The goal is to have an application, running on the user's computer authenticated as either themselves or a service principal, that can perform Azure resource management operations and Key Vault secret (data plane) operations.
So far, the resource operations are working fine with the management.azure.com audience, but the Key Vault data operations naturally fail with an error
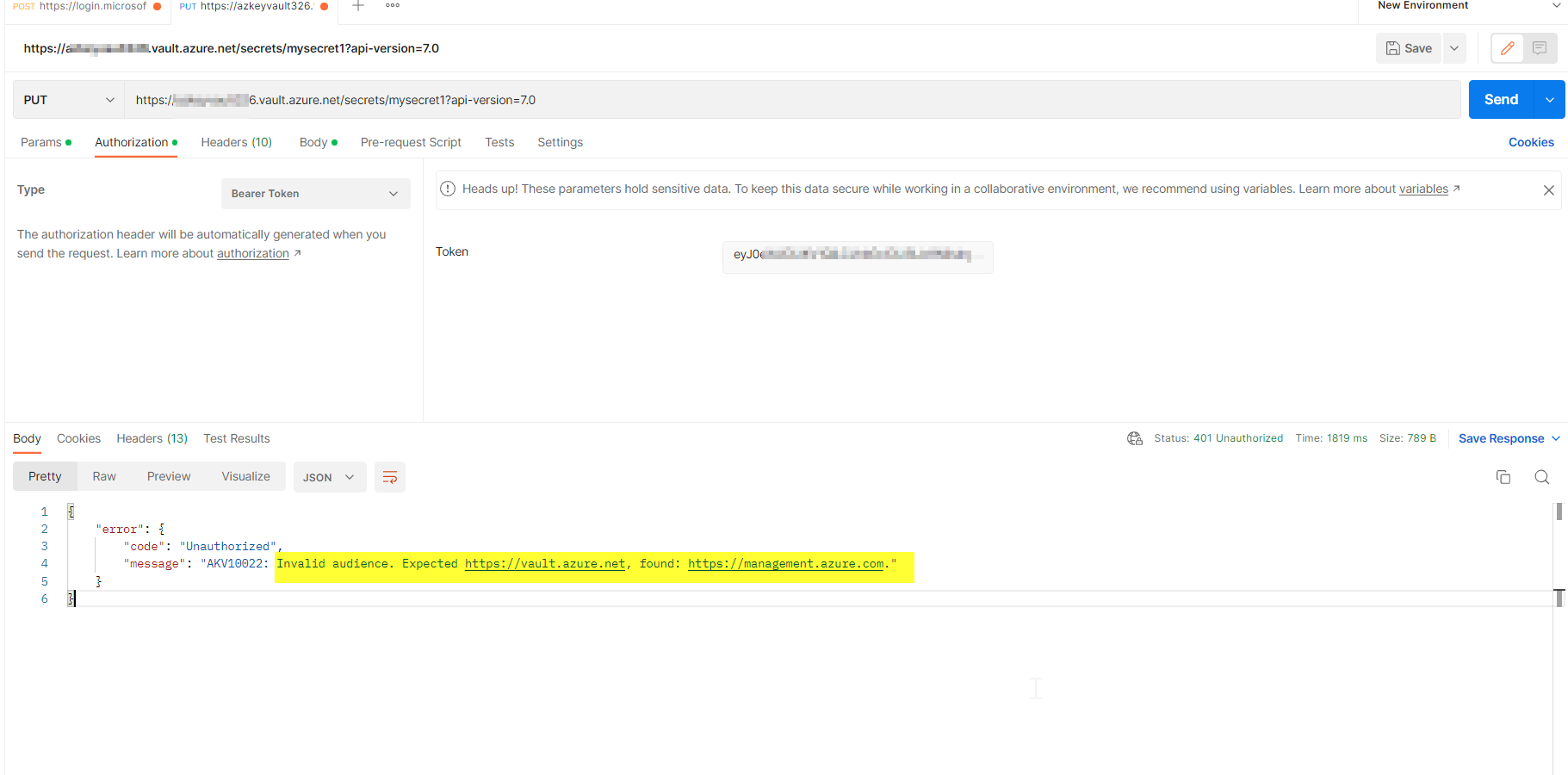
Invalid audience. Expected https://vault.azure.net, found: https://management.azure.com
I've pored over the docs but it's not entirely clear to me if it's possible to have a single token for both audiences? Here, e.g., it suggests you can simply request multiple scopes, but other sources seem to say they must be for the same resource?
