I studied with tigers in advance, there are several main points,
First, as the etheric fang issuing function similar to a key in a key to achieve tigers in hair chain functions,
Second, based on the chain to establish different function, different types of chain blocks,
Third, the chain, in the long term likely to be the foundation of next generation network,
It involves a lot of technical problems, we are still please tiger outlining,
Xiao-hu Chen: thank guo-dong zhao teacher, very glad to have the opportunity to share with everybody block chain of some technical practice, our team can be traced back to as early as six years ago, from 2017 onwards, we aimed at the weakness of the existing block chain technology, in our software system, and a deep understanding of block chain technology, for scalable implementation of the commercial block chain chain, put forward the unique design and development plan, at present, it seems, we put forward at the beginning of 2017 the multi-tier architecture, multiple chain system, has become the important direction of current block chain, in the process of communication with other projects, see more and more projects similar to our framework, on one hand, this is a good thing, prove that we have a good prospective, our efforts are correct, and have more than any other project development time, on the other hand also show block chain now is you, not to advance is to go back, there are so many chaser, if we don't work hard, will soon be over,
Here special mention the etheric, etheric lane in the past 3 years, basically do not have to let a person shine at the moment the technology progress, and from now, according to the existing technical progress, in a short period of time also won't have too much of a breakthrough, this is the thing that it is a pity that, in turn, is also our opportunity, in the proposed after we think more advanced architecture and specific implementation is also very challenging, through the untiring efforts of the team, in April 2018 we successfully realized the main online, and then on this basis, expanding, basically achieved the requirements of the white paper, at present, our application is an important direction in the ground, we cooperate with a number of applications has important application value, concentrate, let they can fast, stable, the example here have FileStorm, PAS project, etc., we will introduce the other members of the follow-up,
18) : "extensible block chain and painters practice"
Host: guo-dong zhao
Guo-dong zhao, zhongguancun large data industry association secretary general, the national 1142 project deputy head of the big data strategy, the listed company's new technology, fubon shares, Mr D cloud network of independent directors, members of the ministry of expert database, expert committee, China computer society, big data and records, a think-tank, director of pangu think-tank, the originator and academic committee member, Beijing university of posts and telecommunications economic management institute of distinguished teachers, "the historical opportunity of the era of large data", "Internet industry", "digital ecological theory", "block chain world", "block chain and big data" to the author,
Share the guests: xiao-hu Chen
Distributors introduction:
Xiao-hu Chen: MOAC (stone) chain founder, CEO, zhejiang university, bachelor's, master's, master of the university of California; Silicon valley 18 years experience in software development and management; Jointly founded several start-ups; 2012 to participate in block chain technology research and development, the well block chain underlying technology initiated and one of the promoters; Launched in 2017, the male scholars chain, pioneered many chain layered shard architecture; Good at algorithm, software architecture, with special insight and vision; Submitted more than 30 patents in block chain technology,
The first part of
System chain and chain applications,
Next, I'll be a little bit about the specific architecture, we also is the main content of today,
Give you look at a map first,
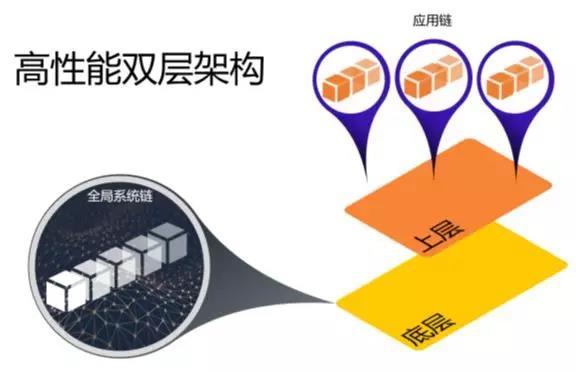
This is our double layer architecture, originally called mother and child chain architecture, then used party think birdcall chain is not tall, so now renamed system chain and chain applications,
The double layer structure has several special place:
Life cycle of the application chain is controlled by intelligent system chain contract, this rather then to apply chain provides a decentralized the role of "god", this concept is very important, because for a block chain, chain block initialization, credible random Numbers, and trusted private key exchange, etc., all need such a role, if there is no a decentralized, many systems can only make do with centralized, here, the latter can provide a system of chain programmable decentralized "god", it is very useful, give you to look at another figure,
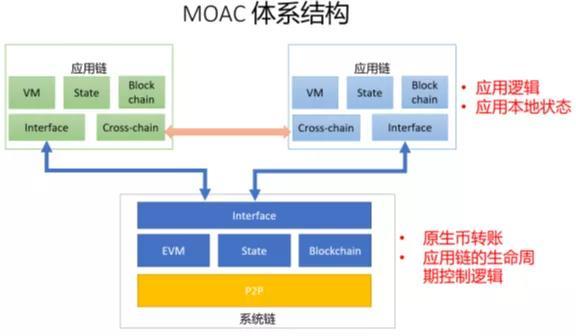
Here is the place where the second special,
This architecture defines an application of chain and chain system, as well as the application of chain and chain application communications between generic framework, makes the application chain has powerful function, at the same time can be "a key chain hair" rapid deployment,
Here also is worth mentioning that the application can periodically will block the hash chain to refresh the record to the system of chain, rather then use system chain anchor application chain eventually sex, add, a key chain, mainly for simple application of standardization, it was a bit of propaganda in the inside, even if there is no such application chain eventually, such as POW, POR, also is the final, in addition, because the system chain chain safer than application, usually such anchor, can greatly enhance the security of application of chain, and thus derived some additional functionality, such as flat block chain, etc., for example, for example for the application of the storage capacity is small chain nodes, can be after the refresh, the history you don't need to delete, as long as a small amount of node records all of history, the practice, is very useful for IOT node, the double deck structure, is very interesting, like DC/EP, can reform already, don't upset the existing pattern,
We have completed the application method of chain of consensus, which is based on such a logic, application is varied, not by a consensus way to support all applications, and as a result, we put forward several different consensus model supply with choice:
The first is the rapid application chain ProcWind contract, can be thought of as a general processor,
The second is the chain FileStorm decentralized storage application, can be regarded as a decentralized file storage system,
The third is the application of random Numbers, chain RandDrop may be regarded as a dedicated processors,
The fourth is the iot application solutions IOTMist,
Especially for small iot node capacity (including storage, CPU, memory), the characteristics of using the multilayer (& gt; 2) structure, the application of chain chain chain system can be used as the upper application, thus to build a tree block chain system, Internet of special needs,
