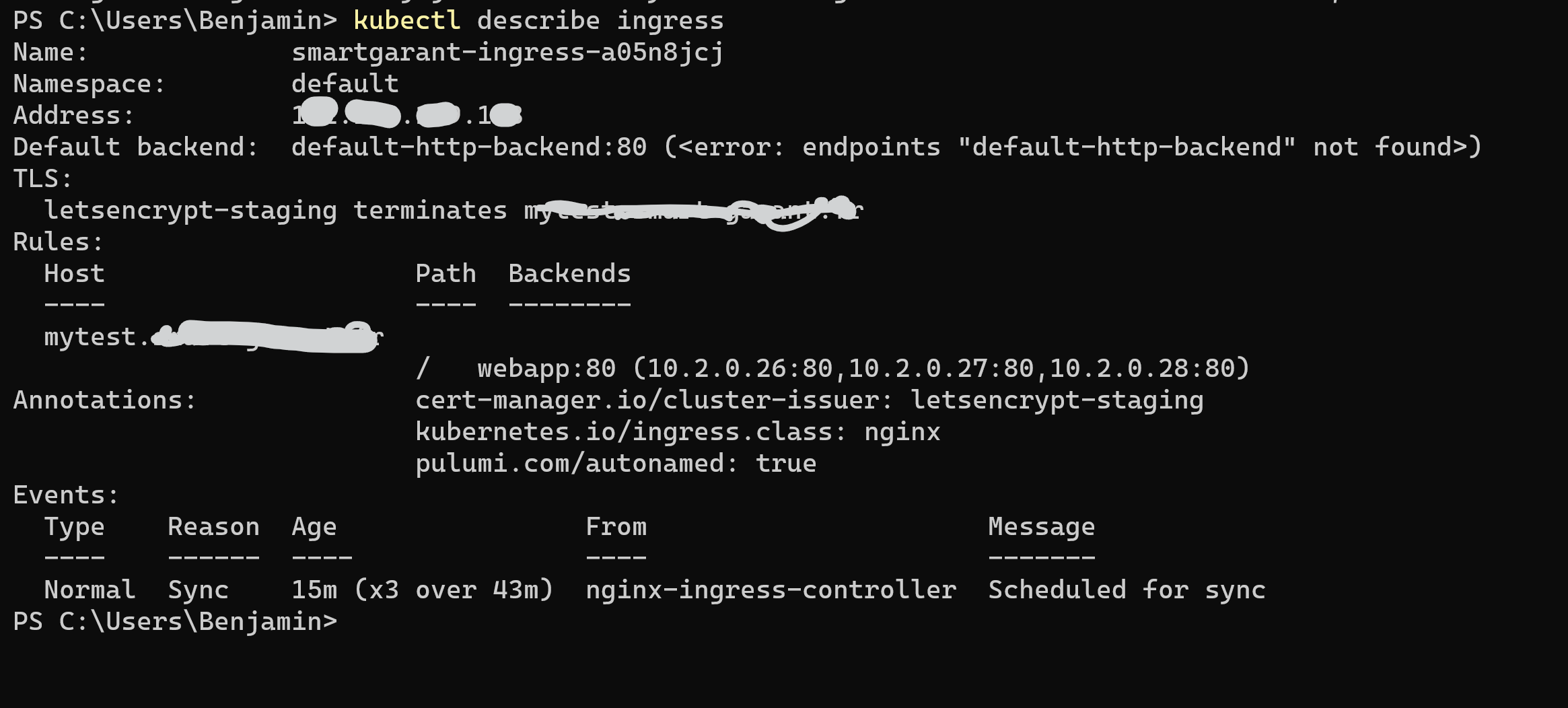
I don't undestand why i can't get certificates on K8S using cert-manager
-
But when i try to get an certificate i get 'no resources found'
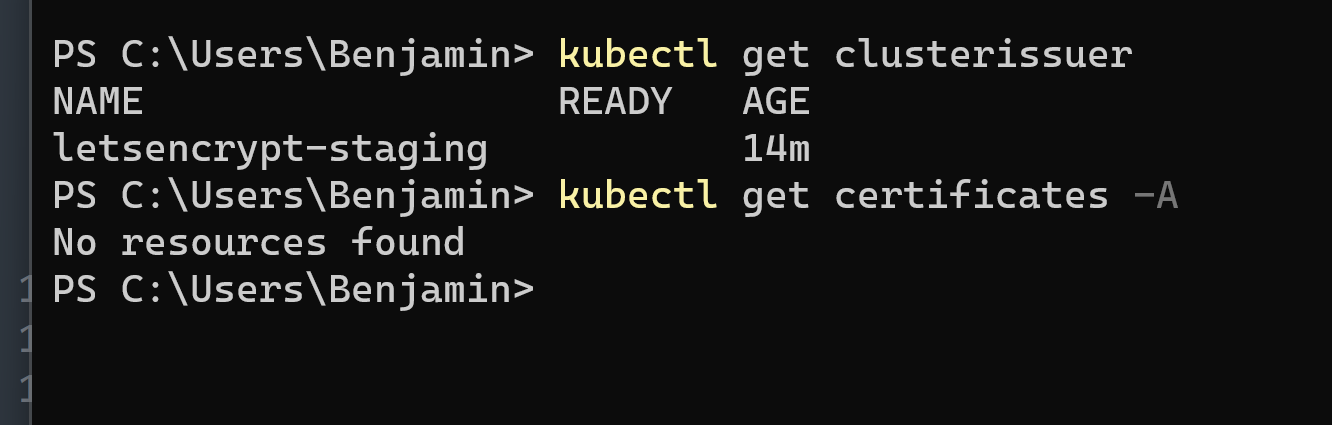
Any idea ?
Thank you for your help
CodePudding user response:
Certificates are not created automatically by cert-manager. You have to create a YAML yourself. And use the issuer name that you have already created
apiVersion: cert-manager.io/v1 kind: Certificate metadata: name: my-certificate namespace: default spec: secretName: set-a-new-name-here issuerRef: name: letsencrypt-staging kind: ClusterIssuer commonName: mytest.example.fr dnsNames: - mytest.example.frCodePudding user response:
acme-staging-v02.api.letsencrypt.orgwill not issue trusted certificates, this is used to check the verification process only. After you have checked the verification process is all good, you can create a new issuer with the URL set tohttps://acme-v02.api.letsencrypt.org/directory.After that, you can follow the official example here to make a certificate request, just make sure the
issuerRefpoints to your updatedClusterIssuer.CodePudding user response:
If you don't want to create kind certificate you can use
apiVersion: cert-manager.io/v1alpha2 kind: ClusterIssuer metadata: name: cluster-issuer-name namespace: development spec: acme: server: https://acme-v02.api.letsencrypt.org/directory email: [email protected] privateKeySecretRef: name: secret-name solvers: - http01: ingress: class: nginx-class-name --- apiVersion: extensions/v1beta1 kind: Ingress metadata: annotations: kubernetes.io/ingress.class: nginx-class-name cert-manager.io/cluster-issuer: cluster-issuer-name nginx.ingress.kubernetes.io/rewrite-target: / name: example-ingress spec: rules: - host: sub.example.com http: . . #Path and service configs . . tls: - hosts: - sub.example.com secretName: secret-nameingress will call clusterisser and it will auto-create certificate for you.
Update ingress resources as per need if you are higher version 1.18 or above
Notes
Make sure you are using the URL
https://acme-v02.api.letsencrypt.org/directoryin clusterissue or else you will get fake certificate in browser.For refrence you can read more here : https://stackoverflow.com/a/55183209/5525824
Make sure also you ingress pointing to proper clusterissuer if you have created new.
Also don't use same privateKeySecretRef:name: secret-name you need to delete it or use the new name as fake certificate now stored in that secret so.