Several of MSAL's token acquisition methods require a scopes parameter. The scopes parameter is a list of strings that declare the desired permissions and the resources requested.
A single token would vastly simplify the application, similar to how ADAL used to work.
CodePudding user response:
I tried to reproduce in my environment and got below results:
Invalid audience. Expected https://vault.azure.net , found: https://management.azure.com
The above error refers that audience of your token to call Azure Keyvault REST API you need to call the audience with https://vault.azure.net
I tried with postman to get token in my environment, ensure you have Registered AD application and keyvault with right process.
Before that check your Azure Keyvault policy and secrets to ensure that no Authorized application is chosen, and use a service principle rather than an application to access the secret.
When I tried with scope https://management.azure.com in postman and got access token.
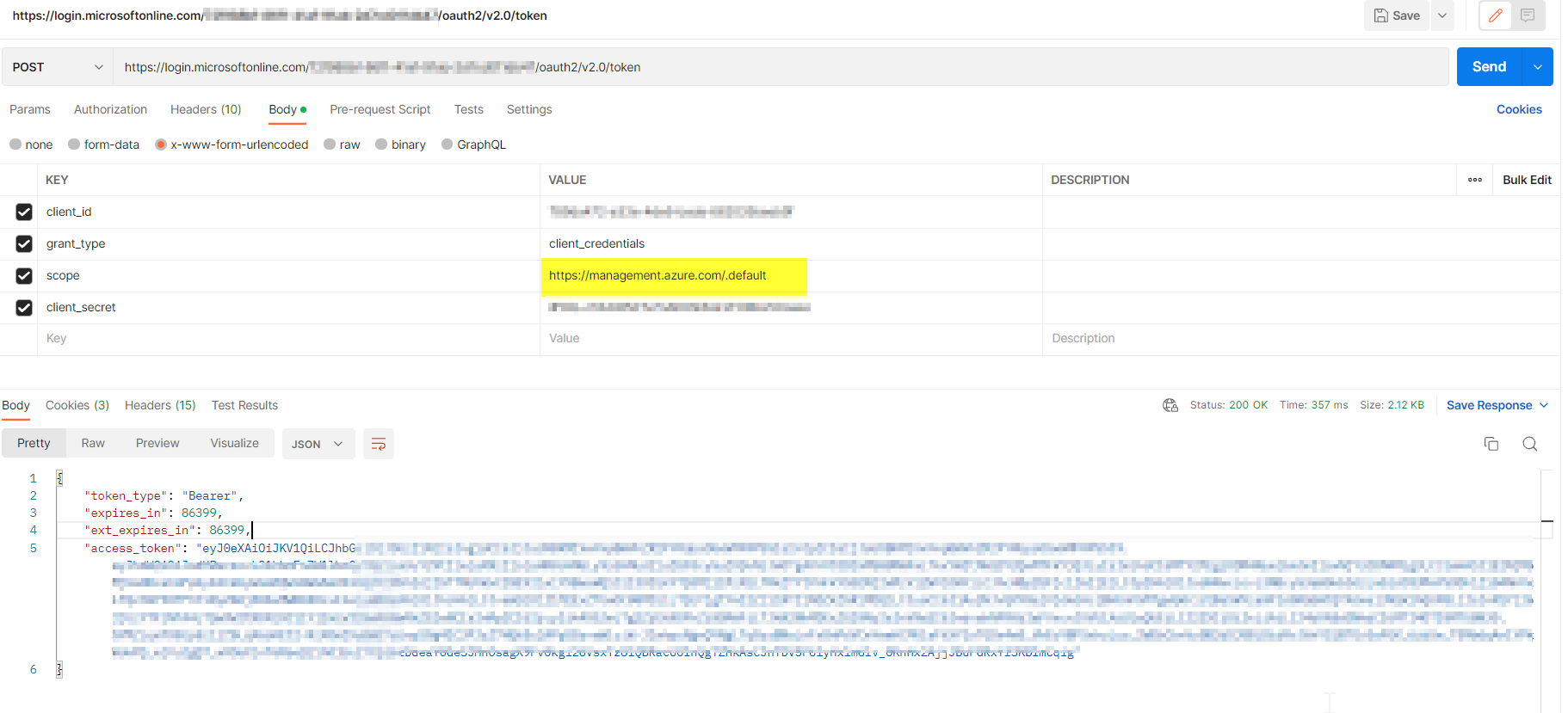
Then I copied the token to call the REST API to set secret.I got similar error.
