Zookeeper acts as a server and configured with keystore, which has server certificate. Certificate chain in my keystore looks like below:
MyIntermediateCert (signed by MyRootCertificate)
MyZookeeperCertificate (signed by MyIntermediateCert)
Another parameter defined is truststore, in which I have only root CA MyRootCertificate.
While zk is starting I see in logs that external connection is configured with TLS everything is fine, however when nodes of zk trying to build quorum and try communicate with each other - i receive classic TLS exception while TLS handshake between client and server.
Exception caught
io.netty.handler.codec.DecoderException: javax.net.ssl.SSLHandshakeException: PKIX path building failed: sun.security.provider.certpath.SunCertPathBuilderException: unable to find valid certification path to requested target
at io.netty.handler.codec.ByteToMessageDecoder.callDecode(ByteToMessageDecoder.java:468)
at io.netty.handler.codec.ByteToMessageDecoder.channelRead(ByteToMessageDecoder.java:276)
at io.netty.channel.AbstractChannelHandlerContext.invokeChannelRead(AbstractChannelHandlerContext.java:379)
at io.netty.channel.AbstractChannelHandlerContext.invokeChannelRead(AbstractChannelHandlerContext.java:365)
at io.netty.channel.AbstractChannelHandlerContext.fireChannelRead(AbstractChannelHandlerContext.java:357)
at io.netty.channel.DefaultChannelPipeline$HeadContext.channelRead(DefaultChannelPipeline.java:1410)
at io.netty.channel.AbstractChannelHandlerContext.invokeChannelRead(AbstractChannelHandlerContext.java:379)
at io.netty.channel.AbstractChannelHandlerContext.invokeChannelRead(AbstractChannelHandlerContext.java:365)
at io.netty.channel.DefaultChannelPipeline.fireChannelRead(DefaultChannelPipeline.java:919)
at io.netty.channel.nio.AbstractNioByteChannel$NioByteUnsafe.read(AbstractNioByteChannel.java:163)
at io.netty.channel.nio.NioEventLoop.processSelectedKey(NioEventLoop.java:714)
at io.netty.channel.nio.NioEventLoop.processSelectedKeysOptimized(NioEventLoop.java:650)
at io.netty.channel.nio.NioEventLoop.processSelectedKeys(NioEventLoop.java:576)
at io.netty.channel.nio.NioEventLoop.run(NioEventLoop.java:493)
ssl.quorum.hostnameVerification is false, I don't need hostname verification between nodes.
My expectation was that client sends request to server (call from one node to another), it receives certificate chain which includes server cert and intermediate cert (sign by CA), and this chain is validated in front of my trust store that includes CA.
This CA by the way is self generated by the way.
What I am missing?
CodePudding user response:
I think I found the issue.
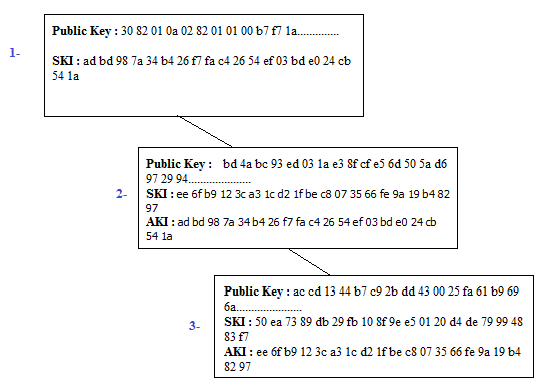
Problem is that my Intermediate Certificate does not include key identifier value in it's AKI extension, which should point to the root CA. It should be something like this: