We have an API hosted in Azure as an Azure Web App that we need to trigger via http on a schedule.
Our API requires a valid Azure AD Access Token be sent with each request.
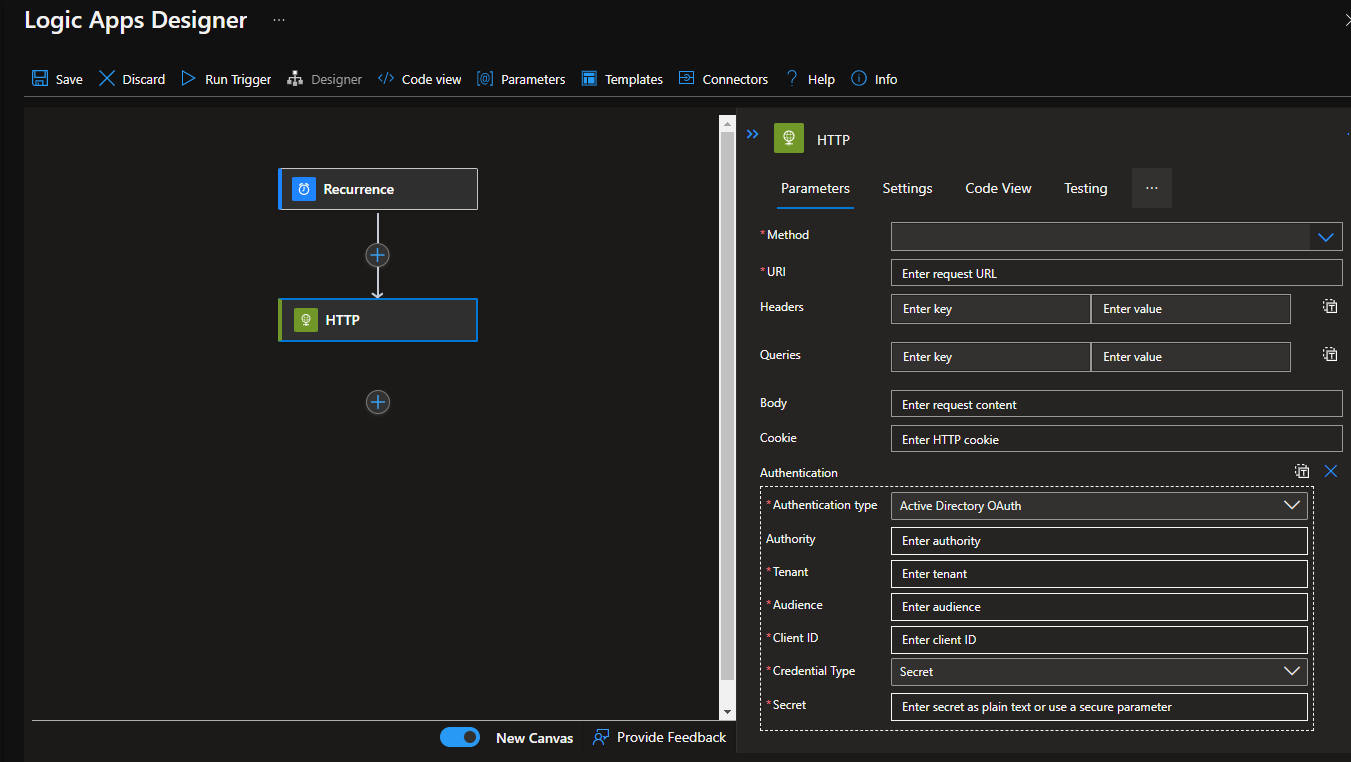
Azure Logic Apps gives us the option to authenticate our request with Azure AD. However, we do not see the option of including scope in the request. If we send a request without specified scope or role, we get the following error:
System.UnauthorizedAccessException: IDW10201: Neither scope or roles claim was found in the bearer token.
How can we authenticate an http request from an Azure Logic App when scope/role is required in the access token by the API?
CodePudding user response:
Thanks to @Skin for the suggestion!
Here is what worked for future visitors to this question:
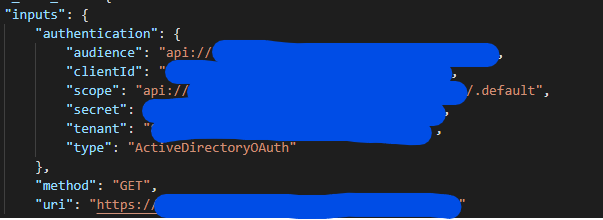
Navigate to your Logic App in the Azure Portal > Select "Logic App Code View" > Add the following to "authentication":
- audience: "api://<your api's clientId>"
- clientId: "<your logic app's clientId>"
- scope: "api://<your api's clientId>/.default" (this piece is not available in the interface)
- secret: "the secret you generated for your logic app in your aad app registration"
- tenant: "your tenant id"
CodePudding user response:
Parameter "Audience" is the scope. Depending on how you built your target api and what is expected there as audience in token you could probably have there somehting like: api://<yoru_app_id>/.default, but you should know it best. E.g. when you call Graph MS your scope/resource/audience here is: https://graph.microsoft.com/.default, but different APIs have different needs for scopes.