Crypto wallet is fully controled by private key, if the private key is lost, the wallet is no longer accessible. This is secure in one way. Or, it cause a lot of trouble in real application, This solution is to dojo.provide a way to recover a private key using the second way.
Editor's note: this article main content from the stone block chain CEO xiao-hu Chen,
A, background
The private key is very important, the key to the world, can be said to be the block chain now is mainly used to control the virtual digital assets, but may extend to all sorts of assets in the future, as to the identity of the control (such as car keys, digital identity, certificates), once the private key is missing, the private key of digital assets and control will be lost, all at the same time, you can also ask for any person or organization to help you find your own private key, if you want to block chain knowledge popularization and application of continuous, the private key storage and recovery plan will be the basis of block chain world configuration,
The purpose of this article is to provide a kind of block chain based on the technology of encryption to entrust the key storage and recovery method, in order to solve the existing user keys security is not high or loss of the user can't recover after technical problems, such a solution should follow the following three criteria:
External features: service program cannot access the private key,
Customizable: even in the case of a private key is lost, the user should be able to understand and configure the recovery options,
Security: there should be no simple method through the recovery options to hijack another person's private key, only have one account can recover the private key,
Second, the existing solution
The more general private key recovery program has a variety of:
2.1 word mnemonic
Backup in advance a mnemonic word (another form of the private key), backup depends on the users themselves, usually advice is copied on paper at home, some demanding may put the paper in the safe, but this solution is facing the risk of "single point of failure", for example, the paper may be lost because of various reasons,
2.2 Secret sharing
To do the decentralized storage and recover the private key, Secret sharing is a good solution,
