I am getting my head around the logs in Azure, and particularly the logs I get from ADSL Gen2 data lake. It is really true that I can't get the login / userid for the changes to the data lake?
I have these fields
TenantId TimeGenerated [UTC] AccountName Location Protocol OperationName AuthenticationType StatusCode StatusText DurationMs ServerLatencyMs Uri CallerIpAddress CorrelationId SchemaVersion OperationVersion AuthenticationHash UserAgentHeader ClientRequestId Etag ServiceType RequestHeaderSize ResponseHeaderSize LastModifiedTime [UTC] Category TlsVersion SourceSystem Type _ResourceId
AuthenticationType is just called AccountKey
CallerIpAddress is the IP address of the user
But the userID like [email protected] or similar is what I am looking for. So how do I include 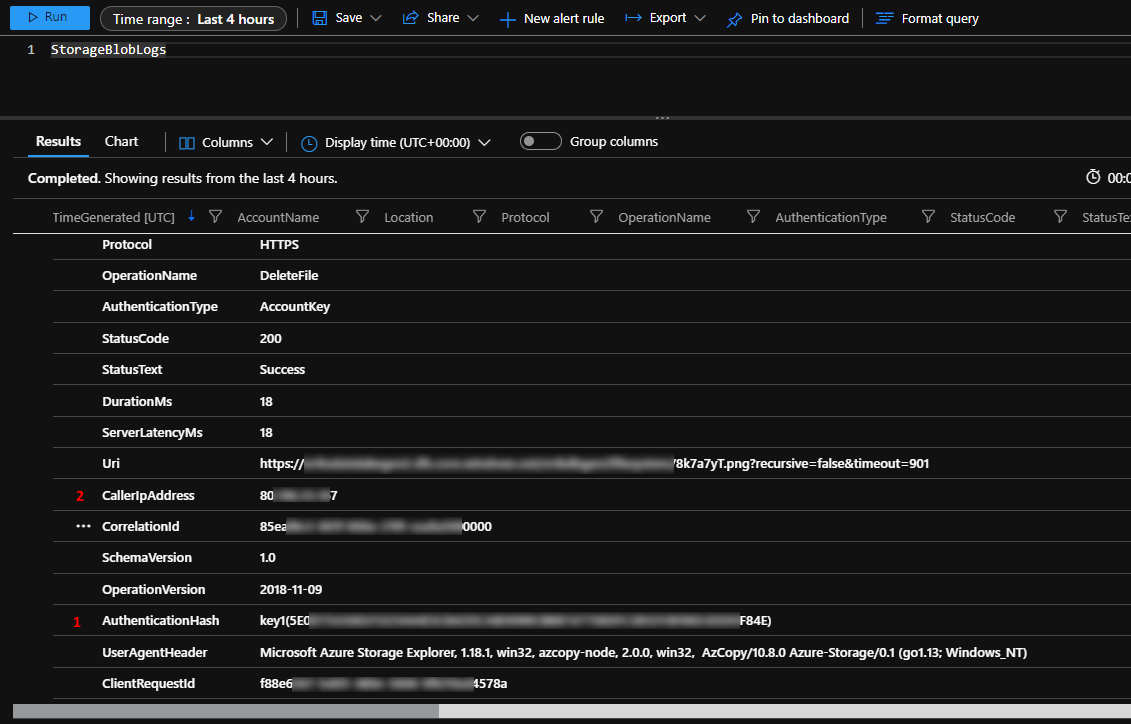
CodePudding user response:
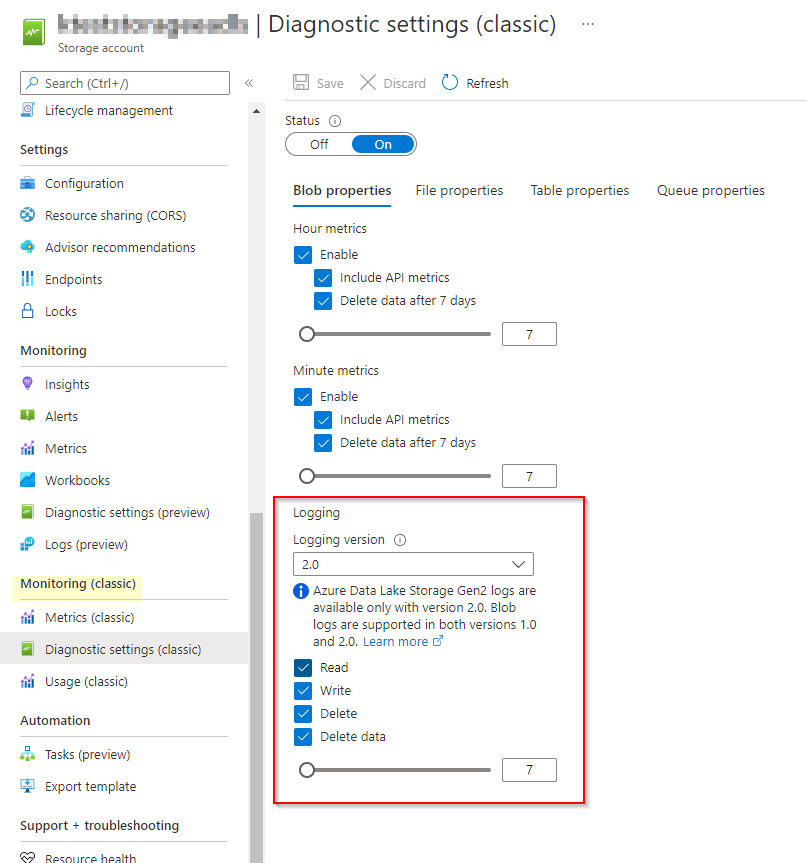
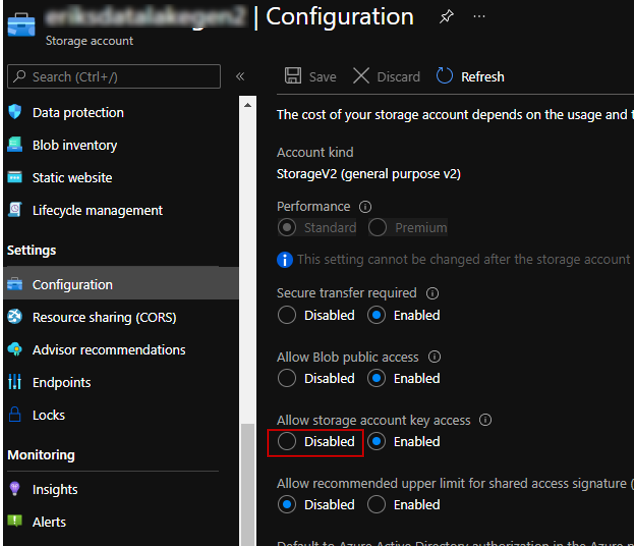
If you have turned on the below specifics in ADLS account