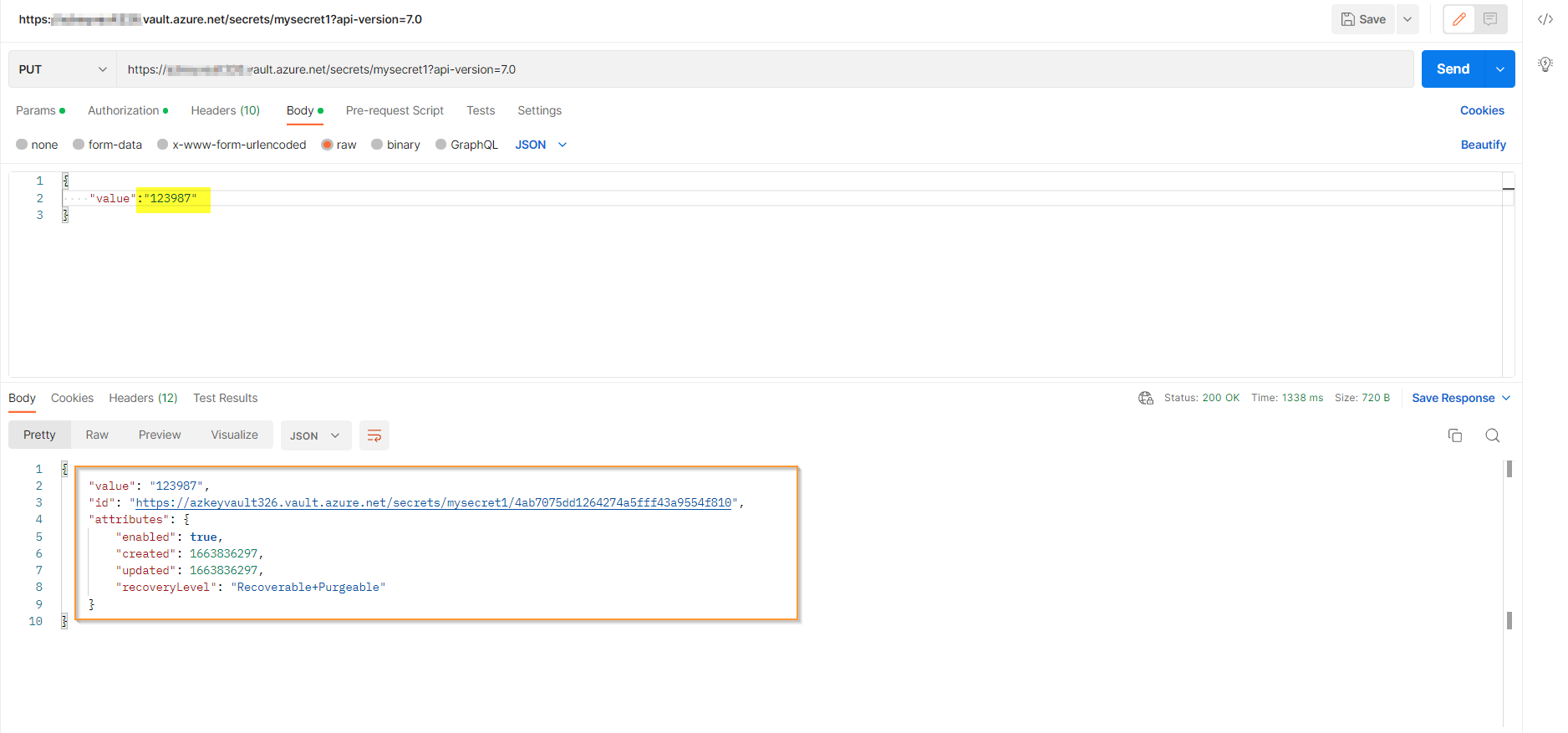
When I tried with scope https://vault.azure.net I got an output sucessfully.
Then I copied the token and called API & set secret, it will work fine.
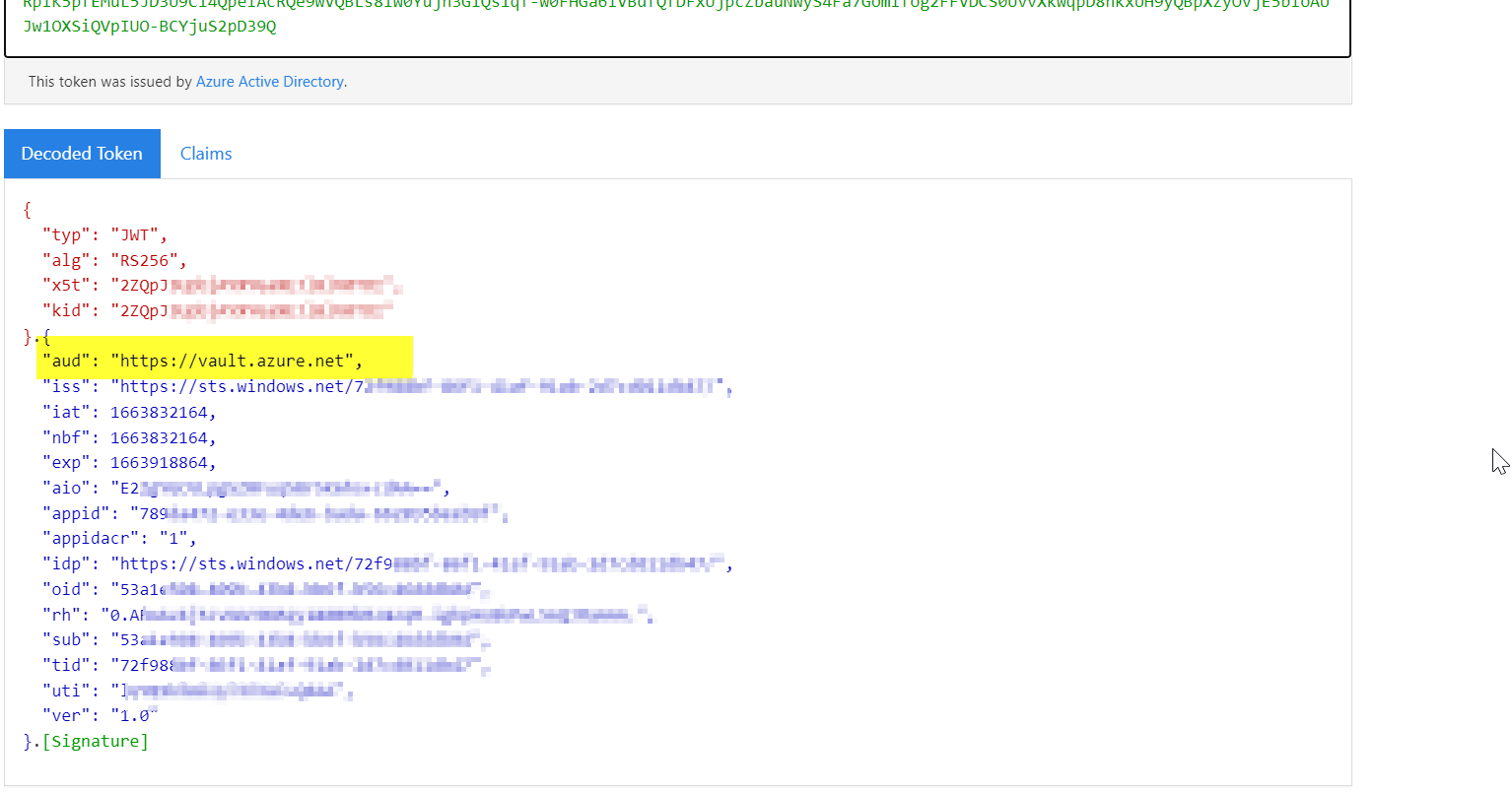
When I decoded token i'm getting aud with jwt.ms
Reference:
https://learn.microsoft.com/en-us/azure/active-directory/develop/v2-permissions-and-consent
CodePudding user response:
You cannot acquire one token for multiple audiences in AAD. This is not supported for token acquisition and also not by the actual services. This is not a MSAL limitation, ADAL cannot do this either. ADAL might request/store multiple tokens internally. You need to manage multiple tokens in this case.
Everything documented by Venkatesan is correct, just giving it a bit more context as an explanation.
See also https://github.com/MicrosoftDocs/azure-docs/issues/82875