Its principle is to spread out a secret, the encryption and store it in a number of participants, only when reach a certain number of participants can spell out the original secret, and a small amount of participants themselves unable to get the secret both to reduce the risk of a single node failure, and can recover the private key, under the condition of certain
Technology itself is not difficult, difficult is to store and restore process standardization, the transition, who are stored in there? How to authenticate to restore? How to ensure the storage of the power, how to avoid the private key storage people unite fraud owner,
Inside the industry has provided related tools, such as: Vault12 solutions is the private key holder can invite friends and relatives as a custodian, pay a monthly fee, can be set according to the data storage security level degree of recovery (such as less key can be as long as confirm to restore a depository, special key may be 3/5 to restore), need a friend by video before recovery, telephone and other way to confirm identity, overall speaking, the scheme is more perfect, detailed, flexibility and operability, is enough to focus on the key recovery,
The solution of the biggest problems is that a certain number of friends group members can work together, from the owner to steal the account access, even if the owner did not ask them to do so, that's why ideally, team members should not know who else in the group, and when the users really need to recover the private key, interactive process and is too complex, experience,
2.3 standard KYC program
With modern Banks perform KYC process similar to new customers, the user can show the KYC providers that their identity, so that to obtain funds, however, users need to perform an already set a good process, the logo behind the provider in order to know the address,
KYC verification is insufficient, the process is usually handled by third party providers (such as IDNOW), it is a costly and a bit of a violation of block chain principle of work,
Three, the technical implementation scheme
3.1 registered stage
Users in the local to the user's private key is encrypted, and put forward an application for registration to the management counter;
At first, the user needs to save the private key encrypted with password (password) (private key), we have defined as EPK1; At the same time, also needs to be saved with safety (security answers) encrypted can restore the content, and public key encryption, again we defined as EPK2,
This information is saved to the service provider in the database,
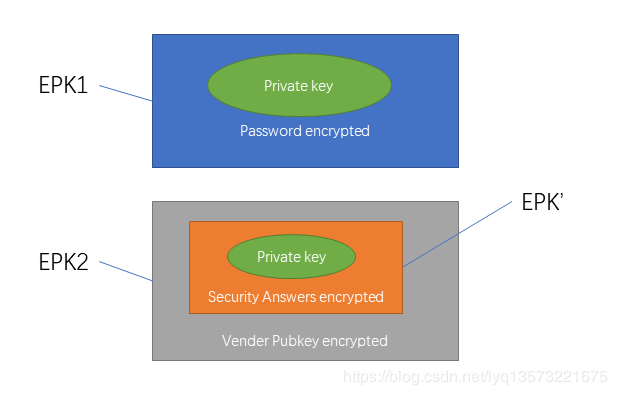
