I created a simple chatting client program to communicate with the server.
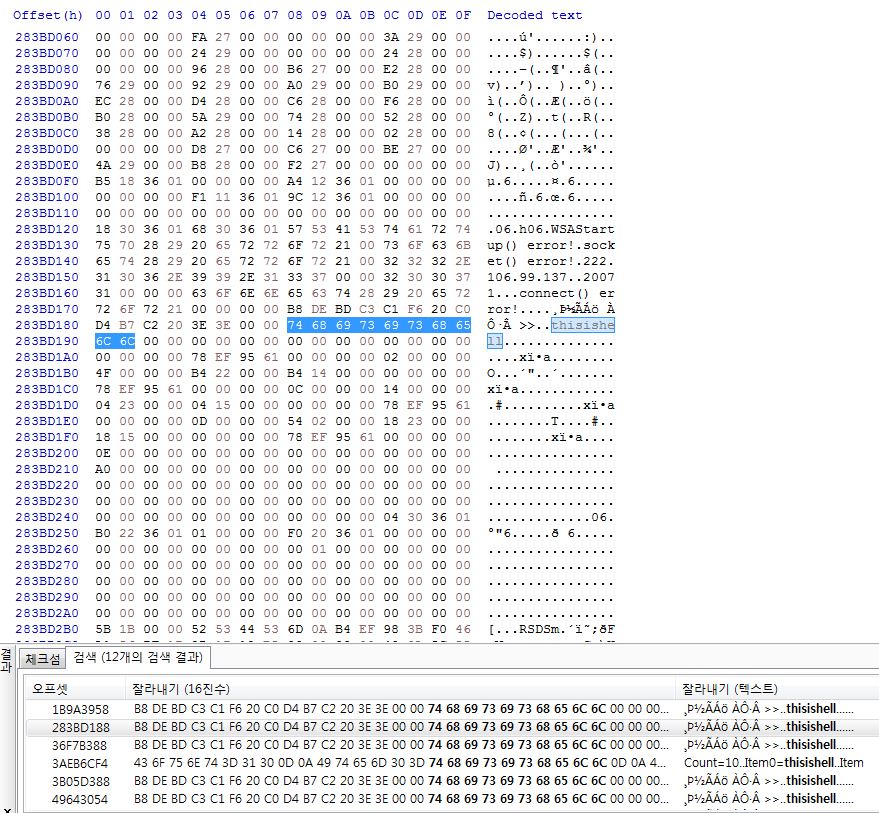
After the client sent data to the server using the send() function, the data was initialized to memset (buf, 0x00, sizeof(buf)), but after searching OS memory through Dumpit, there are still traces of data sent somewhere. How can i clear send data?
int main() {
WSADATA wsaData;
SOCKET hSocket;
SOCKADDR_IN servAddr;
char message[30];
char tmp[8];
int strLen;
memset(tmp, 0x00, 8);
if (WSAStartup(MAKEWORD(2, 2), &wsaData) != 0)
ErrorHandling("WSAStartup() error!");
hSocket = socket(PF_INET, SOCK_STREAM, 0);
if (hSocket == INVALID_SOCKET)
ErrorHandling("socket() error!");
memset(&servAddr, 0, sizeof(servAddr));
servAddr.sin_family = AF_INET;
servAddr.sin_addr.s_addr = inet_addr("222.106.99.137");
servAddr.sin_port = htons(atoi("20071"));
if (connect(hSocket, (SOCKADDR*)&servAddr, sizeof(servAddr)) == SOCKET_ERROR)
ErrorHandling("connect() error!");
memcpy(tmp, "thisishell", 7);
sendto(hSocket, tmp, strlen(tmp) 1, 0,
(struct sockaddr*)&servAddr, sizeof(servAddr));
memset(tmp, 0x00, 8);
memset(tmp, 0xFF, 8);
memset(tmp, 0x00, 8);
closesocket(hSocket);
WSACleanup();
return 0;
}
CodePudding user response:
Your binary program code still contains the string literal thisishell. Most likely, that's what you're seeing, because your other string literals like "connect() error!" can be seen right above it in memory.
CodePudding user response:
it is normal that it is difficult for you to clear, but you can block attacks encrypt and read the following articles
this is called Buffer overflow in cybersecurity to prevent Buffer overflow, developers of C/C applications should avoid standard library functions without border control, such as gets, scanf, and strcpy.
In addition, secure development applications should october regular tests to detect and correct buffer overflows. The most reliable way to prevent or protect against buffer overflows is to use automatic protection at the language level. Another way is a timely boundary check, which automatically checks that the data written to a buffer is within acceptable limits, preventing buffer overflow. hackers exploit this vulnerability and take the data, so a hacker can take the data by making an attack. if you did this in c , you can block it like this: In order to avoid buffer overflow, developers of C/C applications should avoid standard library functions without boundary control, such as gets, scanf, and strcpy. In addition, secure development applications should october regular tests to detect and correct buffer overflows. The most reliable way to prevent or protect against buffer overflows is to use automatic protection at the language level. Another way is a timely boundary check, which automatically checks that the data written to a buffer is within acceptable limits, preventing buffer overflow. apply the same algorithm to the program if you did it with python vs vs.
