I am trying to build a pipeline which is capable of deploying environments for multiple customers. I have the following structure
- Azure Vault with secrets names in this form:
customerName-customerEnvironmentType-secretName - release pipeline with these steps. It is a multi configuration type job where it creates a job for each customer in a list
- Get secrets from vault using filter: customerName-customerEnvironmentType-secretName
- Bash print env
env:sortand print secret (should result in **** in the logs). The bash script has been added below
The customerName-customerEnvironmentType part of the secret name is put into a variable for reuse. What I am trying to do is to get the vault secret based on the customer name and environment type. The bash script is as follows.
#!/bin/bash
env | sort
echo "FULL_NAME: $(FULL_NAME)" # This prints customerName-customerEnvironmentType
echo "normal usage: $(customerName-customerEnvironmentType-secretName)" # This works and prints ***, but this wouldn't be dynamic and would only work for one customer
# Some options I tried, all of them do not resolve. Some of them don't even resolve the FULL_NAME variable
echo "variables['customerName-customerEnvironmentType-secretName']"
echo "${{ variables['FULL_NAME'] }}"
echo "${{ variables.FULL_NAME }}"
echo "$($(FULL_NAME)-secretName)"
echo "$(${{ variables.FULL_NAME }}-secretName)"
echo "variables['$(FULL_NAME)-secretName']"
echo "$(variables['$(FULL_NAME)-secretName'])"
echo "$[variables['$(FULL_NAME)-secretName']]"
Is there a better way of doing this of maybe another way of variable substitution that would work?
logs: Azure vault build step
2022-12-27T13:38:38.0903674Z ##[section]Starting: Azure Key Vault: customer-environments
2022-12-27T13:38:38.0909613Z ==============================================================================
2022-12-27T13:38:38.0909898Z Task : Azure Key Vault
2022-12-27T13:38:38.0910115Z Description : Download Azure Key Vault secrets
2022-12-27T13:38:38.0910336Z Version : 2.211.1
2022-12-27T13:38:38.0910524Z Author : Microsoft Corporation
2022-12-27T13:38:38.0910836Z Help : https://docs.microsoft.com/azure/devops/pipelines/tasks/deploy/azure-key-vault
2022-12-27T13:38:38.0911185Z ==============================================================================
2022-12-27T13:38:38.2801948Z SubscriptionId: hidden-for-security.
2022-12-27T13:38:38.2804271Z Key vault name: customer-environments.
2022-12-27T13:38:38.2810602Z Downloading secrets using: hidden-for-security.
2022-12-27T13:38:38.8860681Z Number of secrets found in customer-environments: 8
2022-12-27T13:38:38.8900028Z Number of enabled and unexpired secrets found in customer-environments: 8
2022-12-27T13:38:38.8909999Z Downloading secret value for: customerName-customerEnvironmentType-secretName.
.... there where more here, but i have hidden them
2022-12-27T13:38:39.0434461Z ##[section]Finishing: Azure Key Vault: customer-environments
Bash build step
2022-12-27T13:38:39.7977754Z ##[section]Starting: Bash Script
2022-12-27T13:38:39.7990665Z ==============================================================================
2022-12-27T13:38:39.7991040Z Task : Bash
2022-12-27T13:38:39.7991348Z Description : Run a Bash script on macOS, Linux, or Windows
2022-12-27T13:38:39.7991674Z Version : 3.211.0
2022-12-27T13:38:39.7991955Z Author : Microsoft Corporation
2022-12-27T13:38:39.7992334Z Help : https://docs.microsoft.com/azure/devops/pipelines/tasks/utility/bash
2022-12-27T13:38:39.7992749Z ==============================================================================
2022-12-27T13:38:40.0194291Z Generating script.