As a result, can express the relationship between them in the following formula:
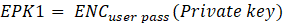
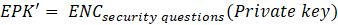
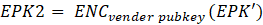
Thus, in the service provider's database, save the following information:
Number content
1 User Name
2 Hashed User Password
3 EPK1
4 EPK2
5 Security Q
6 Vender Pubkey
3.2 user registration process
User registration flow chart is as follows:
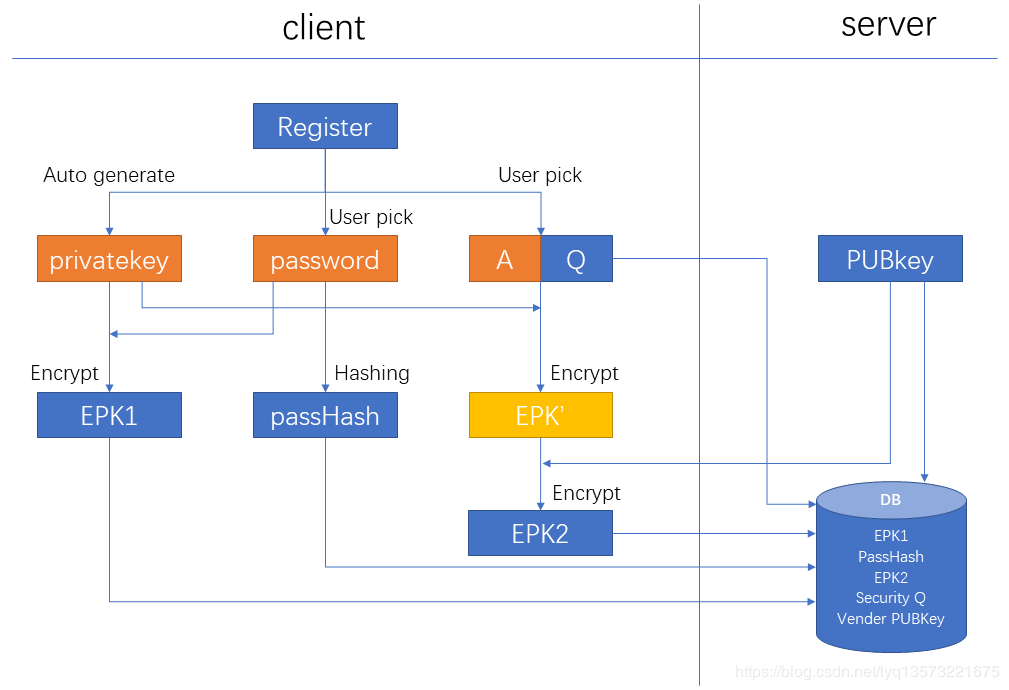
The main steps include:
(1) the private key encrypted locally (EPK1) save;
(2) the user passwords encrypted locally (PassHash) save;
(3) set the user questions and answers, after is encrypted with the private key locally (EPK '), then use the platform (EPK2) keep the public key encryption when;
(4) to save the problem of users to set (Security Q);
(5) save the platform for the public key (PUBkey);
3.3 the private key recovery
If the user password (password) not lost, log in and access to the private key flow chart is as follows:
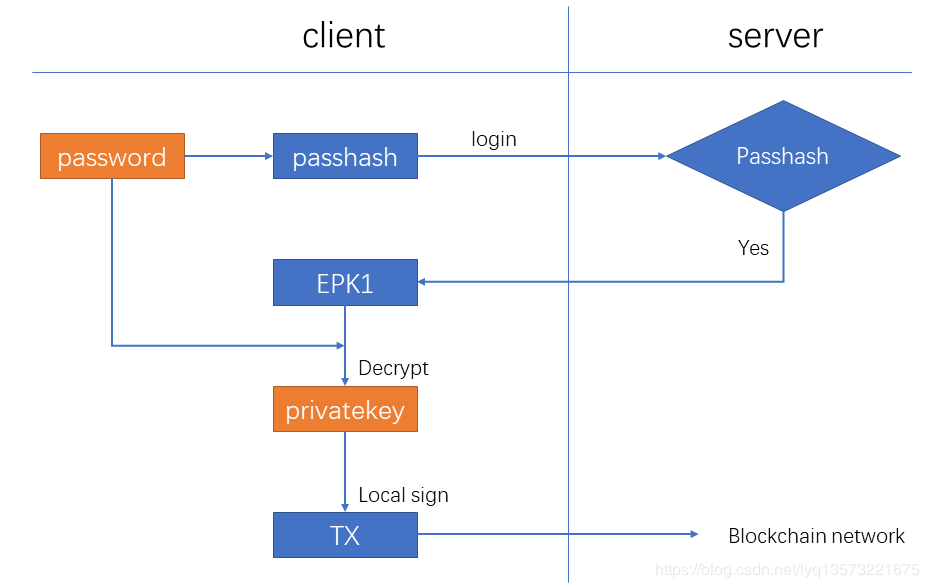
The main steps include:
(1) login password input, get passhash;
(2) compare with passhash saved in the database, if the same, return EPK1;
(3) the user in the local use the password from EPK1 decrypt the private key;
(4) with the private key locally signature, and send the deal to block chain network;
3.4 log in and access to private keys
Lost if the user password (password), or if you want to use the new password to save the private key, password reset process need to save the database content, flow chart is as follows:
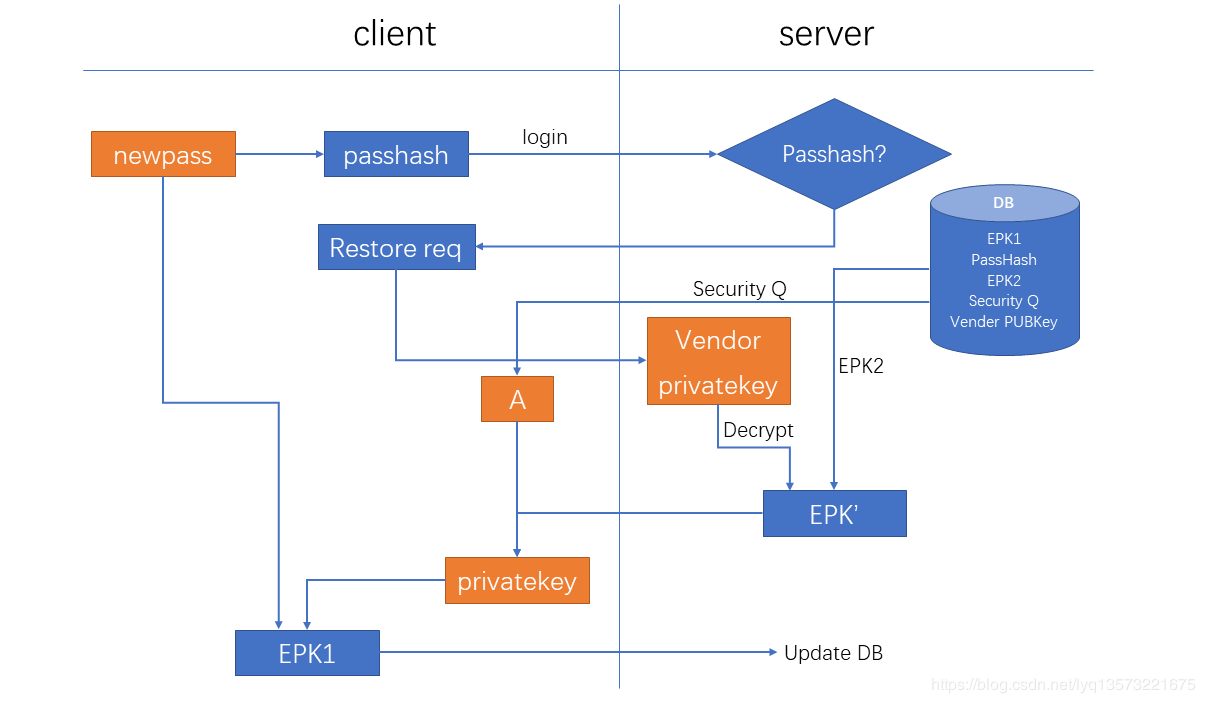
The main steps include:
(1) enter a new password when login newpass, get passhash;
(2) compare with passhash saved in the database, if not identical, to apply for to save, when get the platform the private key (vendor privatekey);
(3) took EPK2 from database, use the platform decrypted, get EPK ';
(4) the user needs to answer the questions in the database, and to answer (can be a biological characteristics such as fingerprints, or the answer to the question) is correct, can recover from EPK 'private key;
(5) use newpass and privatekey to generate new EPK1, and update the database;
(6) so, next time the user can use the new password for the private key to sign or send trading,
-- -- -- -- -- -- -- -- -- -- -- -- -- -- -- -- -- -- -- -- --
Copyright statement: this article for the blogger (Li_Yu_Qing) of the original article