Optionally route if needed
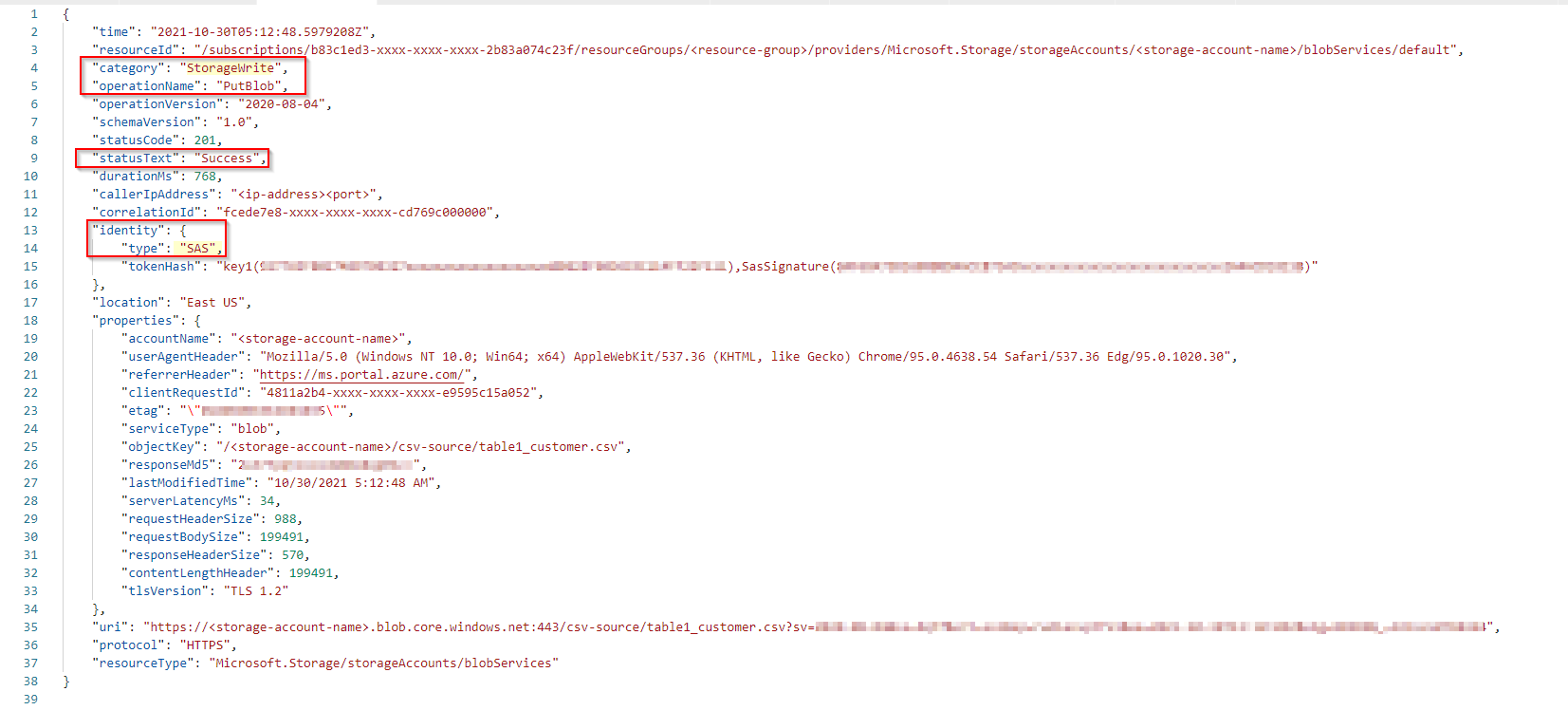
I can see from the logs in the storage about ADLS now.
A sample record containing upn. You can find it at identity.upn where OAuth is the authorization used, which is supported Version 2.0 of Storage Analytics logging.
{
"time": "2021-10-30T05:12:17.3923930Z",
"resourceId": "/subscriptions/<Subscription-id>/resourceGroups/<resource-group-name>/providers/Microsoft.Storage/storageAccounts/<storage-account-name>/blobServices/default",
"category": "StorageRead",
"operationName": "GetBlobServiceProperties",
"operationVersion": "2020-08-04",
"schemaVersion": "1.0",
"statusCode": 200,
"statusText": "Success",
"durationMs": 712,
"callerIpAddress": "<ip-address><port>",
"correlationId": "fced83b0-xxxx-xxxx-xxxx-cd769c000000",
"identity": {
"type": "OAuth",
"tokenHash": "E098F823BC1BE1D9AC73F22F82xxxxxxxxxxxxxxxxxxxx5537E013A5E6BDF71E",
"requester": {
"appId": "691458b9-xxxx-xxxx-xxxx-ed83a7f1b41c",
"audience": "https://storage.azure.com/",
"objectId": "b1c5060f-xxxx-xxxx-xxxx-31cce61160f4",
"tenantId": "72f988bf-xxxx-xxxx-xxxx-2d7cd011db47",
"tokenIssuer": "https://sts.windows.net/72f988bf-xxxx-xxxx-xxxx-2d7cd011db47/",
"upn": "[email protected]"
}
},
"location": "East US",
"properties": {
"accountName": "<storage-account-name>",
"userAgentHeader": "Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/95.0.4638.54 Safari/537.36 Edg/95.0.1020.30",
"serviceType": "blob",
"objectKey": "/<storage-account-name>",
"serverLatencyMs": 711,
"requestHeaderSize": 2713,
"responseHeaderSize": 282,
"responseBodySize": 802,
"tlsVersion": "TLS 1.2"
},
"uri": "https://<storage-account-name>.blob.core.windows.net:443/?restype=service&comp=properties&_=1635xxxx35961",
"protocol": "HTTPS",
"resourceType": "Microsoft.Storage/storageAccounts/blobServices"
}
CodePudding user response:
Once I had sat Allow storage account key access to Disabled. I had OAuth on every StorageRead, StorageWrite, StorageDelete