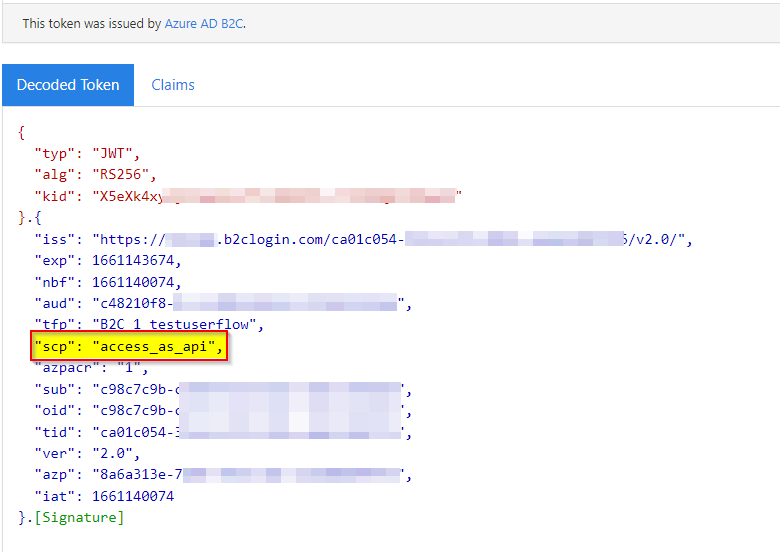
I have also generated a client secret and attempted to retrieve a token using the client-credentials grant type. While it returns a valid token. It doesn't appear to contain the scp claim which should be the access_as_***** value. How might I get this claim to appear in the token response when the access_token is decoded?
CodePudding user response:
Please note that,
client-credentialsgrant type works with Application permissions only. As your exposed API scope is Delegated, it won't work withclient-credentialsgrant type.
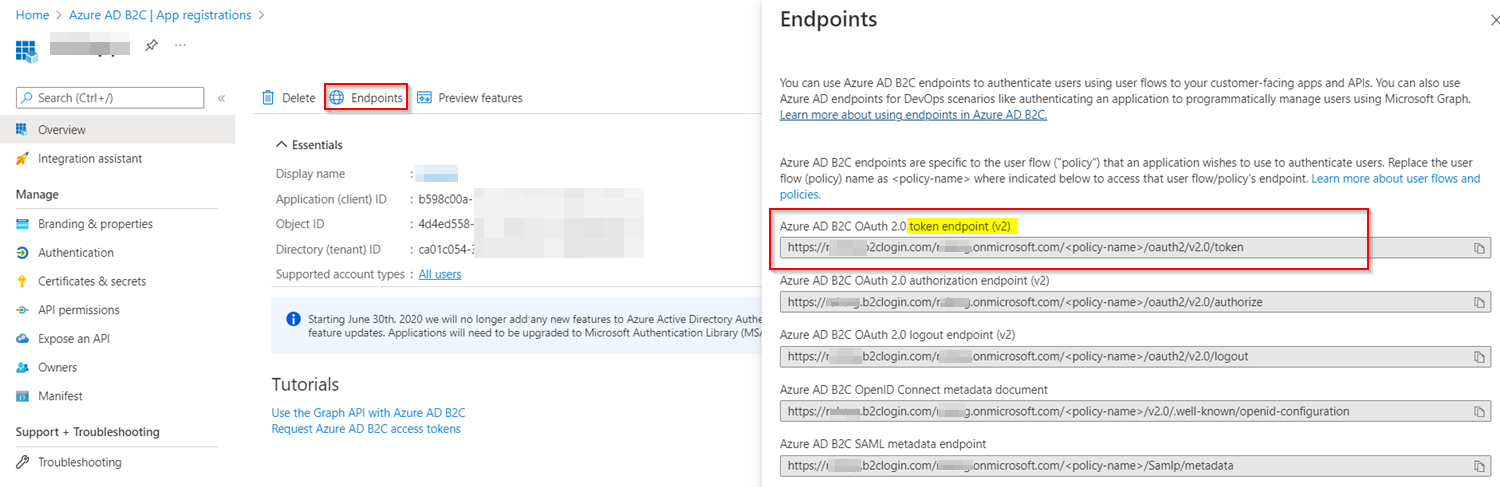
In addition to that, you are using wrong token endpoint to generate the token.
You can get token endpoint of your application like below:
Go to Azure Portal -> Azure AD B2C -> App registrations -> Your App -> Overview -> Endpoints
I tried to reproduce the same in my environment and got the below results:
I have registered an API application and created AppRole by changing its manifest like below:
"appRoles": [
{
"allowedMemberTypes": [
"Application"
],
"description": "Access API",
"displayName": "Demo",
"id": "xxxx-xxxx-xxxx-xxxx-xxxxxxxx",
"isEnabled": true,
"lang": null,
"origin": "Application",
"value": "access_as_api"
}
],
Manifest of MyAPI:
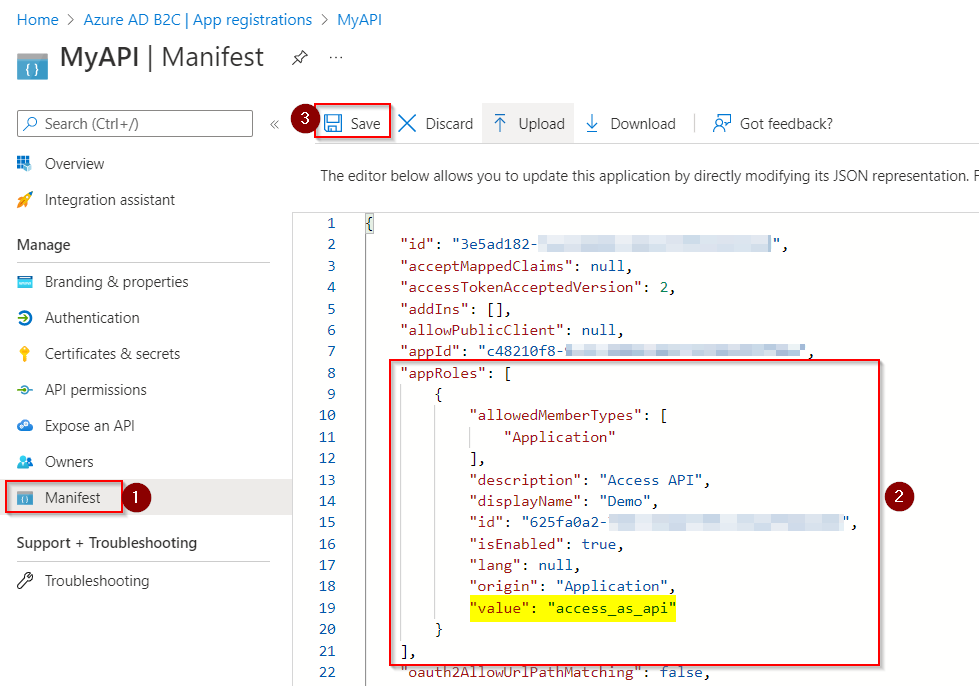
To generate the id, you can user either PowerShell or online GUID generator
I added this API scope in my application like below:
