The original author: Yang xin, le active xiao-hu Chen
Translation translation statement: in this paper, the li vigorously help, translation is completed without the author's audit, if mistakes are found, the reader can message feedback,
[abstract] PoW (effort) is widely used in the agreement, block chain system is used to solve the double cost problem, but if the attacker has more than cut in half the hash work force, then the attacker can double flowers attack attack, or 51% if the hash is strong enough, then attack the cost would be lower, it will block chain poses a great threat to many PoW,
We proposed a technical solution to the miners mining history combined with total calculation difficulty, weight information to alleviate the problem of 51% attack, analysis shows that the use of this new technology, will make the traditional attack increases the cost of two orders of magnitude,
[key words] block chain 51% against mining double flowers against
1.
COINS by this power development in 2009, is the first public ledger system, decentralized since then, many encryption currency, based on the block chain chain block is a protocol for distributed data processing, is used to save a public distributed in P2P network books, transaction data recorded in the blocks, the blocks to form a linked list, each node in the network are stored and maintained a complete copy of the book, without the need for centralized authorization, in the currency based on encrypting of chain blocks, each block contains a block before the hash value, lead to manipulation of insider trading, usually by consensus agreement to ensure that the block chain data integrity between P2P network nodes, the different types of chain blocks, will adopt different consensus agreement,
PoW (effort) is the most commonly used in current encryption based on block chain currency consensus agreement, mainstream block chain, such as COINS and etheric, consensus agreement, is to use the PoW in PoW protocol, each node competition to find a nonce value to generate the hash meet certain conditions, find that the difficulty of a nonce value can be calculated according to the conditions of the hash value, when it finds such a nonce value will generate a block and to the P2P network broadcasting, according to the different types of peer node usually accepts the longest chain or chain of the most difficult to continuously expand chain block, PoW using this mechanism to determine which nodes are eligible to pack a block, this process is also known as the dig,
在这种机制中,计算速度较大(有时称为哈希算力)的节点可以比计算速度较慢的节点更快地计算出nonce值,从而有更高的概率获得打包资格,然而,这种机制有一个缺点:一个自私节点的哈希算力比其余节点哈希算力的总和还要高,就会导致双花问题和自私挖矿,从而危害区块链系统,这通常被称为51%攻击,一些学者已经提出了避免此类攻击的方法,Eyal和Sirer在2014年提出了一个两阶段PoW(2P-PoW)的解决方案,防止了具有巨大哈希算力的矿场的形成,在这个方案中,第二阶段的PoW需要挖矿地址的私钥签名,第二阶段的PoW非常困难,矿池操作者必须向矿工开放这个私钥,以便于比其他节点更快地进行计算,Ruffing et al. 等人在2015年提出了一份合约来惩罚实施双花攻击的攻击者,Solat和Potop-Butucaru在2016年提出了ZeroBlock,在ZeroBlock机制中,要求一个块在块的时间戳之后的特定时间间隔内被对等节点接受,否则该块就会过期无效,这种机制可以防止攻击节点在很长一段时间内进行自私挖掘,J. Bae和H. Lim在2018年提出了一种解决方案,随机选择某一组矿工,让他们有权挖出下一个区块,
In this paper, we propose a weight decided to block chain total difficulty through history of the new solution, the optimized algorithm, a branch of block chain miners if in the previous sections have higher packaging piece rate, it's on the branch block chain have higher total weights of history, the algorithm can make 51% attack financial cost and time cost increased two orders of magnitude,
2.51% and cost
First of all, let's review our 51% attack plot, assuming that the current hash work force is the Po, attackers have stronger hash work force Pa (Pa> Po), and it is through this stronger force of hash is calculated the branch of a hidden Ba, attackers on the two branches for double attack, then the attacker exposed long hidden branch Ba, and make the original branch all the transactions in the Bo is invalid, this is known as 51% of the attack, and the cost of the following:
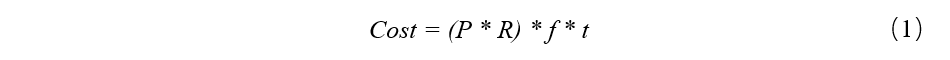
P is the token in the exchange price, R is the piece reward, f is a piece of the generation of the speed, the duration of t on behalf of the attack, do a simplified estimation of the cost, here we assume that the mining token price close to the cost of mining, for many residential block chain, perform such attacks only need hundreds or thousands of dollars,
Another factor is making matters worse, anyone who can pay the right price can easily get hash work force, NiceHash to hash calculate exchange provides an open market, anyone can easily use encryption currency paid rent hash work force in the chain of target block mining, so an attacker can in a short period of time accumulated hash work force for more than 51% of the threshold, the attacker can token by centralized trading pairs of flowers, the entire process takes about 50-500 block, after an attacker can release of hash is rent by force and take profits,
Recently, the etheric lane classic is under attack, attack the branch length of about 50 to 150, a large number of ETC is double flower,
3. The historical weight difficulty
We proposed an improved method of branch always difficult calculation, dig and address this technique takes into account a number of block at the end of the block chain distribution, we call this agreement based on historical weight hard work proof (HWD) - PoW, assuming that in an honest block chain branch, new blocks of miners are likely to be some blocks of miners, before its distribution will reflect the ratio of mining history, and in a malicious block chain branch, new blocks of distribution of miners are likely to be the attacker, this has to do with the regular distribution of miners in the history of different, therefore, when considering the distribution of historical miners, people can easily be honest block chain branch to distinguish malicious block chain branches,
Under this mechanism, in the previous block with less representative branch will be always difficult to calculate weight gain less, therefore, to perform 51% attack, a malicious miners have two choices: either dig a longer branches, or establish miners image in the previous block to build credibility,
Now, let's look at historical weight 51% difficulty is how to defend against:
A) in the first place, in the history window W record every piece of generating frequency for miners:
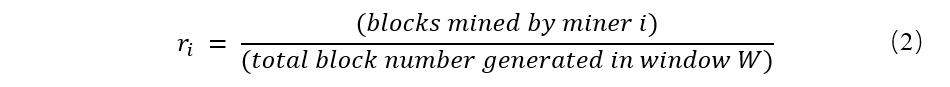
Here:
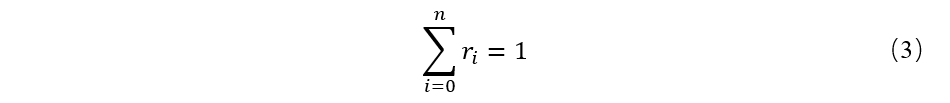
B) then, each block by miners to the private key signature, so that miners will not be able to forge the miners' identity, although this would send a miner's private key; But there are methods to solve, as long as the token is dug, the token from the miners account immediately turn to cold purse,
C) when detected bifurcate crack, through the following method to calculate the weights on each node of the history of each branch difficulty (HWD) :
For K branch of B only miners,
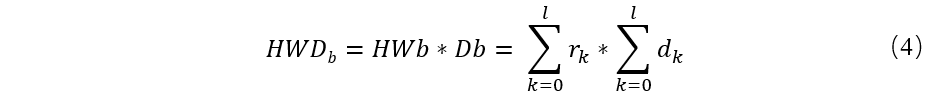
Fairly Rk is history window W in the generation of the frequency, the difficulty of the Dk is a k, L is the length of branch,
Please note that only the frequency calculation for generating a miner, if one address miners mining more pieces, it calculated only once, by inhibiting the single high hash work force of the miners, to encourage the diversified mining, it also increases the difficulty of the attack,
D) each node will compare two different from two branches HWD values, with a higher HWD value of branch will be selected,
The mechanism of the result is clear: if an attacker to add new temporary hash work force, but the new branch of miners is relatively new on the system, the block of ri values will be very low, the corresponding HWD branch will be very small relative to the original, original branch of any node will not switch to the branch of the attacker, this solution can easily prevent "rent" and attach attack,
If an attacker wants to switch to his malicious nodes branches, he will need to produce higher HWD value, the attacker needs to dig in the original branch for a period of time, make oneself contained in history, so when it switch to the hidden branch, its HWD will be higher,
Assume that Pa is the attacker's hash work force, the Po is the original honest hash work force for miners:
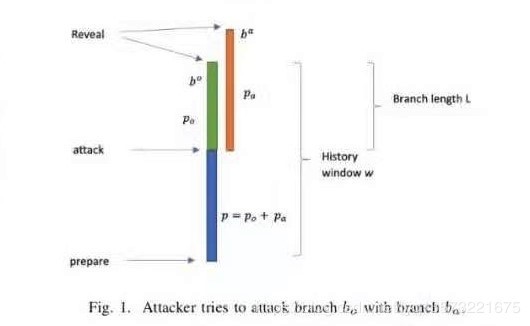
In the original branch, the attacker needs to spend a hash to calculate force Pa and time t, the optimal overhead for Pa W/2 cycles, and then at the time of attack will Pa switch to hide branch, as shown in figure Fig. 1; In order to attack is successful, we need to meet:
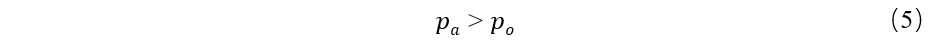
As a result, the malicious branch of public Ba will be longer than the original branch Bo, when released, the original branch HWD for:
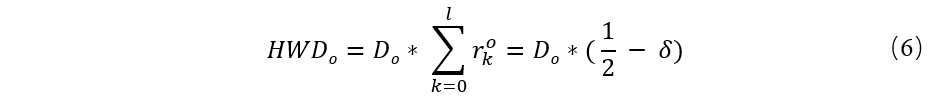
Among them the smallest edge of the delta for the node to accept difference, so the malicious branch HWD is:
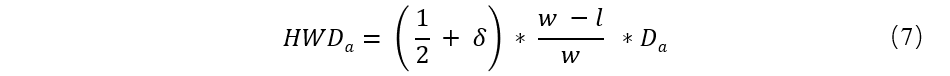
Therefore, we need to:
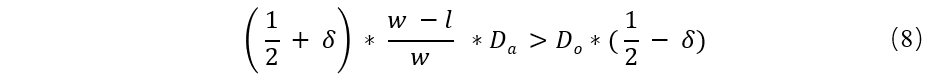
Because Da and Do in this case the infinite close, we can simplify the equation:
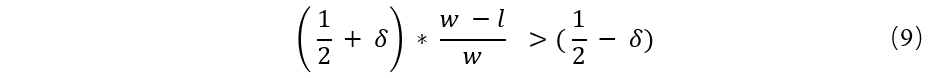
And can be concluded that:
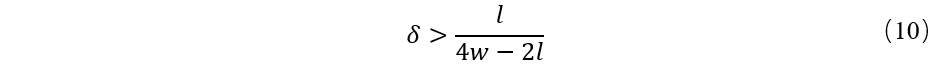
In a word, the attacker's lowest price is in the time window (W - L) overhead hash work force Po * (1/2 + L)/(4 W - 21),
For the typical attack, about 50-500 block is needed to make token from a token cash exchange, from the perspective of the analysis of the following, the miners' switch is not frequently, we can easily set up W & gt; 1 month to increase the weights of history, when W=100000 pieces, the robustness of the attack (editor's note: refers to the system in the case of a disturbance or uncertain can still maintain their characteristic behavior) could be improved by more than 100 times,
Although we can't entirely avoid 51% of the attack, but we can significantly increase the attacker's cost of capital and time costs to more than two orders of magnitude, because an attacker can take quite a long time to prepare, so the possibility of attack is much smaller, because of long time attack will cause a lot of opportunity cost and uncertainty, the HWD scheme comparison, additional improvements to further increase the attack cost,
4. Additional improvements
Above is HWD, additional improvements will be on the basis of the previous more to increase the cost of the attacker,
With the first scheme is released Ri & lt; nullnullnullnullnullnullnullnullnullnullnullnullnullnullnullnullnullnullnullnullnullnullnullnullnullnullnullnullnullnullnullnullnullnullnullnullnullnullnullnullnullnullnullnullnullnullnullnullnullnullnullnullnullnullnullnullnullnullnullnull
