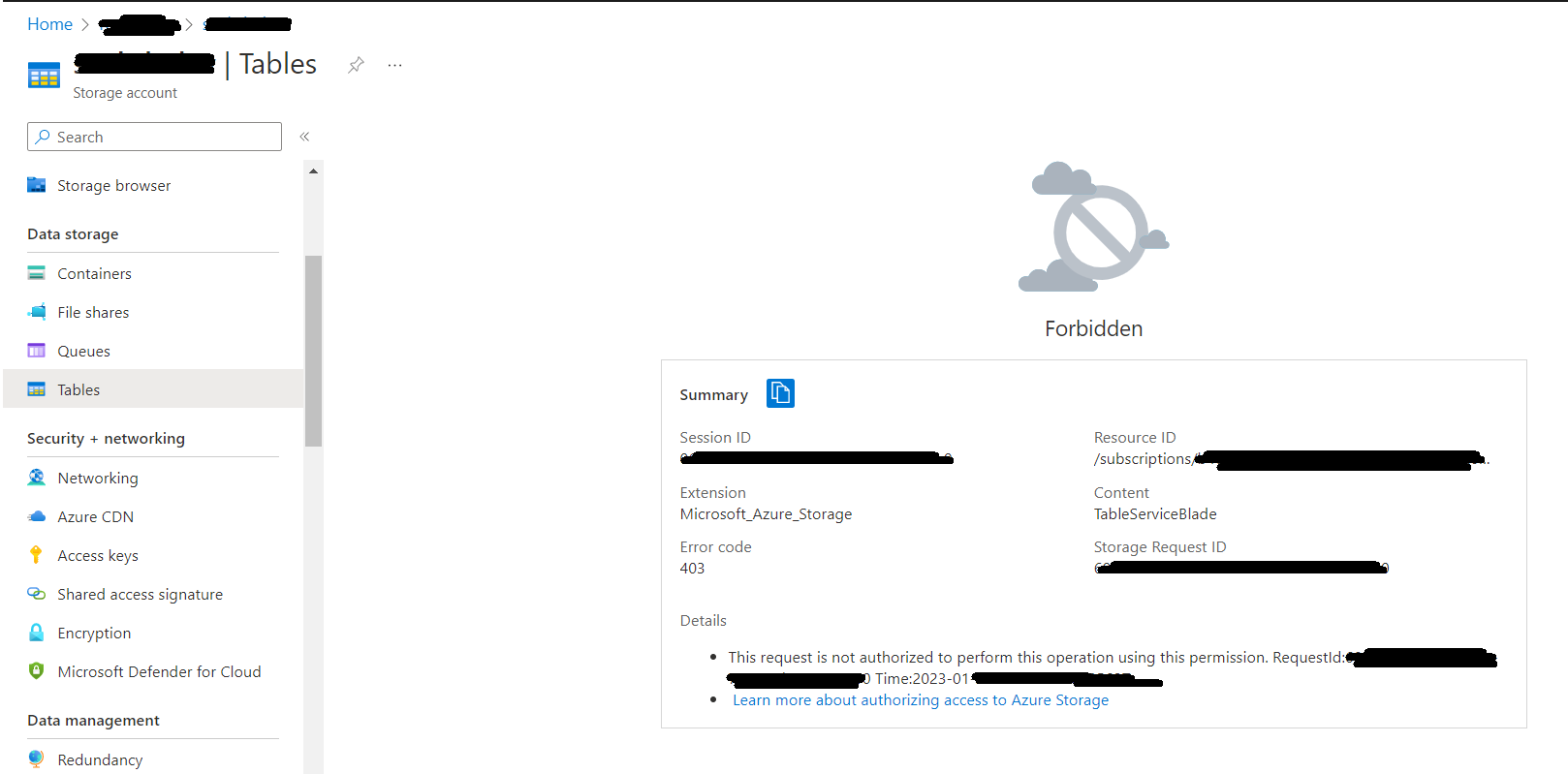
I tried to reproduce the same in my environment and got same error like below:
To resolve the error, you need to assign Storage Table Data Contributor role to your service principal as below:
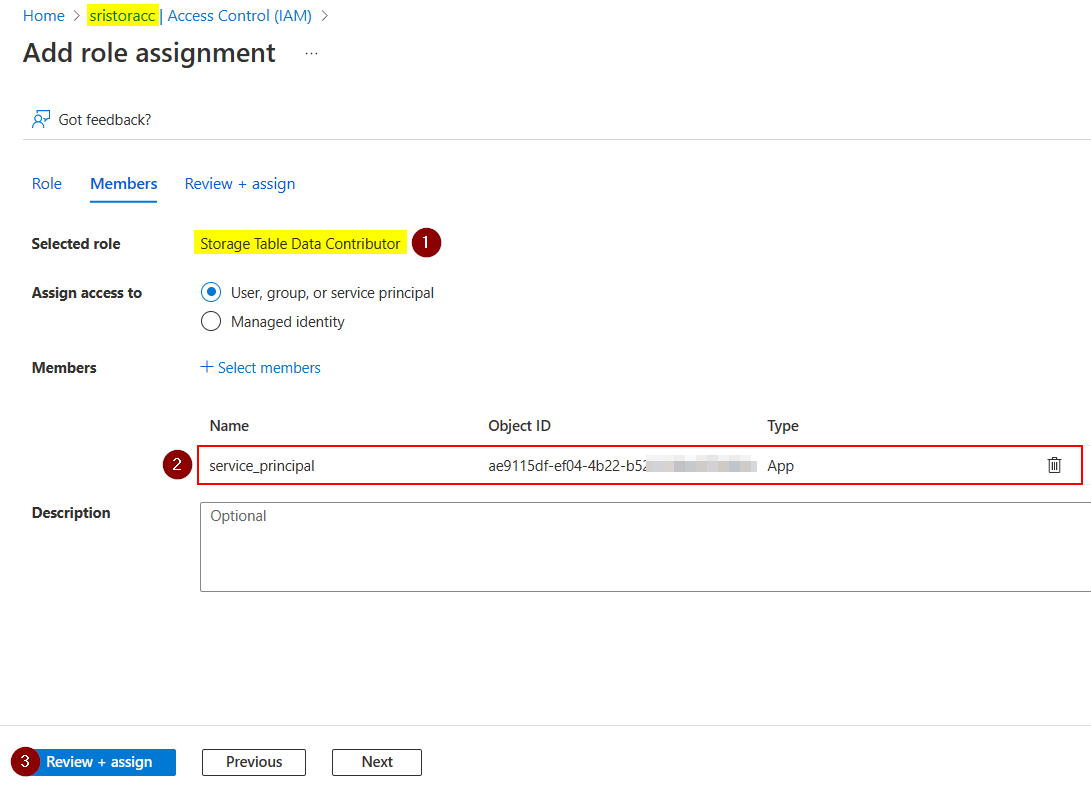
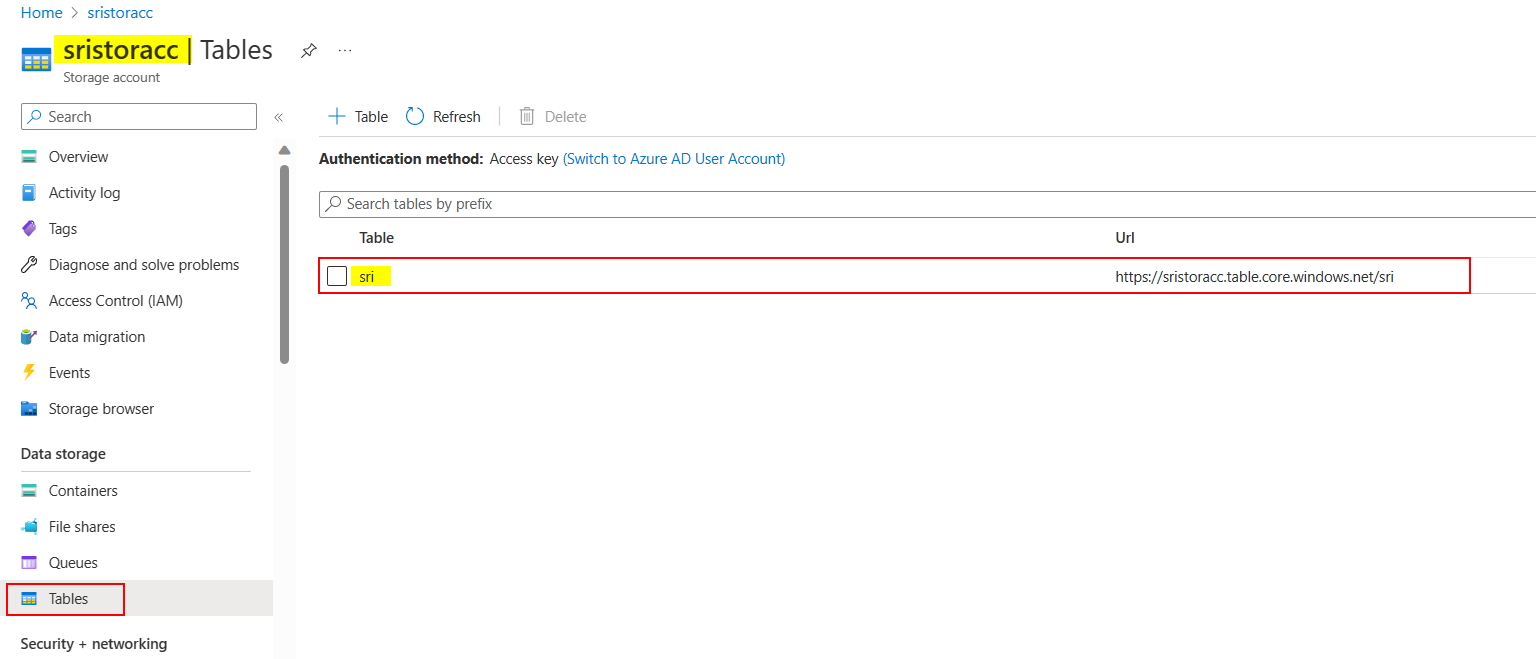
After assigning Storage Table Data Contributor role to my account, I'm able to access the tables successfully like below:
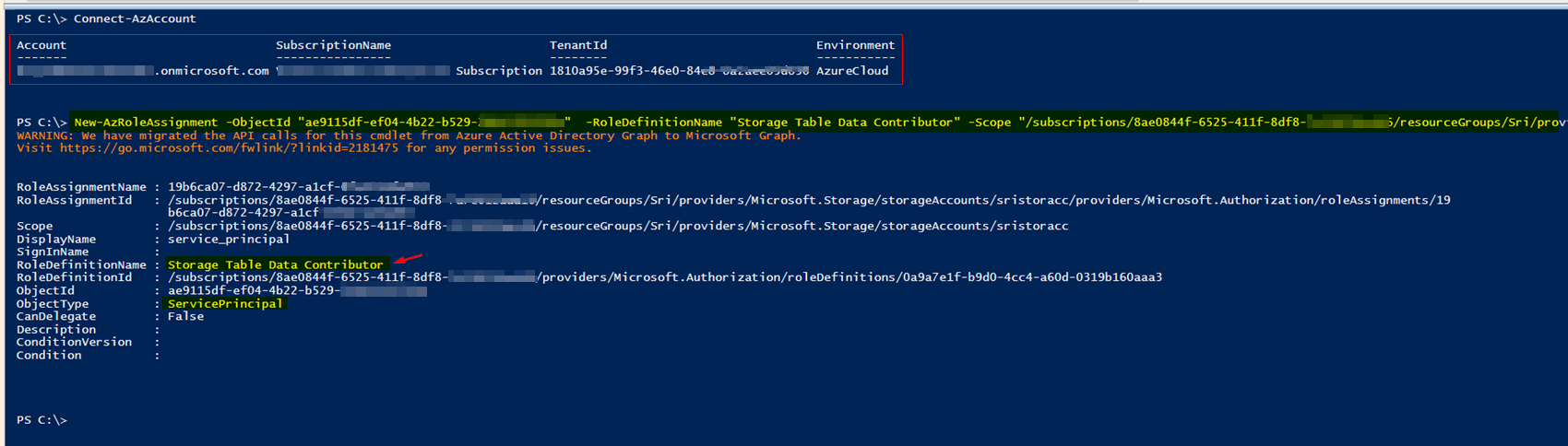
To assign this role programmatically (without using the Azure portal), you can make use of below commands:
PowerShell:
Connect-AzAccount
New-AzRoleAssignment -ObjectId <sp_objectID> -RoleDefinitionName "Storage Table Data Contributor" -Scope "/subscriptions/<subscriptionID>/resourceGroups/<rgname>/providers/Microsoft.Storage/storageAccounts/<account_name>"
Response:
CLI:
az login
az role assignment create --assignee <sp_objectID> --role "Storage Table Data Contributor" --scope "/subscriptions/<subscriptionID>/resourceGroups/<rgname>/providers/Microsoft.Storage/storageAccounts/<account_name>"
Response:
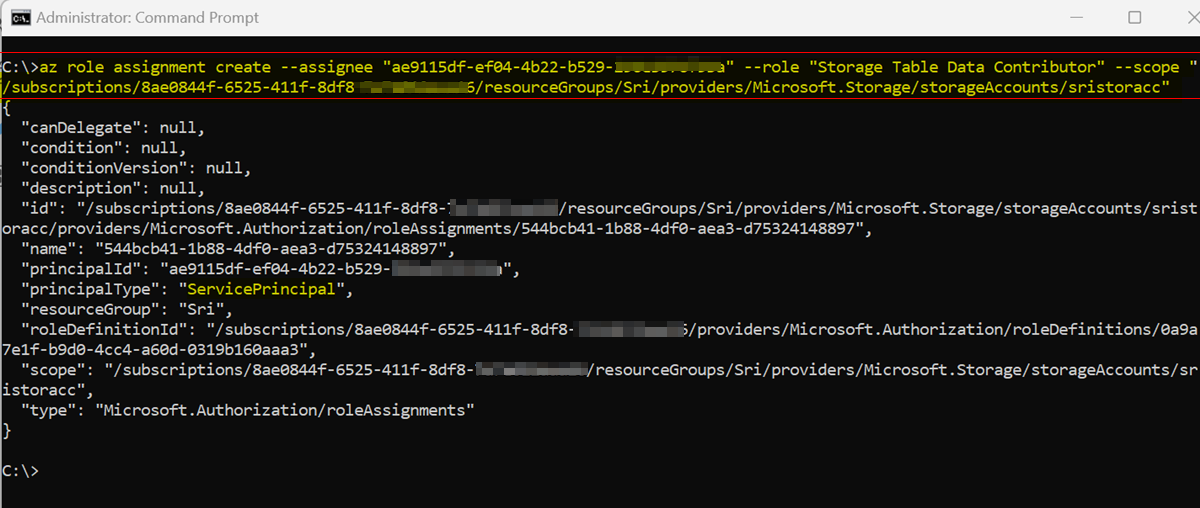
When I checked Portal, role is assigned to service principal successfully under storage account like below: