I am trying to create a protected kubernetes cluster on azure for that I have created the resource group name exampe1,after that created the arc enabled kubernetes cluster for the same resource group I have followed this document added the some extensions and connected to the cluster using the command
az connectedk8s connect --name cluster123 --resource-group rgexample --location eastus
so that the cluster got connected successfully to the azure
After that I want to see the workloads which are running on my kubernetes cluster and I want to monitor the clusters which are there on my cluster
I have given some access token to connect the workload but I am not able to see any workloads and monitoring cluster which are running on my cluster
Can any one help me that how to connect and what is the issue will be much appreciated
CodePudding user response:
I tried to reproduce the same issue in my environment and got the below results
I have created the resource group and arc enabled kubernetes cluster
While creating cluster I have added k8s extensions using below commands
az login
az extension add --name connectedk8s
az extension add --name k8s-extension
az extension add --name customlocation
az provider register --namespace microsoft.kubernetesConfiguration
az provider show -n Microsoft.kubernetesConfiguration --query "registrationState"
az account set --subscription sub_id
az connectedk8s connect --name <cluster-name> --resource-group <rg-name> --location eastus --correlation-id <c-id>
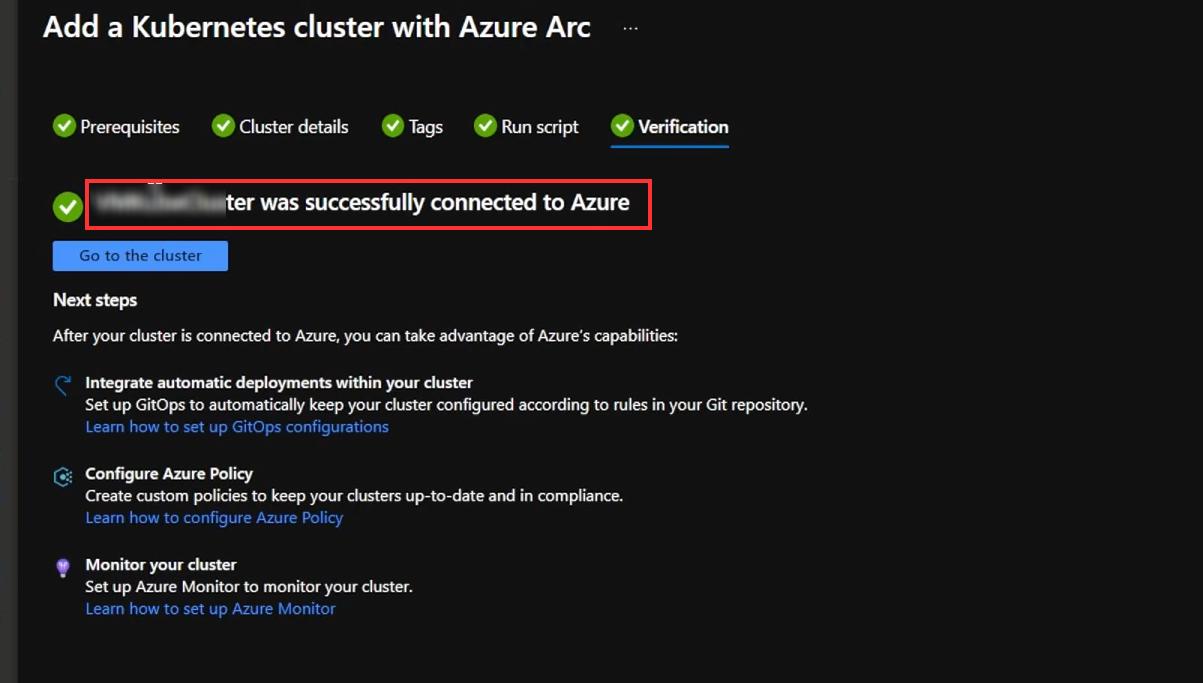
Created the arc enabled kubernetes cluster successfully and connected to azure
When I check in workloads I didn't find any nodes or pods, for that I have added the "service account bearer token"
kubectl create serviceaccount admin-user
kubectl create clusterrolebinding admin-user-binding --cluster-role cluster-admin --serviceaccount default:admin-user
$SECRET-NAME=kubectl get serviceaccount admin-user -o jsonpath='{$.secrets[0].name}'
$BASE64=kubectl get secret $SECRET_name -o jsonpath='{$.data.token}' [Text.Encoding]::Utf8.GetString([Convert]::FromBase64String($BASE64))
<!-- | base64 -d |sed $'s/$/\\n/g') -->
By Running the above command one token will be generated Using those token I can be able to see the workloads
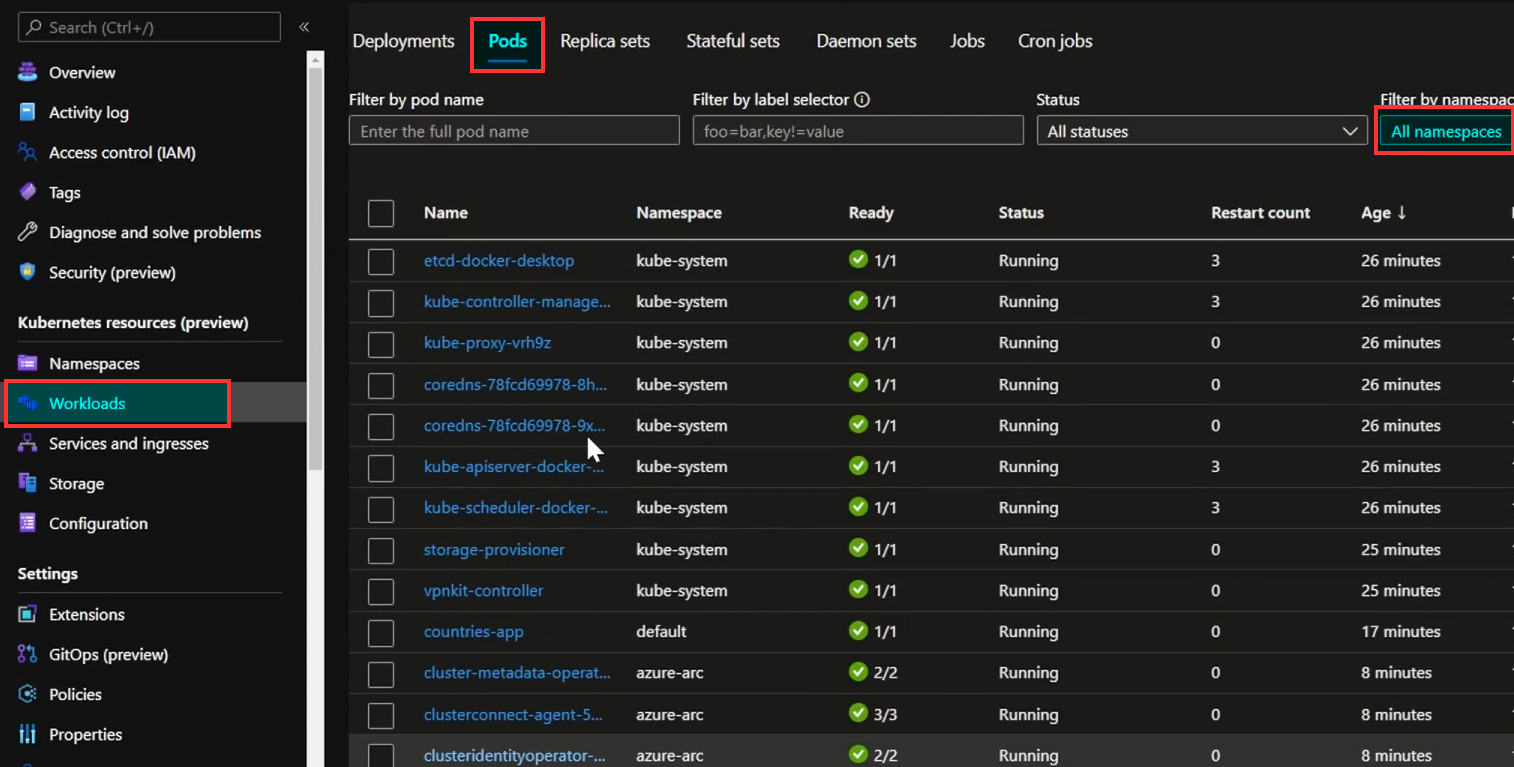
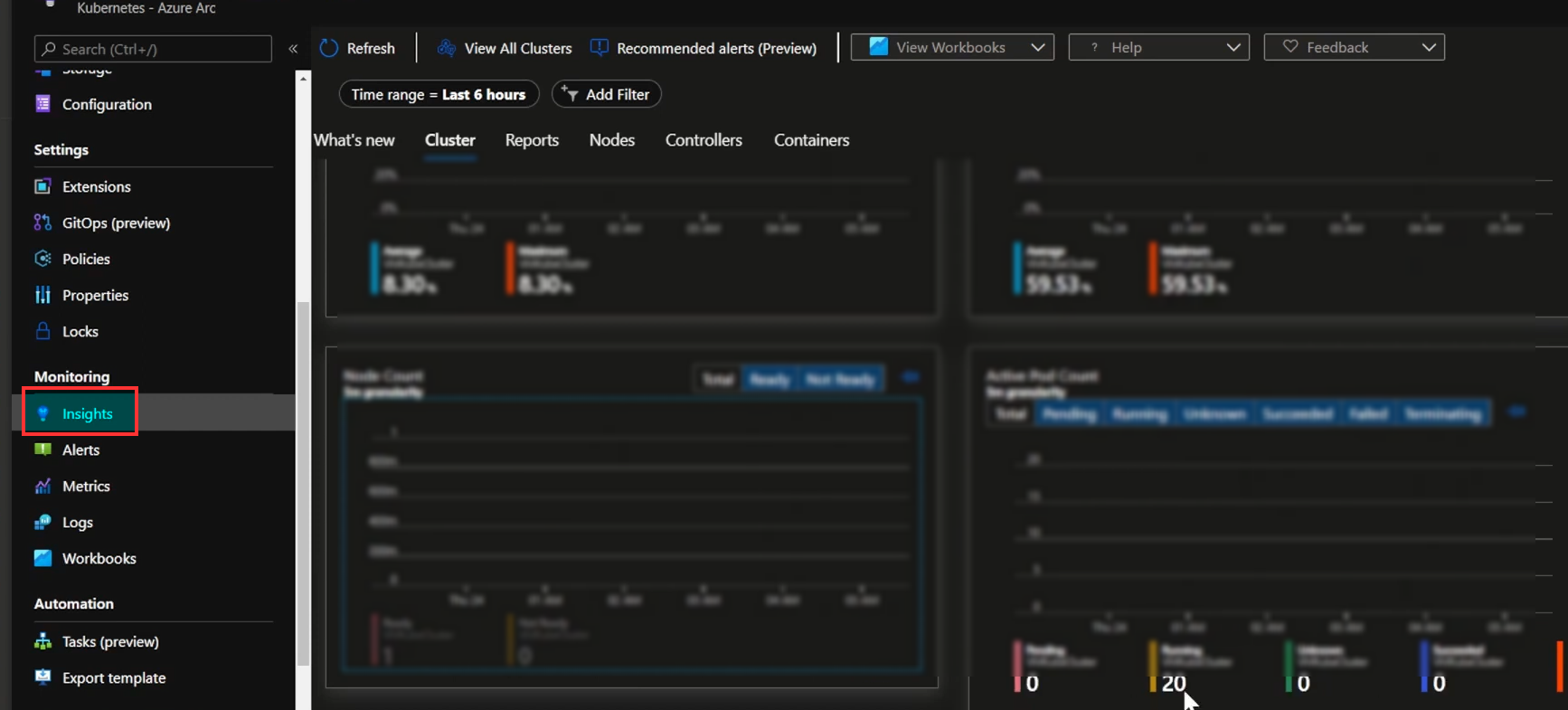
We can check all the pods ,namespaces and nodes which we have created in the workloads For monitoring the pods/nodes etc. click on insights and click on configure azure monitor it will onboarded
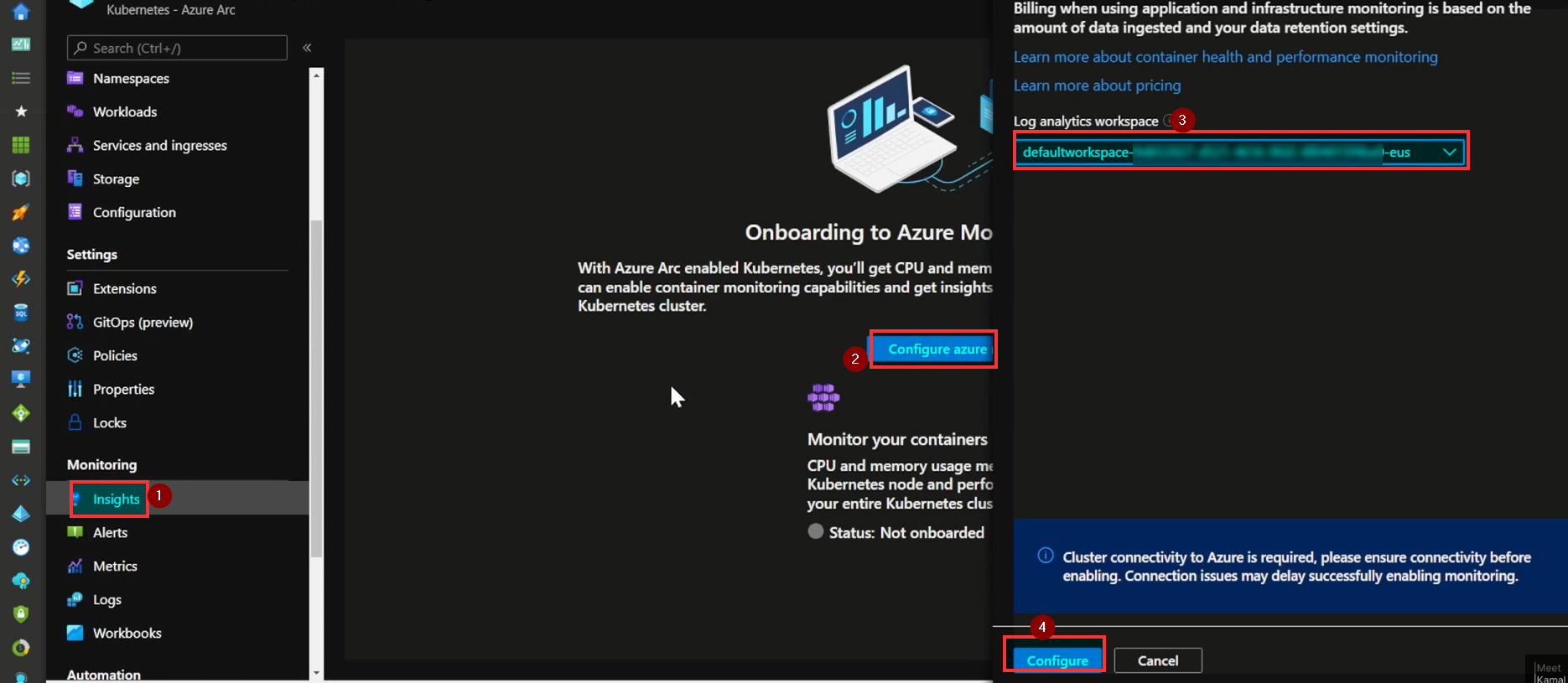
Here we can monitor all the pods and nodes information with the their CPU while clicking on reports