1. Will continue to brute force network port 22 other root password, has been trying to log in
2. The process name is random letters such as ualDvKdU
Part 3. The machine can be found on the planning task in the script, the script in base64 encryption, still use chattr lock file, the script will exist in/root/. XXX. Sh and/opt/XXX. Sh
4. General viruses have two random processes, names are not regular, one another do not take up 100% CPU resources
5. Most of the machine process through the analysis of the lsof command basic could not find the file is called
6. The virus process can be in/TMP/. X11 - Unix/directory production file name for 11 01 22, writing is a process inside the PID
My response to
PermitRootLogin no
Systemctl stop crond & amp; & Crontab -e
Chmod 000/usr/local/bin/curl & amp; & Chattr + I/usr/local/bin/curl
Chmod 000/usr/bin/curl & amp; & Chattr + I/usr/bin/curl
CD/TMP/X11 - Unix & amp; & Rm - rf 00 11 22
Chmod 400/TMP/X11 - Unix & amp; & Chattr + I/TMP/X11 - Unix
Mv/usr/bin/chattr/usr/bin/bak chattr
The/usr/bin/tracepath/usr/sbin/tracepath
Chattr - I/root/. Systemd - service. Sh & amp; & Echo & gt;/root/. Systemd - service. Sh & amp; & Chmod 000/root/. Systemd - service. Sh & amp; & Chattr + I/root/. Systemd - service. Sh & amp; & Chattr - I/opt/systemd - service. Sh & amp; & Echo & gt;/opt/systemd - service. Sh & amp; & Chmod 000/opt/systemd - service. Sh & amp; & Chattr + I/opt/systemd - service. Sh & amp; & Kill 9 ` cat/TMP/X11 Unix/11 ` & amp; & Kill 9 ` cat/TMP/X11 Unix/01 `
Rm - rf/TMP/X11 - Unix/01/TMP/X11 - Unix/11/TMP/. X11 Unix/22 & amp; & Chmod 000/TMP/X11 - Unix & amp; & Chattr + I/TMP/X11 - Unix
Through the above command and I change the SSH port number basic had taken control of the virus, process started, no longer
Two months after the virus was found in the Intranet, virus reform the script name and other basic routines in
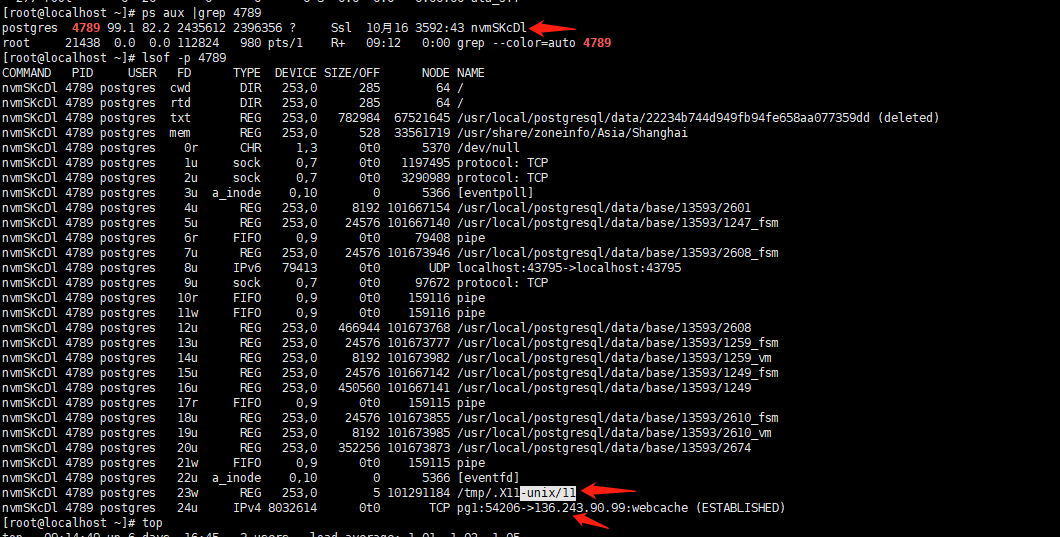
This time I use lsof command found the virus on the part of the machine and postgres database, please analyse why associated with a database, the database security vulnerabilities?
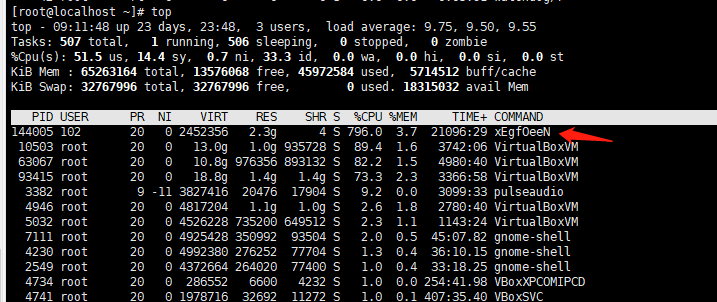
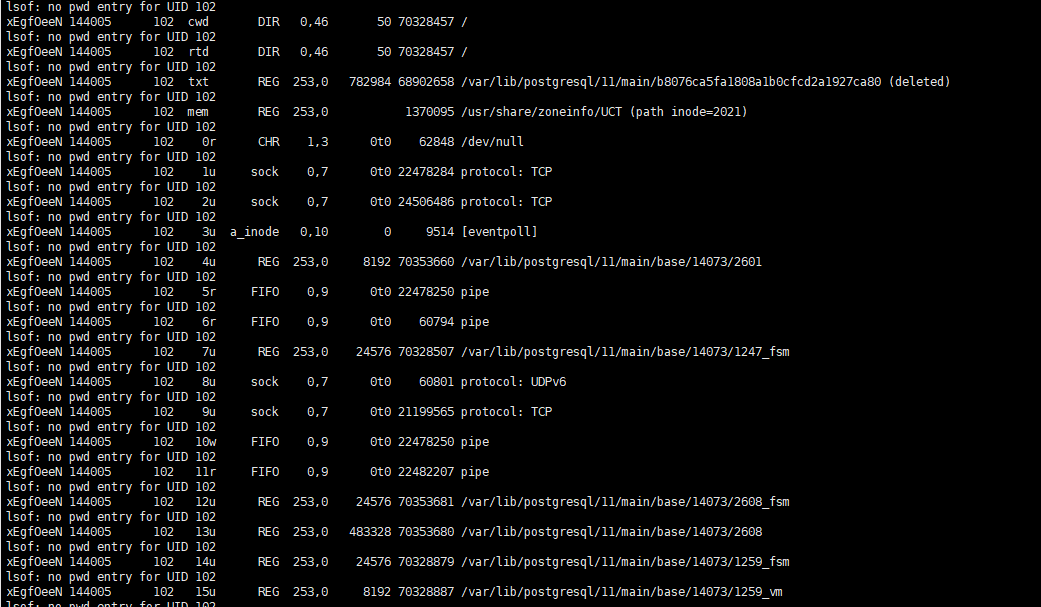
Here are two screenshots from infected machines
Mining process has an IP networks outside pg1:54206 - & gt; 136.243.90.99: webcache (ESTABLISHED)