In front of the three has been implemented, the last one is still in development,
Fourth special point is that we can according to different consensus agreement which build a variety of applications,
More importantly, an application can use multiple application chain to meet the demand,
Due to the aforementioned unified framework, so an application can use at the same time the application of two different chain ProcWind and Filestorm, realize the application logic and data storage of decentralization, the Internet of things the 4 layer can be vertical, such application, in the future mass users and their control based on mass data, this framework is very appropriate, can accommodate 1 billion nodes, think about modern digital city,
For applications, reduce the user's entry is very important, the existing chain block access actually not friendly, the most common is based on the application of intelligent contracts, the user at the time of any function call, you had to spend a certain amount of gas, so that either the user have a certain amount of token in advance, or application to potential users automatically top-up beforehand, is very troublesome, the realization of the application of chain locations can do not need to use token, so to avoid the problem of the user's entry, but the underlying system chain through the control of resources, can avoid the malicious user application chain sybil attack, said don't want a token for users, our application chain is complete,
The second part of
The underlying system chain
Then I want to mention the underlying system chain, just talked about, apply chain can have a variety of consensus, and there may be many instances of application of chain, the chain must be a sufficient safety and decentralized chain, can afford to support a large number of applications of the above, the underlying male scholars chain with the method of POW, meet the requirements of this because we think currently only POW, adopt similar to the etheric lane of POW GPU dig, but all of the POW and chain has a problem, the oldest of all is if you are not a homogenous POW you vulnerable to attacks 51%, particular way is a short period of time, from other homogeneous POW network rent a large number of work force, to attack target POW and chain, then out again, the rent for a short period of time cost is very low, actually surprisingly low, then as a small force of the POW and chain, we must solve this problem, that sounds like the etc was attacked, so yes, give you to look at a map,
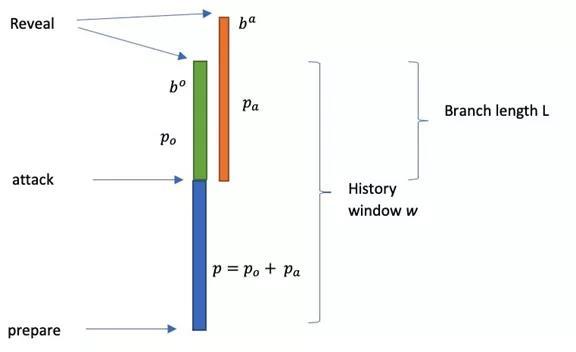
This is our solution, and the concrete practice, we creatively, by considering the weight of history POW, English is POW - HWD, the working principle of this solution is to use: honest node will continue to dig, dig and the attacker just willing to consume a certain resources to a short time, therefore, under the condition of considering the contribution to the history, can reduce the influence of the sudden influx of large work force,
Under the proper history window parameter configuration, we can put the increase in the cost of the attacker - 1000 times, 100 times, small work force of the chain of POW also can significantly improve the ability to resist attacks, relevant content we have published in July in IEEE blockchain conference,
The third part
Some consensus plan summary
Finally, I give a new dry again, this is my some summary of existing consensus scheme, is an exploration for the future development direction of locations, are not open before, here are Shared, everyone look at this chart,
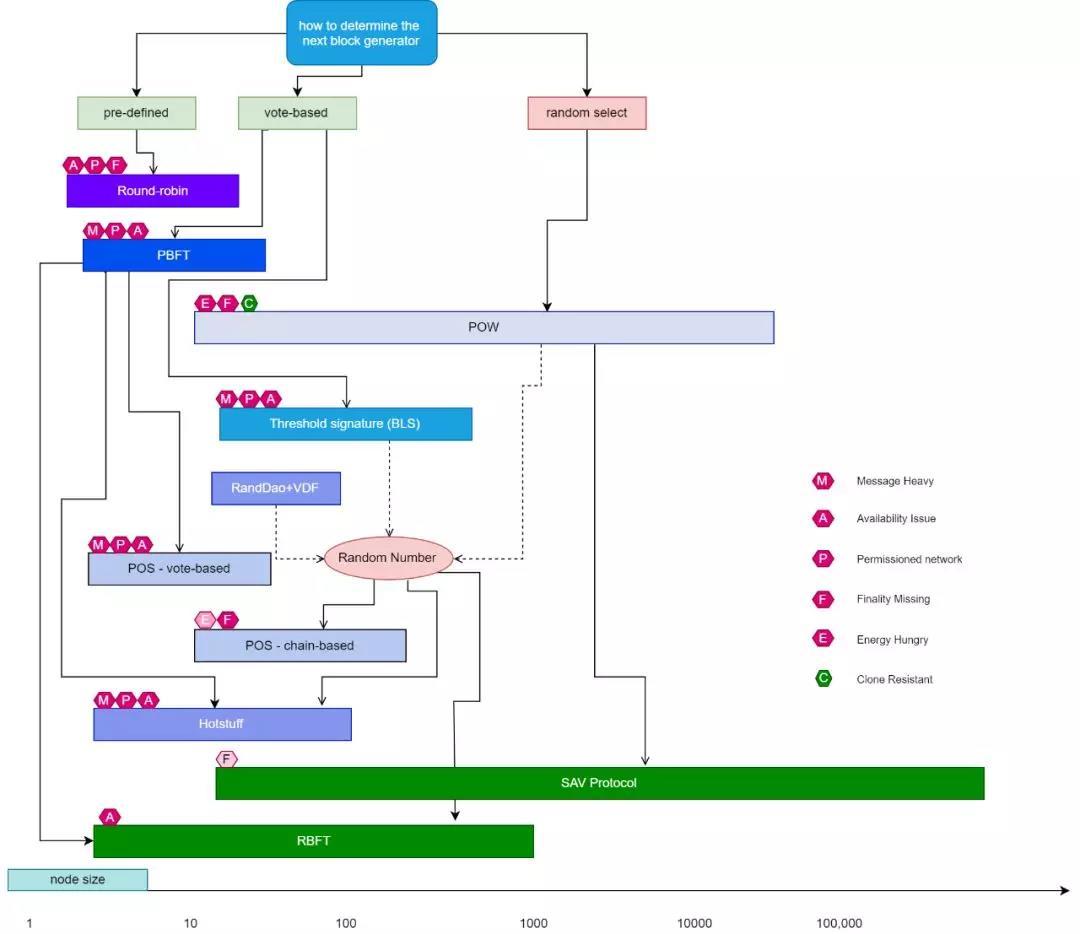
Basically all block chain consensus agreement, a fundamental problem, need to be solved is how to decide who can produce the next block, can be a god to choose, or take a piece of, or vote to select, or is randomly selected, choose a different way, it corresponds to the different characteristics, also corresponds to the different function, become a different chain, for example PBFT, problem is the message volume is too big, admissions requirements, online rate problem, problem of POW is the consumption of energy, without end, have a good feature but POW is resistant to copy, because the work force is the physical requirements of POW, cannot copy more at the same time, for POS, it is easy to copy another, in this figure, one of the most important information is different protocols can apply the number of nodes, at present, the most support node number, also is the most decentralized is POW, you to look at the down to the agreement of two green, one is RBFT, this is one of the goals, we hope is to be able to transcend Libra Hotstuff agreement,
In this layer system chains, can combine pow + pos at the same time, the other is SAV Protocol, this is the direction of future development, we hope it can support more than millions of nodes, and do not need to consume too much energy, this figure we can experience, I am here today's speech, thank you,
The fourth part
Interaction link
Guo-dong zhao: hard tiger, thanks for sharing tiger, do not be technology feast,
Guo-dong zhao: you have what problem, can ask open ha, don't miss the chance of a silicon valley and Daniel directly play,
Guo-dong zhao: with Wells have been online, at any time,
Well: pioneering layered architecture, the application of chain here, the shard, and implements the atom cross chain, than the cosmos and pokadat implement first,
Group of friends: question 1: RBFT have improved on the fault tolerance?
Xiao-hu Chen: answer question 1: there is a lot of improvement, but also can solve the problem of access the Libra and node number,
YanYang: question 2: at present, the layered architecture can use several technical indicators reflect the performance of it?
Xiao-hu Chen: answer question 2: there are two kinds of layered architecture extension, horizontal extension and vertical scaling, vertical scaling well big speak just now, you can have at most four layer, horizontal scaling is infinite, can support at least 1000 chain, concrete TPS I do not speak, each application chain is a similar to an Ethernet, can support multiple contracts,
Guo-dong zhao: block chain some hot technology at present, there are involved, and the results,
YanYang: question 3: layered architecture embodies the flexibility of the application of it, but sometimes the underlying chain need to update, will increase the complexity of the release?
Xiao-hu Chen: answer question 3: the chain there are a great feature, the application of chain code is chain code are separated and the underlying system, at the bottom of the update does not affect the application of the upper, a bit more extreme, application of chain can be separated from the underlying run separately, but a lot less across the chain and the function of refresh, but amazingly, according to the need, the underlying application chain can be returned, the
Xiao-hu Chen: add, the chain of the application of four kinds of consensus, each with independent code,
Xiao-hu Chen: future allows users to define their own new consensus way,
nullnullnullnullnull
