
Technology entrepreneurship veterans after mason, 70, worked in large domestic zte communications enterprises for 17 years, from the beginning to the end to witness the rise and fall of the whole communication industry and Internet industry, this caused me a thinking, we need to have eyes to see trends, only in this way, can we seize the opportunities of The Times, otherwise, it's always go with the flow, by fate,
Case model outline:
1, the company introduced and entrepreneurial mind
2, what is digital identity
3, solve the market what is pain points
4, why do you want to use digital identity
5, customer group is what target
6, what products and services
7, the market progress and achievement how
8, the mechanism design how to
9, what is core advantages barriers
What is 10, market demand
Company introduction
Well card is based on the well and digital identity infrastructure on the chain, use of chain blocks, decentralized, tamper-resistant features, using the intelligent contracts, IPFS decentralized distributed storage technology, such as to the application of the Internet provide a decentralized trusted digital identity service,
01 entrepreneurial mind
Well the source of this project, is from a true market demand, which are based on block chain exchange user registration, due to regulatory requirements, he will require the user to carry out a real-name authentication, but under the current network architecture, we found that the same person to different blocks chain exchange requires a real-name authentication, it is unnecessary for users, carefully analyse the causes of this problem, actually is not simple,
Causes of this problem, it is derived from the Internet at the beginning of the standards of a problem, they didn't like E-mail protocol, HTTP protocol to define standard about the identity of the person ID like that, thus, causing the should have as the standard for public people identity ID standard monopolized by some companies as a private agreement, this creates problems at present, these companies because have you the identity of the ID, thus easily steal your privacy, and profit in your data, and there is no way that you user abducted by the giant companies,
Then I and well through a few friends are planning to do well the project, the original is that we see this trend, chain blocks and digital identity in the future will be a subversive now Internet architecture, technology of society have a huge change, citizens have a digital identity, to guarantee the means that the following several aspects:
(1) of the citizen's data to get the maximum security; To avoid the personal information is abused, theft;
2. Global digital identity of the user in the future can be Shared, which means that the support of digital identity enterprise can be the introduction of the global digital identity of the user;
3. Pass card issued/points between different enterprises can be more convenient transfer between
4. Based on the application of block chain contracts (such as intelligence, etc.) can be truly fall to the ground, before due to anchor a natural person can only be an armchair strategist,
What is digital identity
The meaning of digital identity is quite widespread, according to the W3C DIDs standard definition of digital identity, digital identity objects including person, organization, object, etc., all said that any individual, organization, Internet of things devices are our potential customers, the digital identity will become an important infrastructure, block chain and intelligent contract will be in the future, and through the technology together to promote traditional Internet to value evolution of the Internet,
02 digital identity in the chain of blocks in the position of the technical architecture
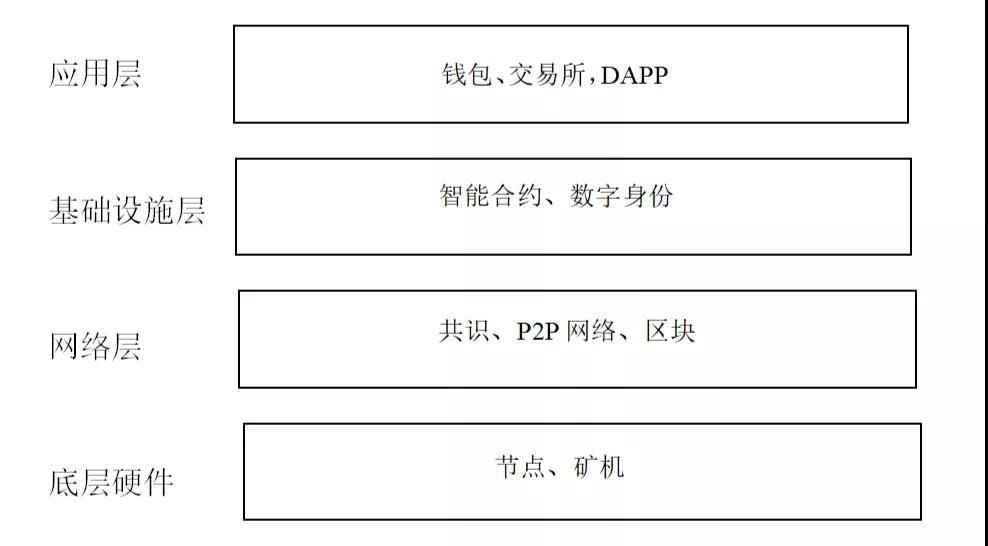
To solve the market pain points
03 mainly solve the problems of the current Internet application cannot solve the
1, the individual user does not have its own identity, resulting in the Internet privacy, data theft and abuse can be seen everywhere.
2, the giant company with possession of user data, thus by controlling the user interests and steal the user data acquisition, 3, the Internet giant enterprise business rules have been hold, small and medium-sized enterprises according to the old business model is unsustainable; 4, the lack of digital identity, caused some similar innovative applications such as intelligent contract can't really be born; So well card company background is also on the spot to solve of,
Why use digital identity
04 USES digital identity to the benefits of enterprise:
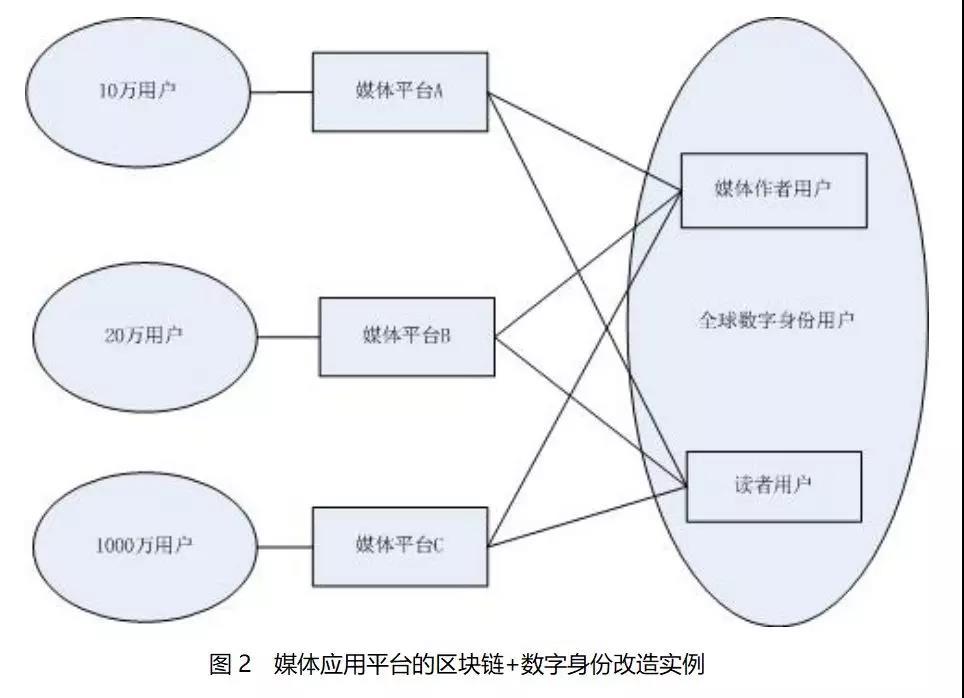
I through a we are operating under the "media + block chain" case to make a brief introduction, using block chain and the benefits of digital identification technology to the media platform enterprise,
Background: there are three media platform
Media platform A, here are 100000 user
Media platform B, there are 200000 user
Media platform C, is a giant company, has 10 million users under
Status: giant monopoly
So if the existing Internet operating mode, there is a problem, is the media platform C can in their own large users of squeeze other platforms living space, a situation caused by the strong stronger, thus forming a monopoly,
Breakthrough: how to break the monopoly of small and medium-sized media
In this case, media platform and media platform B how to solve this dilemma, we put forward A solution, that is:
Media platform A and B can be on the basis of the original user interface, support digital identity well card users access
Doing this there are several advantages, the first for users:
1. The author users, the media was employed digital identity, the author means that media users have their own ID and data, then the media after the author can published an article in your own data area, if the author and the media platform and media platform B has signed A contract, is A key to achieve the author can mass media function, in this way, the author will greatly reduce the workload of media, which have more choice of platform; In his own hands, and because the data can be very convenient for approval,
2. For the readers, can use their well card ID to log in any application, without frequent use various user name and password to log in various applications, and don't have to worry about their privacy, and data from being misappropriated
3, the benefits for the enterprise to:
1) the small and medium-sized enterprises can introduce huge amounts of digital identity of users, can share digital identity of users, to form a coalition;
2) enterprises through the data to the user, through grant access card to the user and integral as incentives, can achieve the goal of enterprise and users are bound to the interests of the win-win;
3) between alliance enterprises through the integration between digital identity user flow, has formed a kind of brand-new business model, so as to break the monopoly of big companies,
Customer group
05 specifically well the typical customers include the following several
1. The Internet APP and DAPP application as long as involving the real-name authentication id will be our potential customers, we will use this part in DAPP and SDK way to call for application,
2. Individuals or organizations need to electronic business licenses issued by the authority or credit reporting and so on other data on a chain,
3. For the enterprise or the organization set up the internal digital identity system based on block chain, to facilitate exchange between enterprises between users,
Products and services
06 well the product category
1, well Jpassword (password management software)
This is one for the average user data rights belong to your own password management software, is designed to help users to manage their many scattered on the application of user name and password, and block chain under all kinds of wallet to the private key and other personal data privacy,
Currently on the market some of the same kind software is through the personal privacy important data saved to a centralized server to achieve, in this way is extremely unsafe for users, and our product advantage is that the data stored in the decentralized IPFS distributed database, the data classified completely user control, security more than similar products on the market,
2, well J - DID
Well pass another product platform (J - DID) role is to provide a decentralized trusted authentication platform, the traditional centralized authentication platform, between each platform are data islands, repeating validation problems, so the effect of J - DID is to build an ownership completely belongs to personal ID, and then the user can based on your own this ID to go to new validation, the future you can use this ID to direct you do cross-platform application, in this way can we truly data and application of separation, break traditional caused by centralized company "data island" phenomenon,
Because we are follow the W3C DIDs standard design, so you can meet the national "* *" personal information is protected and GPDR privacy protection * * issued by the European Union,
Market progress and profitability
07 project is underway in several market
1, telecom SIM card project, telecom is planning to personal digital identity that a do SIM card chip, and later, the user's digital identity can be read from the phone directly, we are currently working to telecom do detailed design,
2, a police project in one district in Shanghai, the project is a convenient service project of police, this? Probably has more than one hundred users, to provide our public security convenient service for these users, such as identity card, hu kou book, such as remote handle query and schedule, and so on, is convenient and reliable and protect the privacy of the individual,
3, media, community projects, before the background of this project have been described in detail in the examples,
Well the profit the company market mainly has several aspects:
1, the company currently has a user-oriented password management software is charging software,
2, hole card for other Internet application decentralized trusted id check function, it will generate profits,
3, the well will be involved in the other enterprises in the construction of digital identity, through the provision of technical, consulting and cooperation method, combined with block chain, through the business model of economy so as to create a conducive to business operation, so as to realize win-win,
The mechanism design
Due to the decentralized authentication this is cooperation and the public security department, we will strictly abide by the compliance requirements and well certificate issued itself does not pass certificate,
However, because no matter any enterprise or individual have access card or integral part of this data, then this part of the data on my digital identity of the following is the most reasonable, so I think in the future in any enterprise or individual will need a digital identity,
Core advantages barriers
09 project core advantage
1. The product concept is advanced, we believe that we will do product to individuals, is conducive to innovation and development of society, also is the development trend of the future;
2. Our project based on many years of experience in commercial and chain operation well SWTC male chain of development, the well tong SWTC similar Libra male chain the same technical architecture, and has stable commercial 5 years, can meet the demand of high concurrency stability,
3. The core team members are in their respective professional fields have profound background of the expert team, so we didn't dare to do this kind of not issuing the ground application,
4. Our institute and China telecom and the Ministry of Public Security is good partners, hole card and power and is deep strategic partnership,
Based on the above reasons, I believe our team can do real ground commercial projects,
Well the relations with well through
10 well with well through the ecological relationship between
Well card is well through ecological chain of a node, is also well through strategic partners, is also the ecological of male scholars chain partners, for the 2 and provide credible authentication service chain,
Future will run across the chain, for the whole Internet application decentralized trusted digital identity service functions,
The market demand
We welcome enterprises to need to use id real-name authentication function in priority and we well cooperation, because under the same circumstances, offer the same authentication service,
If you use other centralized authentication, is equivalent to you give your users the centralized company, and will not cause you any commercial return, and use well, the future will lead to the users and business model returns,
nullnullnullnullnullnullnullnullnullnullnullnullnullnullnull
