I have a public Azure function. I can just visit its url and I see the application. Is it possible to restrict this so that only the API Management service can access this function? I don't want to make the function private (Vnet) because then I need a very expensive (Premium plan) for the API Management.
CodePudding user response:
One of the workarounds I did to restrict the Function App from Internet Access and to only allow from the APIM Instance is:
- Created the .NET Azure Function App with HTTP Trigger (minimal code) - Consumption Hosting Plan from the Portal:
#r "Newtonsoft.Json"
using System.Net;
using Microsoft.AspNetCore.Mvc;
using Microsoft.Extensions.Primitives;
using Newtonsoft.Json;
public static async Task<IActionResult> Run(HttpRequest req, ILogger log)
{
log.LogInformation("C# HTTP trigger function processed a request.");
string responseMessage = "Hello Krishna, This HTTP triggered function executed successfully.";
return new OkObjectResult(responseMessage);
}
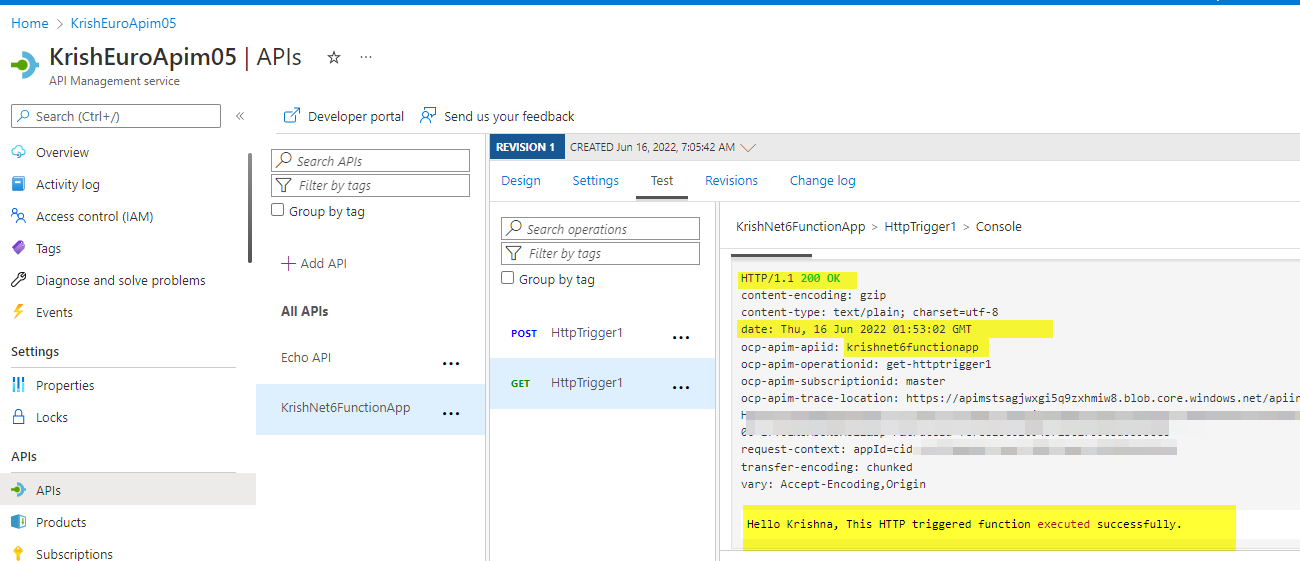
- Added this Function App API to the Azure APIM Instance.
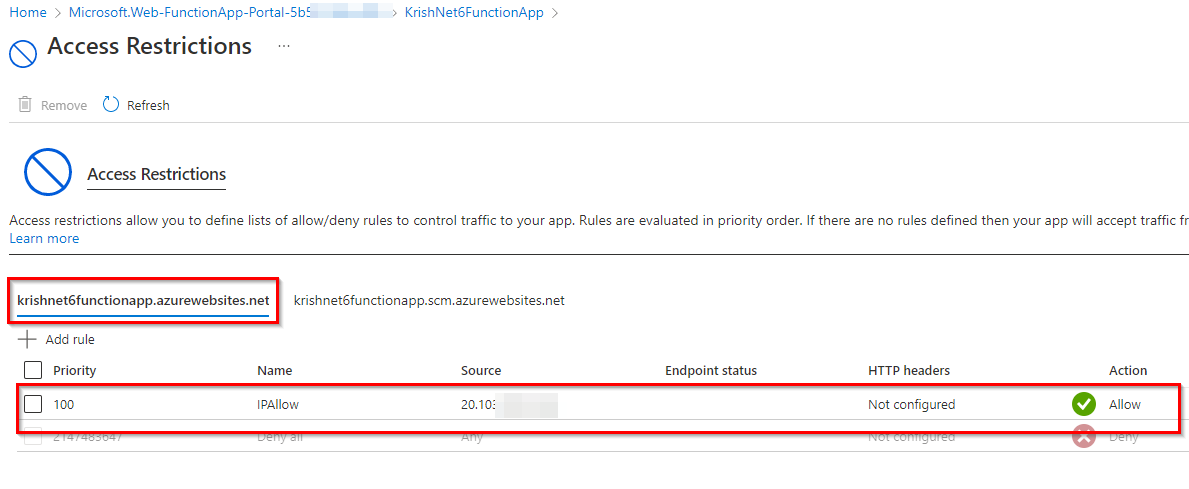
- In the Function App (Portal) > Networking under Settings > Access Restrictions > Added a rule that allows the APIM Public IP address only:
Tests:
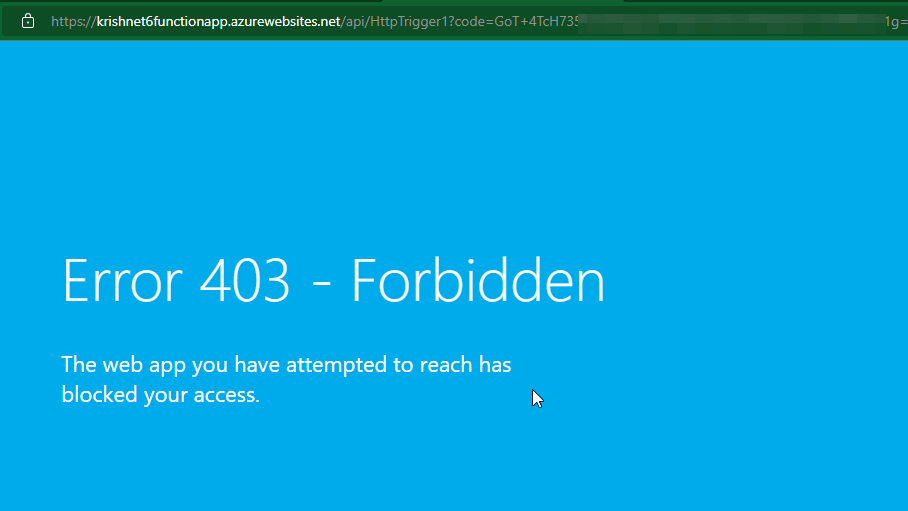
- I have set the Function Authorization Level to Function So Anonymous users cannot access the Function App URL without Function Key-Code in the URL.
- To protect the Function App more securely like to accept accesses only from same Azure AD tenant resources, you can Configure Authentication in Function App.
Refer to the Microsoft Blog Article on Accepting traffic only from APIM for the Function App.
