I can connect to MS Graph to get a Bearer token using Powershell but not with a Web Acvtivity in ADFv2 using the same credentials.
I'm getting the TenantId, ApplicationId and ClientSecret from an existing App in Azure.
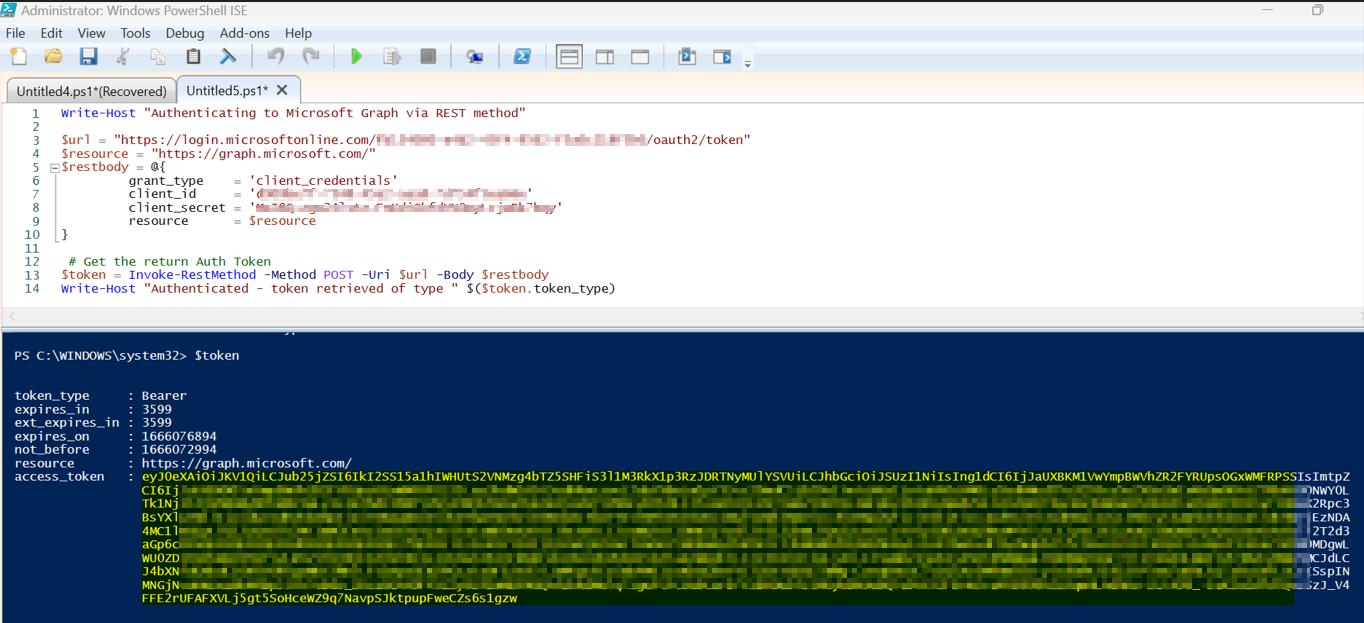
This is what I'm doing in Powershell - Works
# Authenticate to Microsoft Graph
Write-Host "Authenticating to Microsoft Graph via REST method"
$url = "https://login.microsoftonline.com/$tenantId/oauth2/token"
$resource = "https://graph.microsoft.com/"
$restbody = @{
grant_type = 'client_credentials'
client_id = $applicationID
client_secret = $clientSecret
resource = $resource
}
# Get the return Auth Token
$token = Invoke-RestMethod -Method POST -Uri $url -Body $restbody
Write-Host "Authenticated - token retrieved of type " $($token.token_type)
Result
This is the Web Activity - Fails
Input
{
"url": "https://login.microsoftonline.com/<tenantId>/oauth2/token",
"method": "POST",
"headers": {
"Content-Type": "application/x-www-form-urlencoded"
},
"body": "grant_type=client_credentials&client_id=\"<applId>\"&client_secret=\"<client_secret>\"&resource=\"https://graph.microsoft.com/\"",
"authentication": {
"type": "MSI",
"resource": "https://graph.microsoft.com/"
}
}
Error
Application with identifier '{appIdentifier}' was not found in the directory '{tenantName}'. This can happen if the application has not been installed by the administrator of the tenant or consented to by any user in the tenant. You may have sent your authentication request to the wrong tenant.
The error doesn't make sense as it works in powershell.
The difference here is that I'm executing the powershell with my own account and with a System Assigned MI in ADF. What permission am I missing? How do I troubleshoot this?
CodePudding user response:
I tried to reproduce same thing in my environment got below results:
PowerShell with Bearer token :
To resolve the error .Please follow below steps:
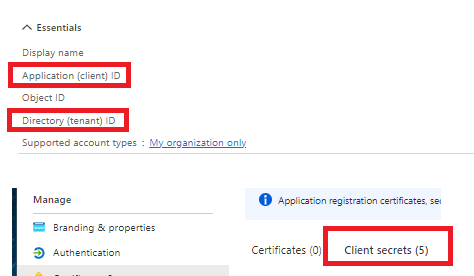
Step1: Created AD application added permission as below:
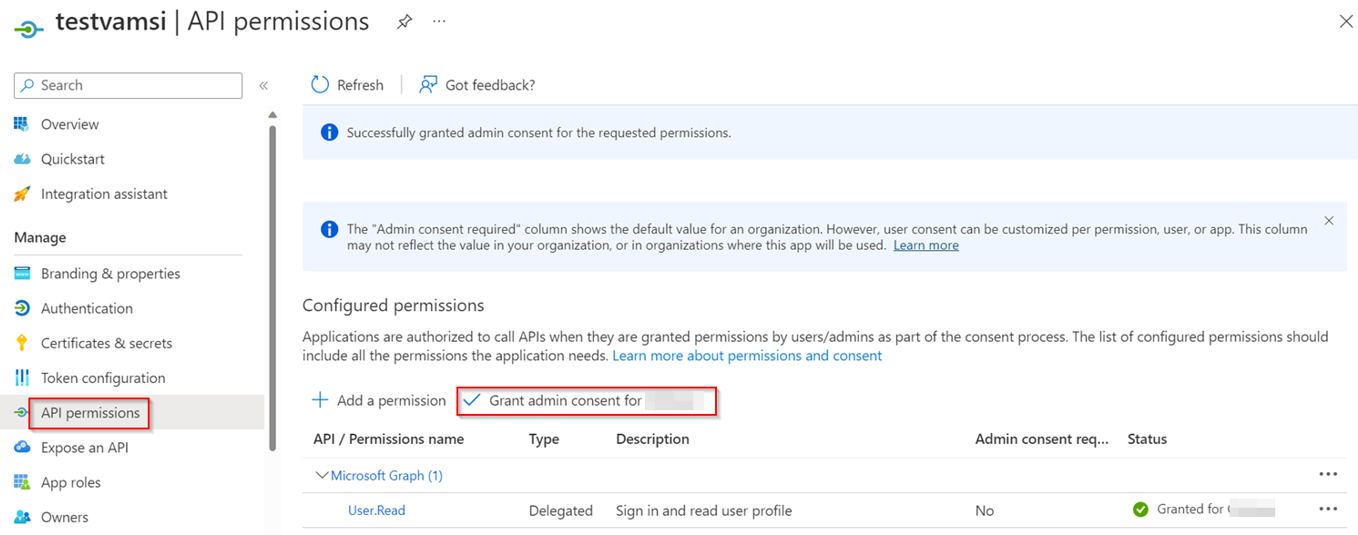
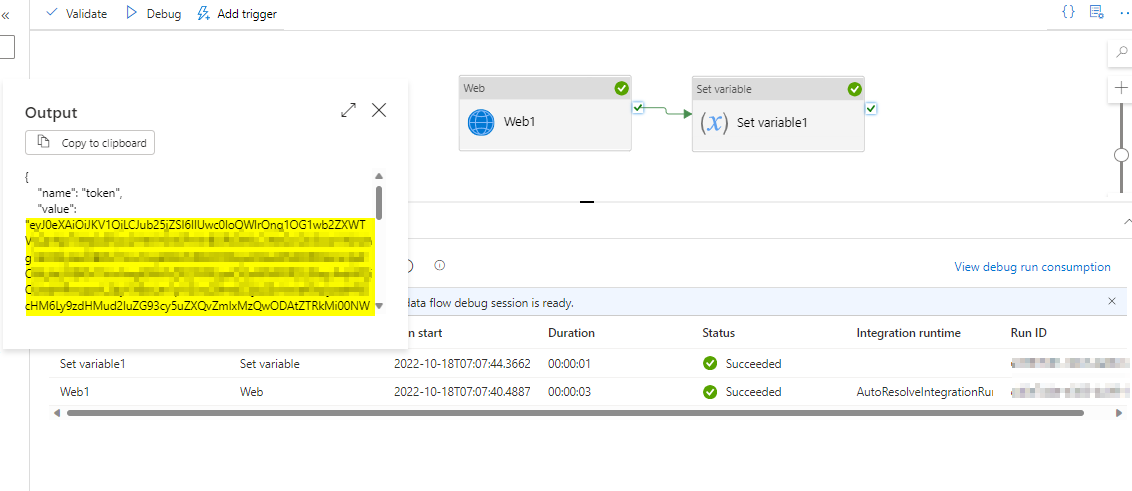
Step2: Create a web activity to get the Access Token from ADF
- URL:
https://login.microsoftonline.com/<Tenant ID>/oauth2/token
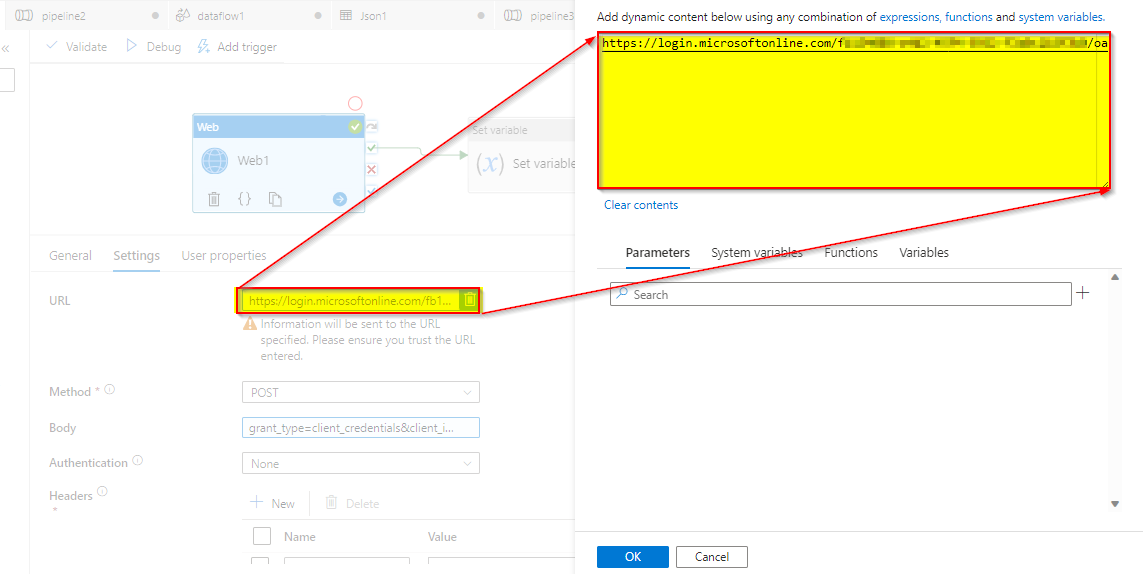
Method : POST
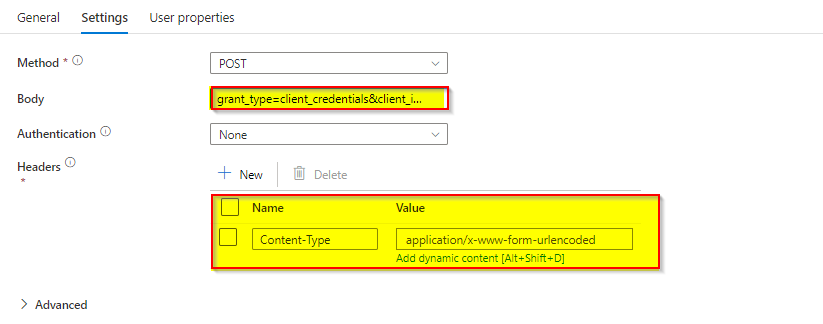
Body:
grant_type=client_credentials&client_id=<client_id>&client_secret=<client_secret>&resource=https://graph.microsoft.com/Header:
Content-Type:application/x-www-form-urlencoded
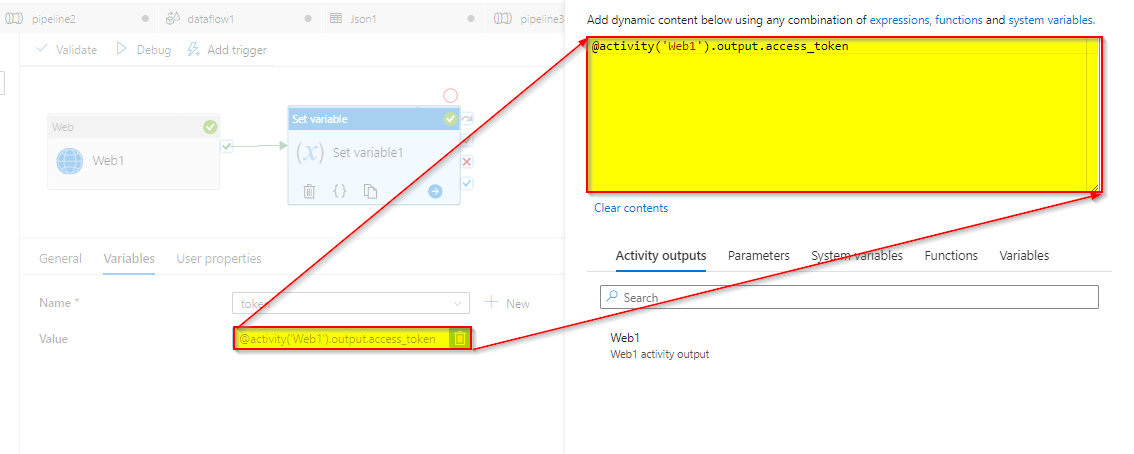
Step3: Create Set variable :
- Add dynamic content ->
@activity('Web1').output.access_token
Response