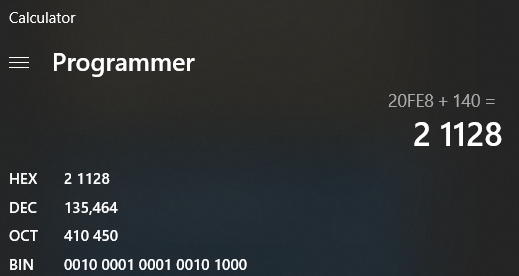
Can someone explain to me how you read these memory addresses? I used cheat engines pointer scanner function in order to obtain the pointer that will always point to my guns ammo address. This is required because the address of my ammo changes every time I load up assault cube and obtaining the original pointer ensures I can always access that address.
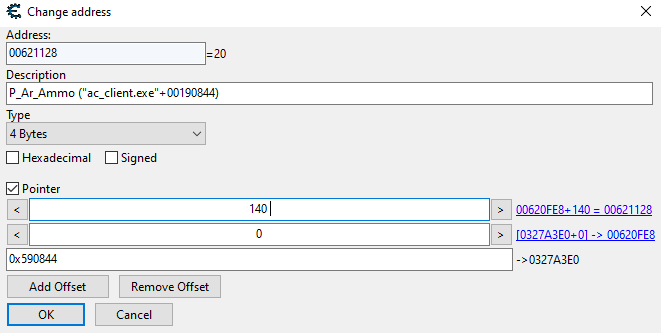
I first managed to determine that ac_client.exe starts at 0x400000 so adding that with the offset of 0x00190844 gives me 0x590844 which is the main static address. Then in that picture above you can see that 0x590844 just points to 0x0327A3E0. Then we can see that we are adding an offset of 0 then seeing where that points to which seems to be 0x00620FE8. Now here is where I am lost how does adding 0x00620FE8 with 140 aka 0x8C ever equal 0x00621128? Because I am getting 0x621074 from my calculations. I am trying to figure out how to get to 0x00621128 when starting at 0x590844 so I can replicate it inside of my C project by using ReadProcessesMemory but I cant seem to figure out where they are getting this value from. At the top I can see that 0x00621128 is the address that contains my guns ammo since shooting my gun changes that 20 value so I know this is what I need. Does anyone know the problem I am having here?
CodePudding user response:
140 is not 0x8C , it is 0x140, this is all in hex, it doesn't need to be converted again to hex