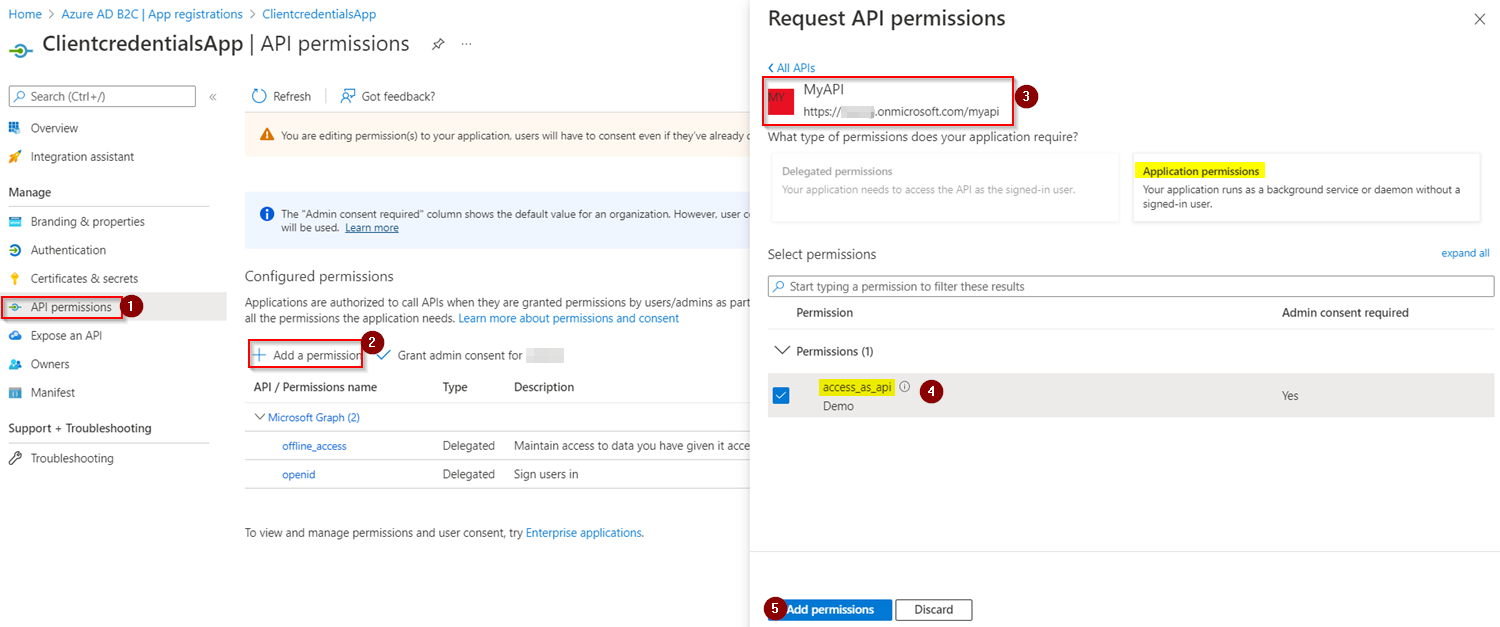
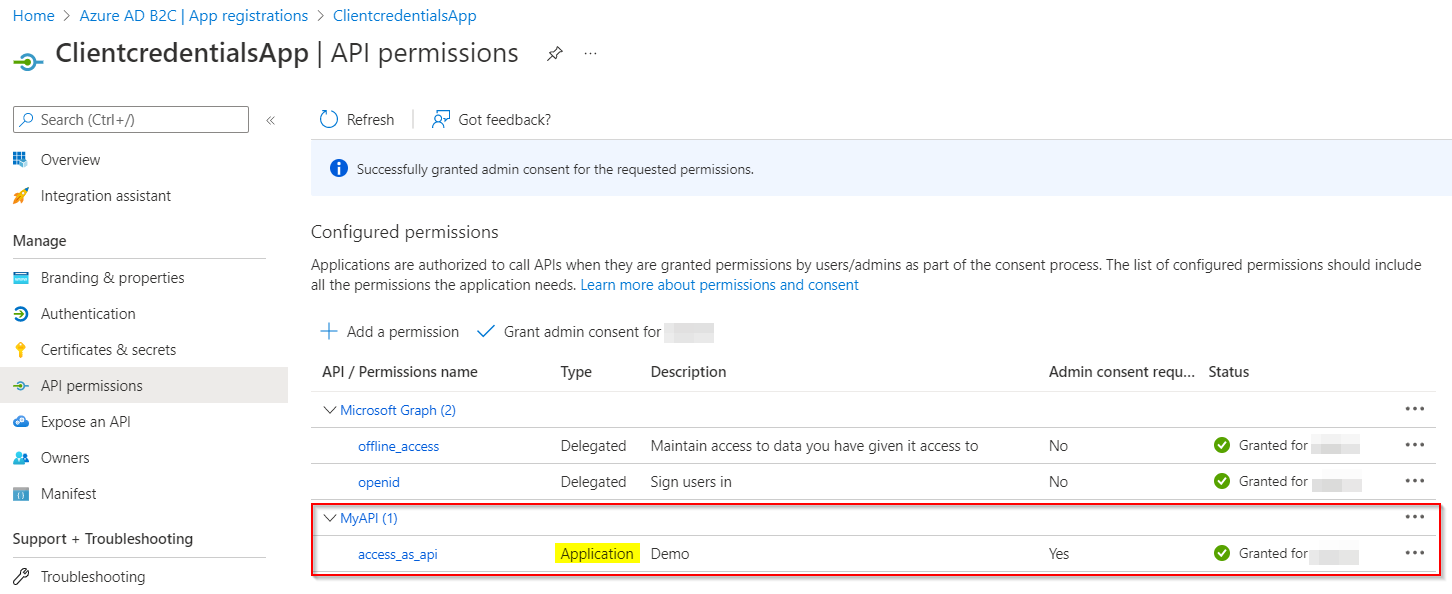
Make sure to grant consent for that added permission and it is of Application type:
I generated the access token using client-credentials grant type like below:
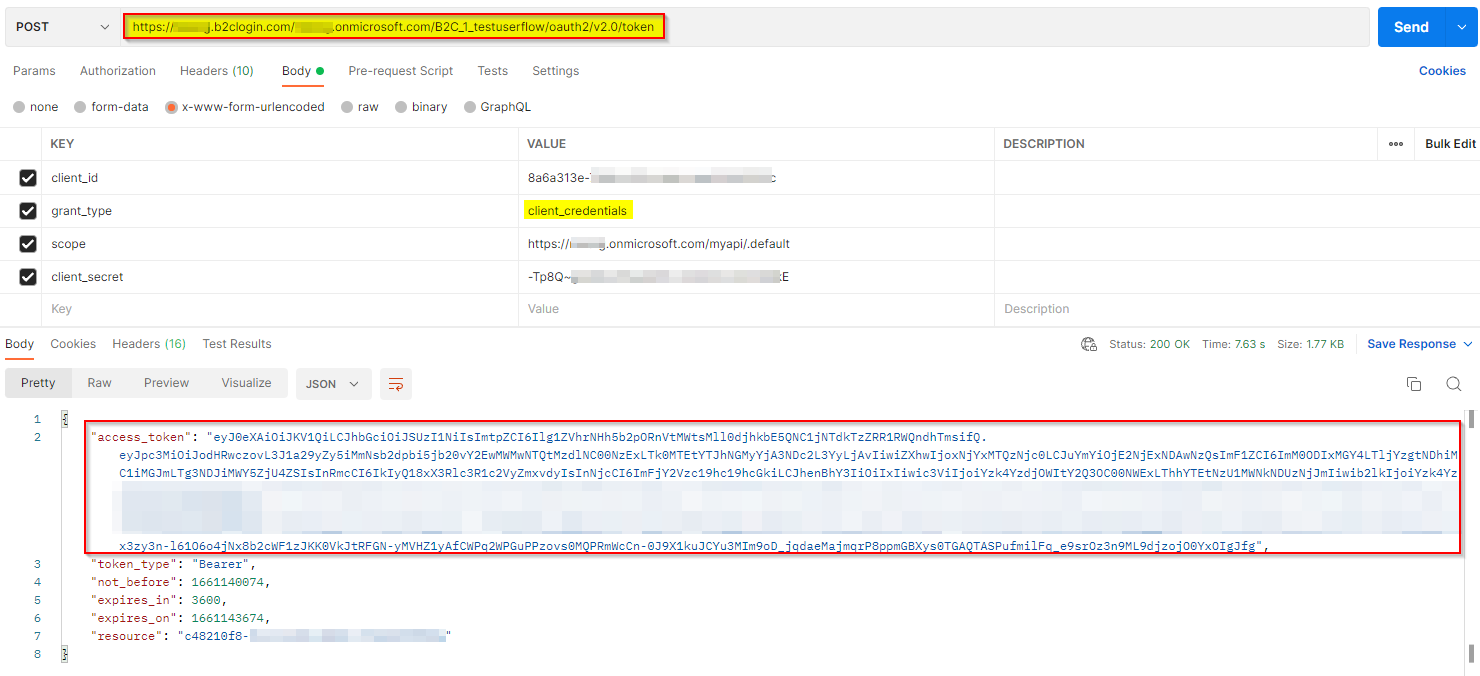
I got the scp claim successfully when I decoded the token like below: