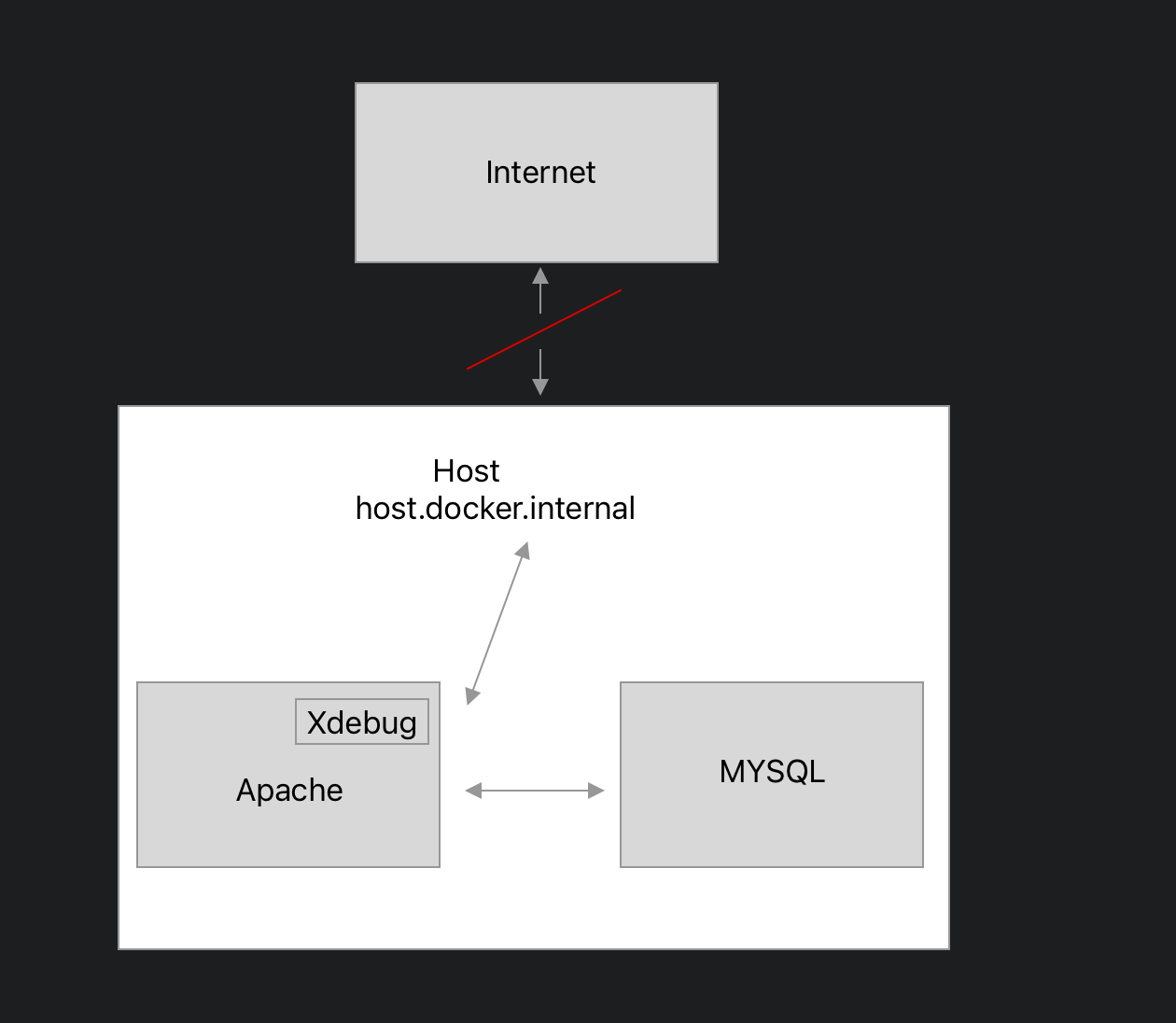
How do I setup my Docker networks to allow only internal and host access?
I have been using a user-defined network to prevent my containers from accessing the internet.
networks:
no-internet:
internal: true
ipam:
config:
- subnet: 172.19.0.0/16
This works great. However, I would like to allow my containers to connect to the host so that I can use XDebug. If I use the default Docker network, I can setup Xdebug to connect to the host via host.docker.internal. Once I add the containers to the no-internet user-defined network, the containers lose access to the host.
CodePudding user response:
I have no idea what XDebug is, so I might be totally wrong; but my intuition is that this is an easy case.
Put Xdebug in a container on the no-internet network.
CodePudding user response:
Instead of setting internal, when creating your user defined networks, set com.docker.network.bridge.enable_ip_masquerade=false. That would prevent NAT masquerading outbound traffic from that particular network (which is how Docker connects containers to the host network when using IPv4).
The following is how you'd do it with the docker-cli.
docker network create --subnet 172.19.0.0/16 \
-o com.docker.network.bridge.enable_ip_masquerade=false \
-o com.docker.network.bridge.name=nointernet \
nointernet
And this is what it would look like in with Docker Compose
networks:
front:
driver: bridge
driver_opts:
com.docker.network.bridge.enable_ip_masquerade: 'false'
ipam:
driver: default
config:
- subnet: 172.19.0.0/16