I need to get all the resources referenced by the action per each AWS event record. I use Python and cloudaux/boto.
The documentation states a "resources" field: 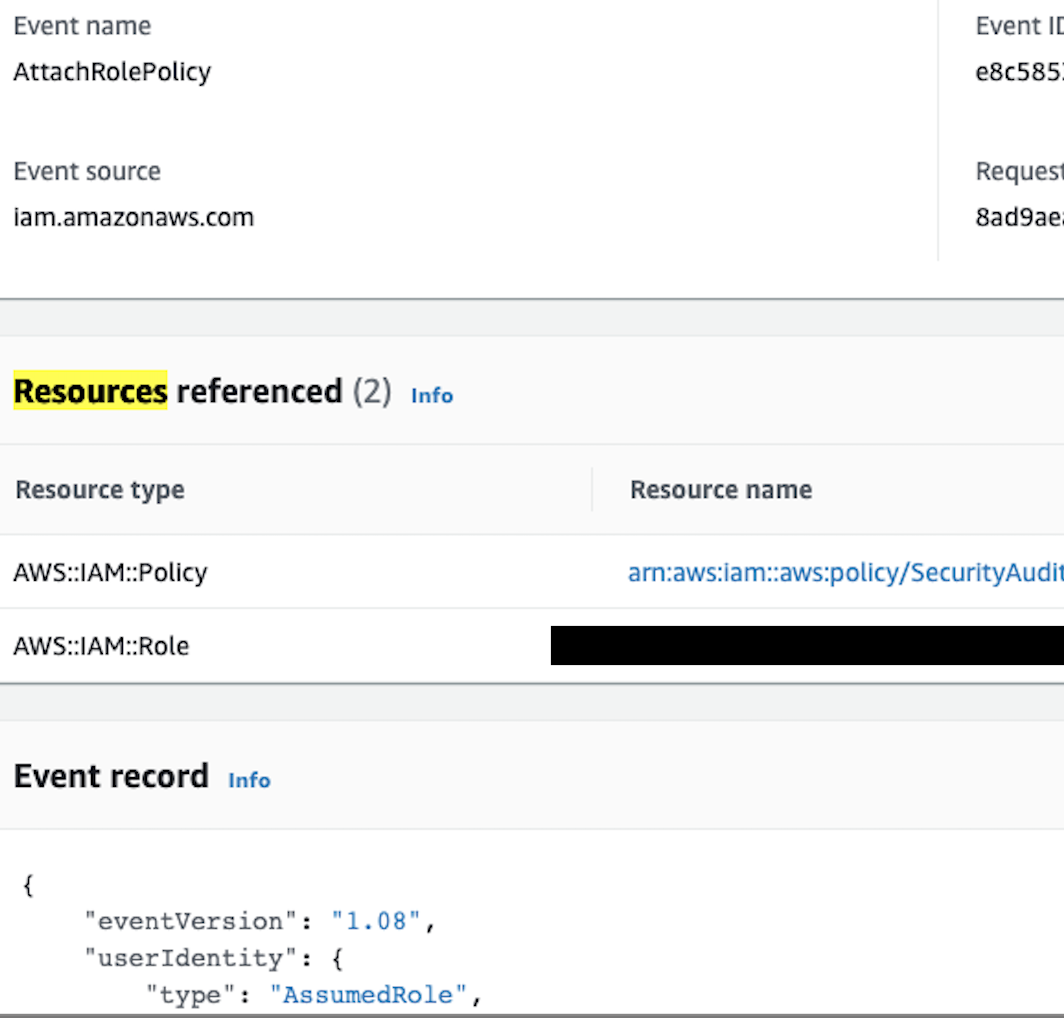
CodePudding user response:
The CloudTrail LookupEvents API has resources for each event (where it is available) in the response. You will need to set LookupAttributes in the request body if you want to filter for specific event(s) in the response.
Here is a sample request/response (this was generated using the CLI, but it should be similar with API/boto3):
aws cloudtrail lookup-events --lookup-attributes AttributeKey=EventName,AttributeValue=AttachRolePolicy
{
"Events": [
{
"EventId": "aaaa-aaaa-aaa",
"EventName": "AttachRolePolicy",
"ReadOnly": "false",
"AccessKeyId": "AAAAAAAAA",
"EventTime": "2022-12-12T04:55:30 00:00",
"EventSource": "iam.amazonaws.com",
"Username": "aaaa",
"Resources": [
{
"ResourceType": "AWS::IAM::Policy",
"ResourceName": "arn:aws:iam::aws:policy/AutoScalingConsoleReadOnlyAccess"
},
{
"ResourceType": "AWS::IAM::Role",
"ResourceName": "SampleRole"
}
],
"CloudTrailEvent": "{\"eventVersion\":\"1.08\",\"userIdentity\":{\"type\":\"IAMUser\",\"principalId\":\"AAAAAAAAA\",\"arn\":\"arn:aws:iam::1234567890:user/AAAAAAAAA\",\"accountId\":\"1234567890\",\"accessKeyId\":\"AAAAAAAAA\",\"userName\":\"kaustubh\",\"sessionContext\":{\"sessionIssuer\":{},\"webIdFederationData\":{},\"attributes\":{\"creationDate\":\"2022-12-12T04:52:13Z\",\"mfaAuthenticated\":\"true\"}}},\"eventTime\":\"2022-12-12T04:55:30Z\",\"eventSource\":\"iam.amazonaws.com\",\"eventName\":\"AttachRolePolicy\",\"awsRegion\":\"us-east-1\",\"sourceIPAddress\":\"AWS Internal\",\"userAgent\":\"AWS Internal\",\"requestParameters\":{\"roleName\":\"SampleRole\",\"policyArn\":\"arn:aws:iam::aws:policy/AutoScalingConsoleReadOnlyAccess\"},\"responseElements\":null,\"requestID\":\"aaaa-aaaa-aaa\",\"eventID\":\"aaaa-aaaa-aaa\",\"readOnly\":false,\"eventType\":\"AwsApiCall\",\"managementEvent\":true,\"recipientAccountId\":\"1234567890\",\"eventCategory\":\"Management\",\"sessionCredentialFromConsole\":\"true\"}"
}
]
}
