I have created app registration in AD, created client secret and exposed the API. I have created App Role and added permissions (additional permissions to the default graph user read). I also have added a scope.
When I do the request
curl --location --request POST 'https://login.microsoftonline.com/<tenant id>/oauth2/v2.0/token' \
--header 'Content-Type: application/x-www-form-urlencoded' \
--data-urlencode 'client_id=<application id>' \
--data-urlencode 'client_secret=<secret>' \
--data-urlencode 'scope=api://<application id>/.default' \
--data-urlencode 'grant_type=client_credentials'
I get the response containing access_token. However when I decode the token it does not contain any roles, scopes or anything
{
"aud": "api://<application id>",
"iss": "https://sts.windows.net/<tenant id>/",
"iat": 1672241639,
"nbf": 1672241639,
"exp": 1672245539,
"aio": "<>",
"appid": "<application id>",
"appidacr": "1",
"idp": "https://sts.windows.net/<tenant id>/",
"oid": "<>",
"rh": "<>.",
"sub": "<>",
"tid": "<tenant id>",
"uti": "<>",
"ver": "1.0"
}
What is missing?
/oauth2/token returns similar response
{
"aud": "<resource id>",
"iss": "https://sts.windows.net/<tenant id>/",
"iat": 1672241960,
"nbf": 1672241960,
"exp": 1672245860,
"aio": "<>",
"appid": "<application id>",
"appidacr": "1",
"idp": "https://sts.windows.net/<tenant id>/",
"oid": "<>",
"rh": "<>",
"sub": "<>",
"tenant_region_scope": "EU",
"tid": "<tenant id>",
"uti": "<>",
"ver": "1.0",
"xms_tdbr": "EU"
}
CodePudding user response:
I tried to reproduce the same in my environment via Postman and got below results:
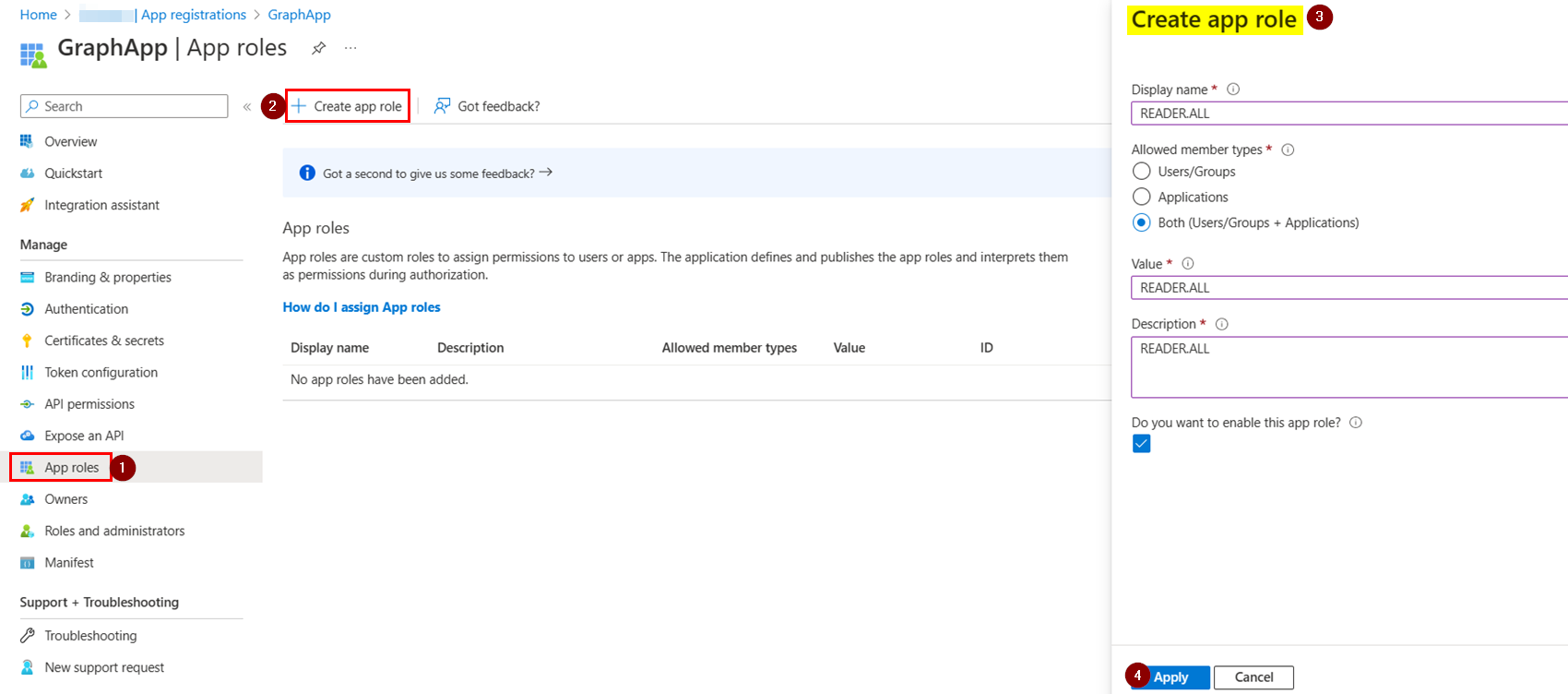
I registered one Azure AD application and created App role named READER.ALL like below:
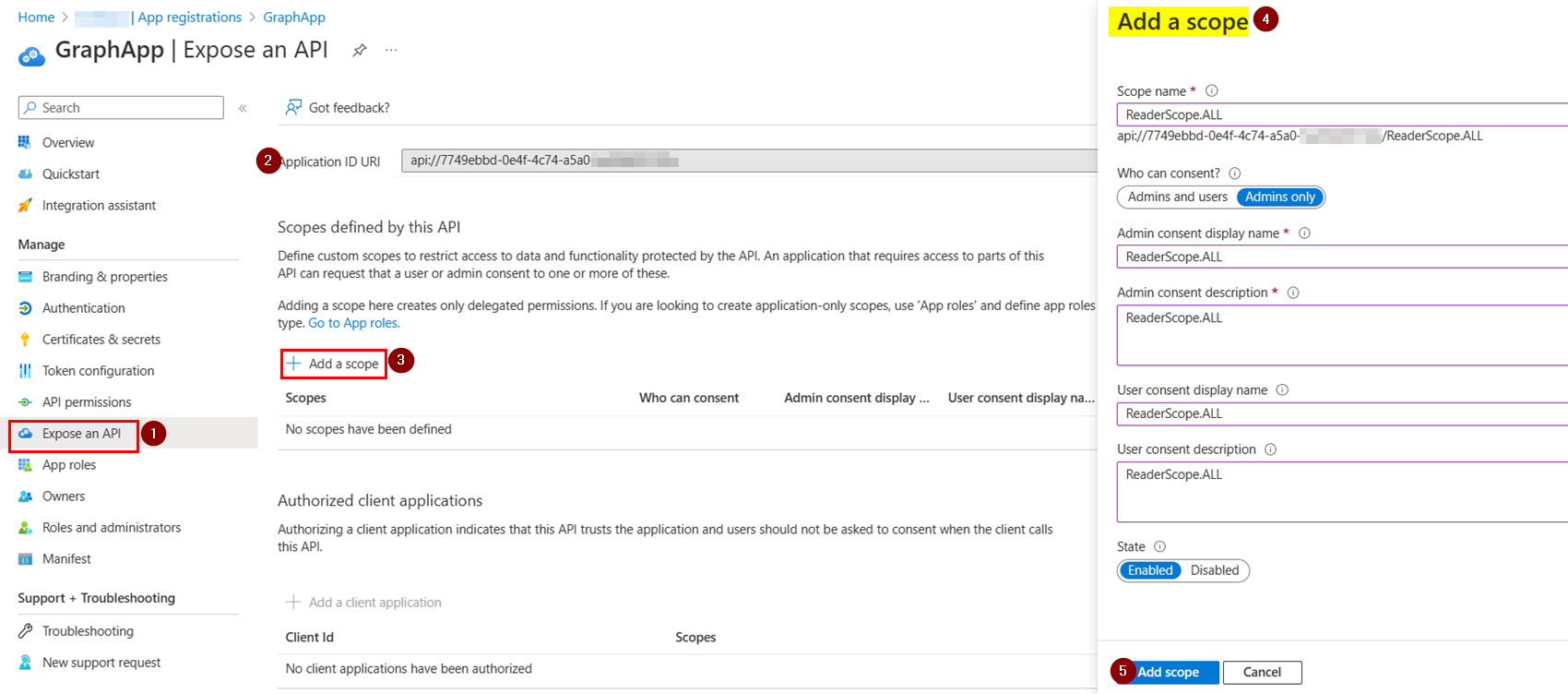
Now I exposed one API named ReaderScope.ALL same as you like below:
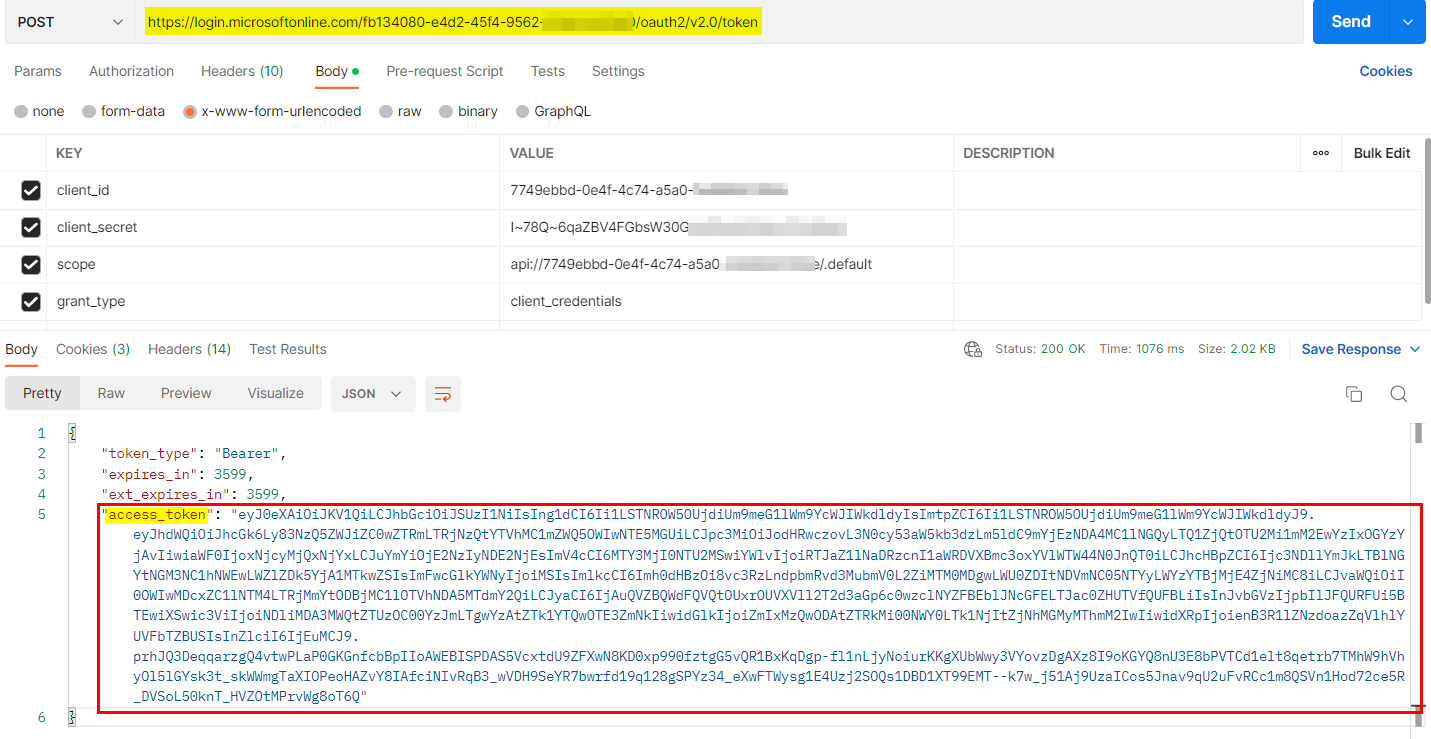
Now I generated the token using Client credentials flow via Postman with below parameters:
POST https://login.microsoftonline.com/<tenantID>/oauth2/v2.0/token
client_id: <appID>
client_secret: <secret>
scope: api://<appID>/.default
grant_type:client_credentials
Response:
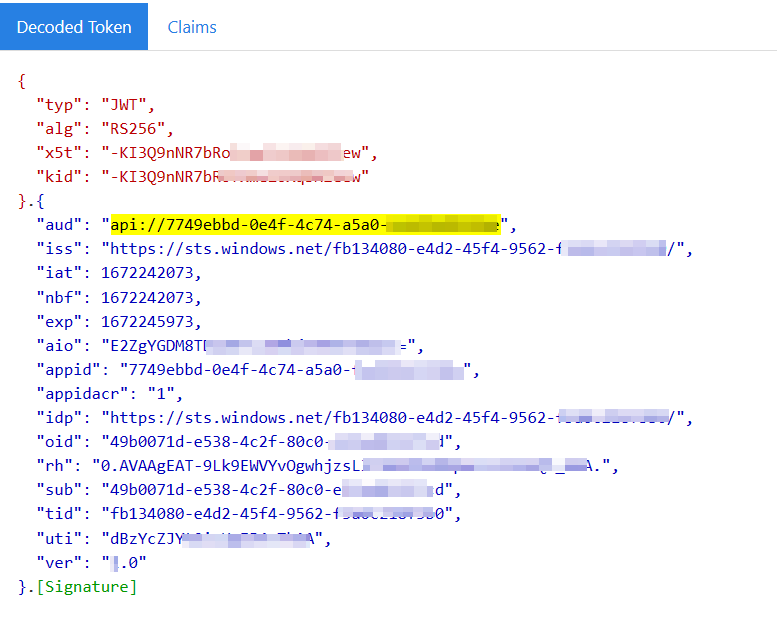
When I decoded the token, I did not find roles claim same as you like below:
To get roles claim in the token, you need to add API permission like below:
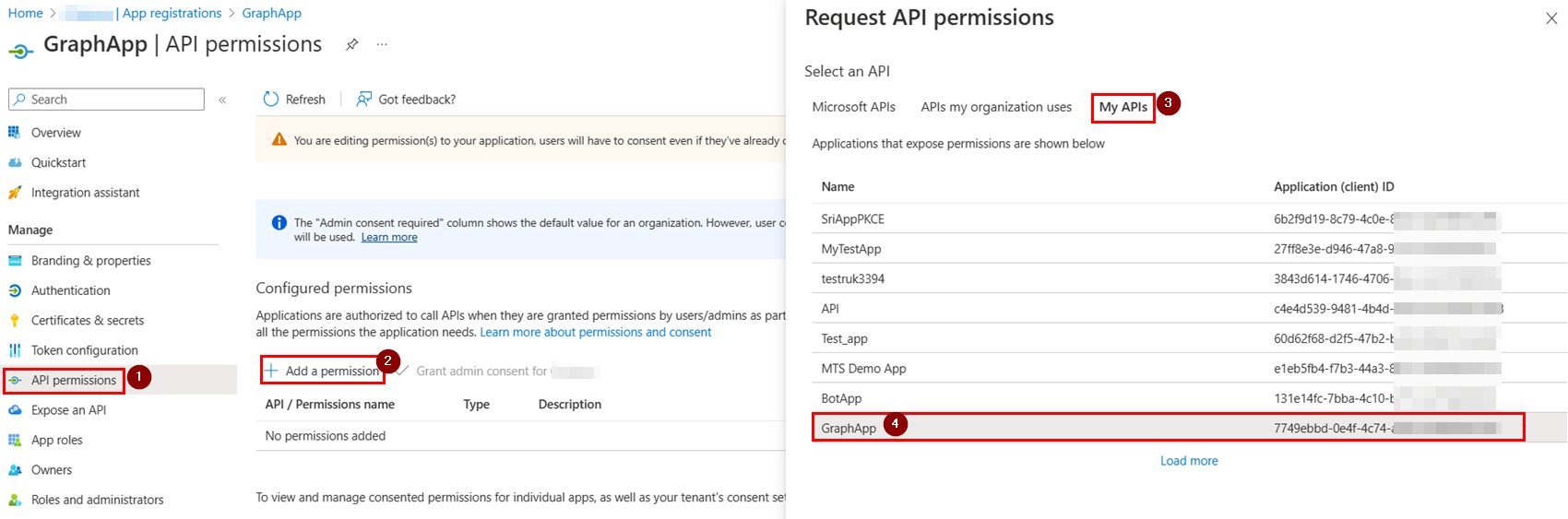
Now, select Application permissions and add the App role like below:
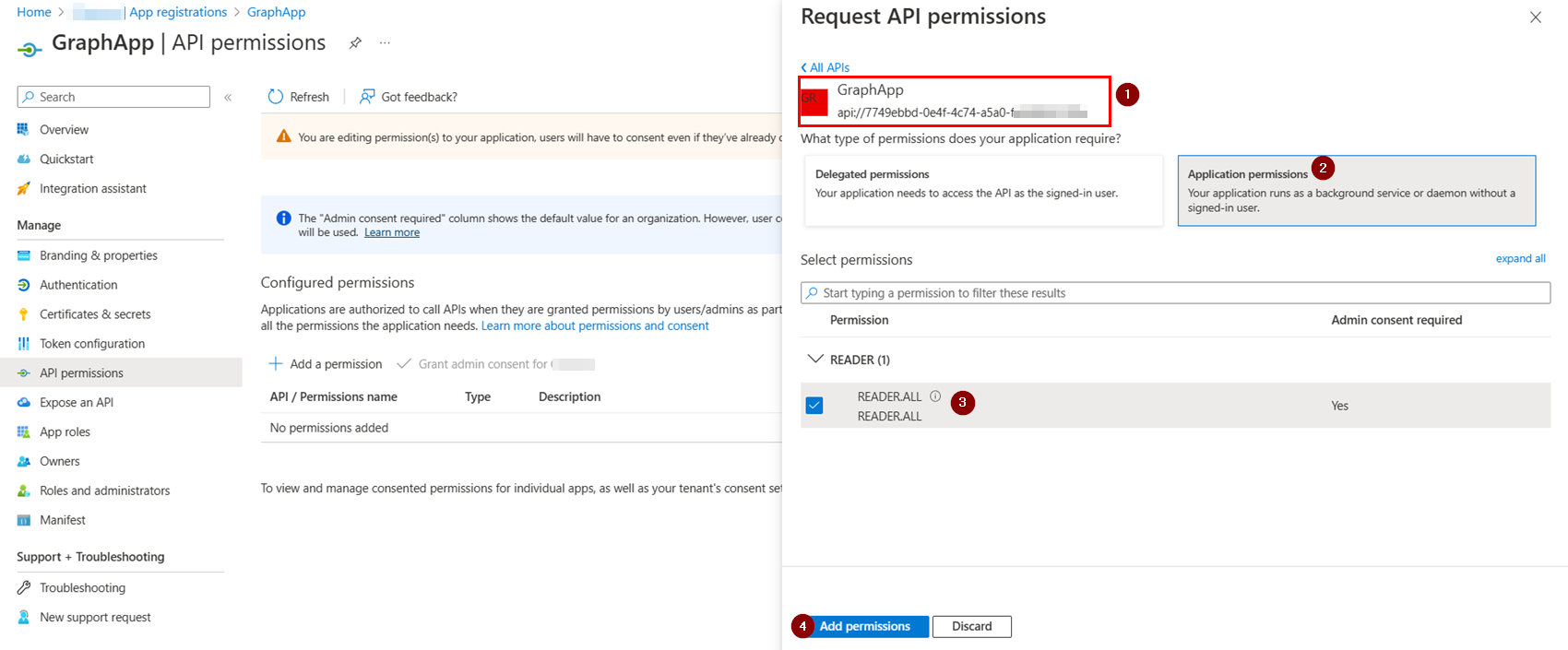
Make sure to grant admin consent to the added permission like below:
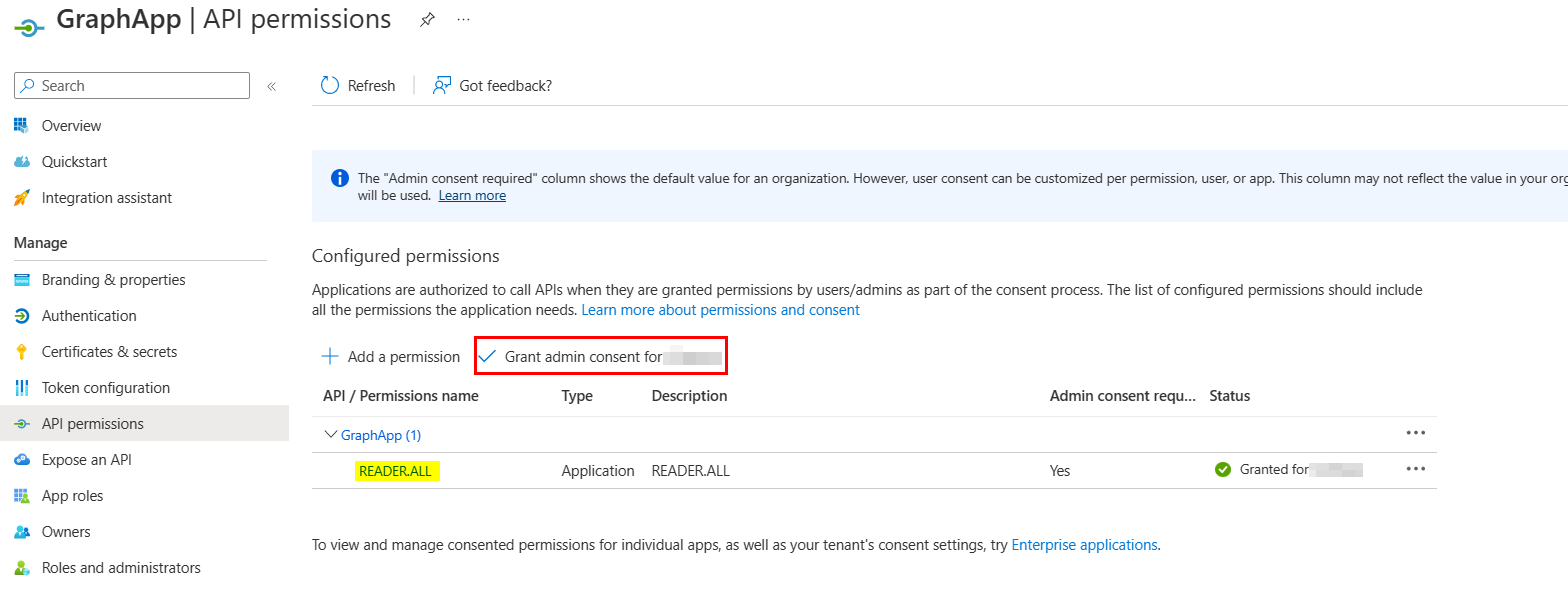
When I generated the token again now and decoded it, I got roles claim successfully like below:
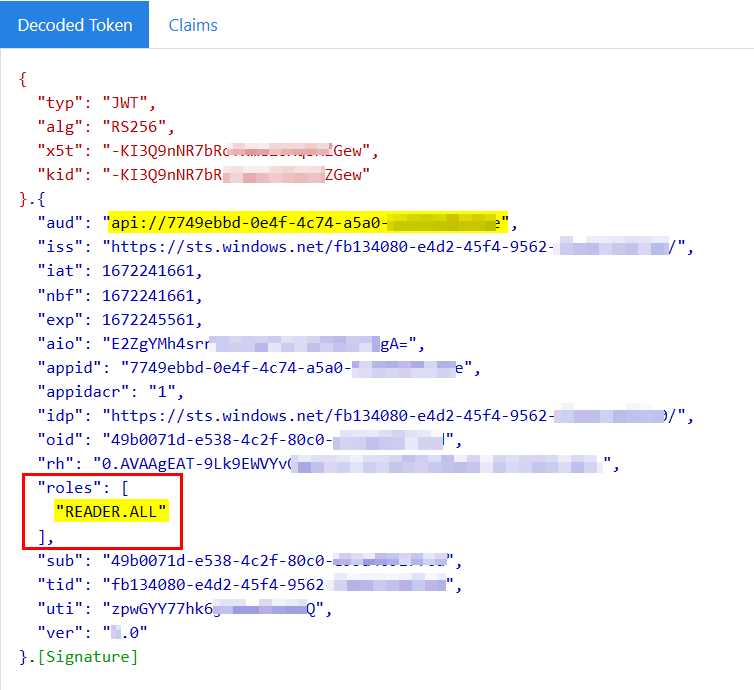
You will get only Application permissions in roles claim while using client credentials flow.
To get Delegated permissions in scp claim, you need to use interactive flows like authorization code flow etc.