2022-12-27T13:38:40.0198418Z ========================== Starting Command Output ===========================
2022-12-27T13:38:40.0202702Z [command]/usr/bin/bash /home/vsts/work/_temp/6ad51bf7-2673-449a-9e74-66b2bb6abb19.sh
... removed the output of env | sort for security reasons
2022-12-27T13:38:40.0288018Z FULL_NAME: customerName-customerEnvironmentType
2022-12-27T13:38:40.0298702Z normal usage: ***
2022-12-27T13:38:40.0299290Z variables['customerName-customerEnvironmentType-secretName']
2022-12-27T13:38:40.0299794Z
2022-12-27T13:38:40.0300226Z
2022-12-27T13:38:40.0301018Z /home/vsts/work/_temp/6ad51bf7-2673-449a-9e74-66b2bb6abb19.sh: line 11: ${{ variables['FULL_NAME'] }}: bad substitution
2022-12-27T13:38:40.0302092Z /home/vsts/work/_temp/6ad51bf7-2673-449a-9e74-66b2bb6abb19.sh: line 12: ${{ variables.FULL_NAME }}: bad substitution
2022-12-27T13:38:40.0304197Z /home/vsts/work/_temp/6ad51bf7-2673-449a-9e74-66b2bb6abb19.sh: line 13: customerName-customerEnvironmentType-secretName: command not found
2022-12-27T13:38:40.0305052Z /home/vsts/work/_temp/6ad51bf7-2673-449a-9e74-66b2bb6abb19.sh: line 14: ${{ variables.FULL_NAME }}-secretName: bad substitution
2022-12-27T13:38:40.0305862Z variables['customerName-customerEnvironmentType-secretName']
2022-12-27T13:38:40.0306661Z /home/vsts/work/_temp/6ad51bf7-2673-449a-9e74-66b2bb6abb19.sh: line 15: variables[customerName-customerEnvironmentType-secretName]: command not found
2022-12-27T13:38:40.0307284Z
2022-12-27T13:38:40.0308101Z /home/vsts/work/_temp/6ad51bf7-2673-449a-9e74-66b2bb6abb19.sh: line 16: 'customerName-customerEnvironmentType-secretName': syntax error: operand expected (error token is "'customerName-customerEnvironmentType-secretName'")
2022-12-27T13:38:40.0337412Z ##[error]Bash exited with code '1'.
2022-12-27T13:38:40.0352993Z ##[section]Finishing: Bash Script
CodePudding user response:
I tested in my pipeline and it worked fine. Here’s yaml sample:
variables:
- name: FULL_NAME
value: customerName-customerEnvironmentType
steps:
- task: AzureKeyVault@2
inputs:
azureSubscription: ‘your subscription‘
KeyVaultName: ‘your key vault name’
SecretsFilter: '*'
RunAsPreJob: true
- script: |
echo "FULL_NAME: $(FULL_NAME)"
echo "normal usage: $(customerName-customerEnvironmentType-secretName)"
# get the vault secret based on the customer name and environment type
echo $(${{ variables.FULL_NAME }}-secretName)
displayName: 'Run a multi-line script'
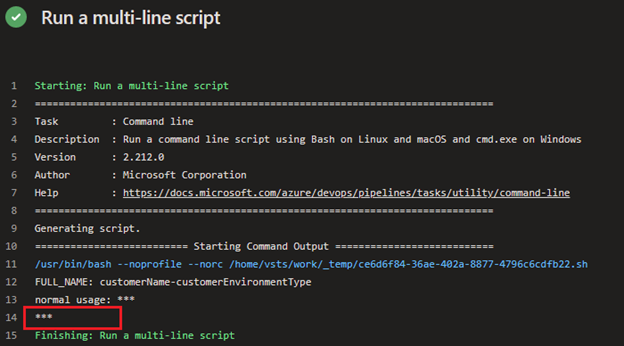
RESULT
BTW it seems like logs in a wetransfer link is private, i have no access to it, you can provide plain text or make it public.
CodePudding user response:
Azure Release pipelines seems to not support variables in variables at the moment.
Found an alternative. By using the azure cli to get the secrets and store them in secret output variables. This seems to behave similar to when the Azure vault step gets the variables. The difference is that I can now controll what they are called.
# Azure CLI bash step
# Save password secrets base64 encoded
NAME_OF_SECRET_WITHOUT_CUSTOMER_SPECIFIC_NAMING=$(az keyvault secret show --vault-name some-vault --name some-secret | jq -r '.value' | base64)
echo "##vso[task.setvariable variable=NAME_OF_SECRET_WITHOUT_CUSTOMER_SPECIFIC_NAMING;isOutput=true;issecret=true]$NAME_OF_SECRET_WITHOUT_CUSTOMER_SPECIFIC_NAMING"
# Other bash task
# Note: Under output variables in de pipeline builder for the CLI step, I added the the VAULT_ prefix. This is added to the front of the variable. If you don't do this, I am not sure if you need something else in front of it.
echo "$(VAULT_NAME_OF_SECRET_WITHOUT_CUSTOMER_SPECIFIC_NAMING)" <- logs *** because it is a secret