How would someone go about preventing MITM type attacks against API secrets/ API keys? How does facebook/ instagram protect their users against MITM type hacks?
Do they even protect the users? Or they assume that any possible attacks should be shouldered by users?
CodePudding user response:
Some Context on my Answer
I assume that your question is in the context of mobile apps, thus my answer will show how to protect against a MitM attack for APIs serving mobile apps and how it can be bypassed.
Your Facebook/Instagram Related Questions
How does facebook/ instagram protect their users against MITM type hacks?
Do they even protect the users? Or they assume that any possible attacks should be shouldered by users?
This questions are best answered by an insider at Facebook/Instagram or from a security researcher that have done extensive work on their mobile apps and APIs.
Sorry for not being able to elucidate you here.
Preventing MitM Attacks
How would someone go about preventing MITM type attacks against API secrets/ API keys?
This one I am able to help you with and the quick reply its by using certificate pinning against the certificate public key, and we will go in more detail below.
In a first instance you will want to secure the HTTPS communication channel by configuring the mobile app to only establish a connection with the API, during the TLS handshake, if it presents the certificate issued for its domain and that is known and trusted by the mobile app, ignoring any other that may still be valid as per validation against the certificate trust store of the device. I go into more detail about it and how to implement it on the article I wrote Securing HTTPS with Certificate Pinning:
In order to demonstrate how to use certificate pinning for protecting the https traffic between your mobile app and your API server, we will use the same Currency Converter Demo mobile app that I used in the previous article.
In this article we will learn what certificate pinning is, when to use it, how to implement it in an Android app, and how it can prevent a MitM attack.
What to pin?
From the same article I will quote:
The easiest way to pin is to use the server’s public key or the hash of that public key, The hashed public key is the most flexible and maintainable approach since it allows certificates to be rotated in the server, by signing the new one with the same public key. Thus the mobile app does not have to be updated with a new pin because the hash for the public key of the new certificate will continue to match the pin provided in the network security config file. We will see an example of this later when we talk about how to setup certificate pinning.
Implementing Static Certificate Pinning
The easiest and quick way you can go about implementing static certificate pinning in a mobile app is by using the Mobile Certificate Pinning Generator that accepts a list of domains you want to pin against and generates for you the correct certificate pinning configurations to use on Android and iOS.
Give it a list of domains to pin:
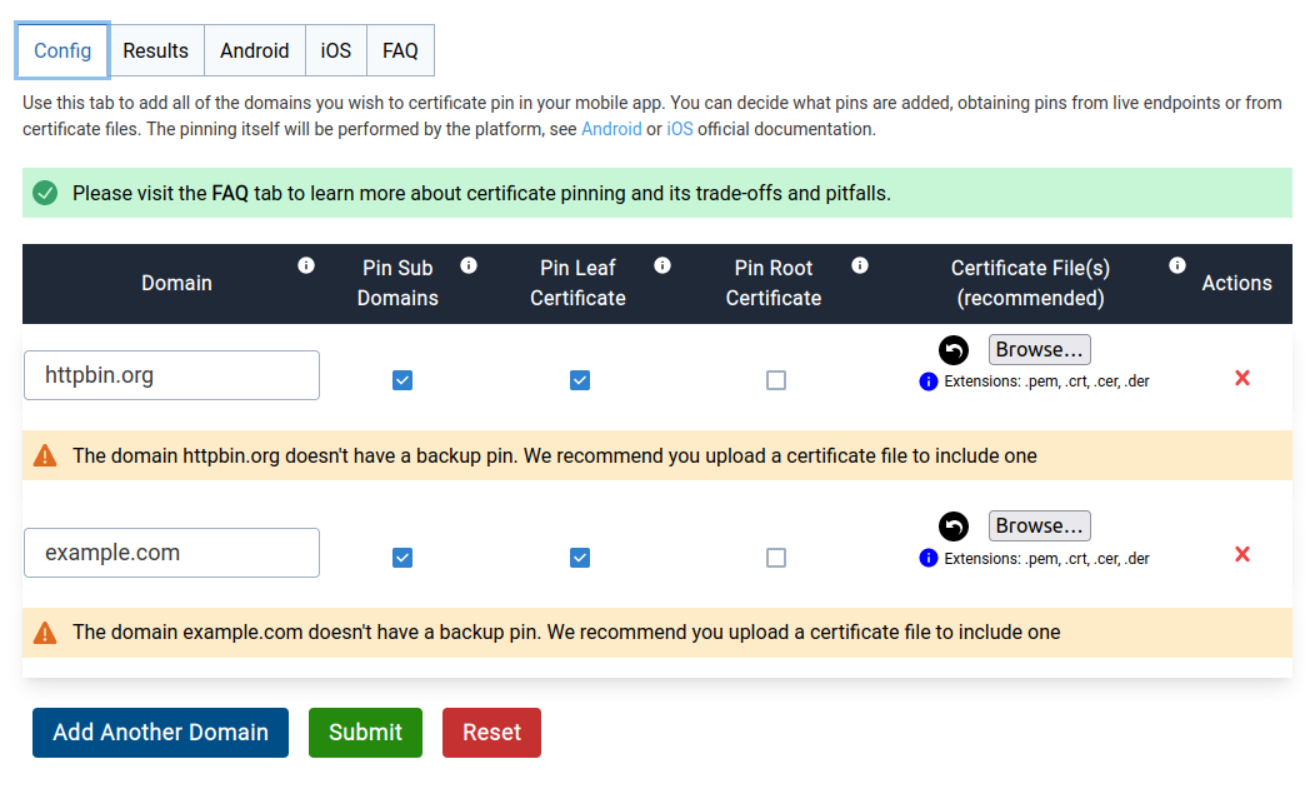
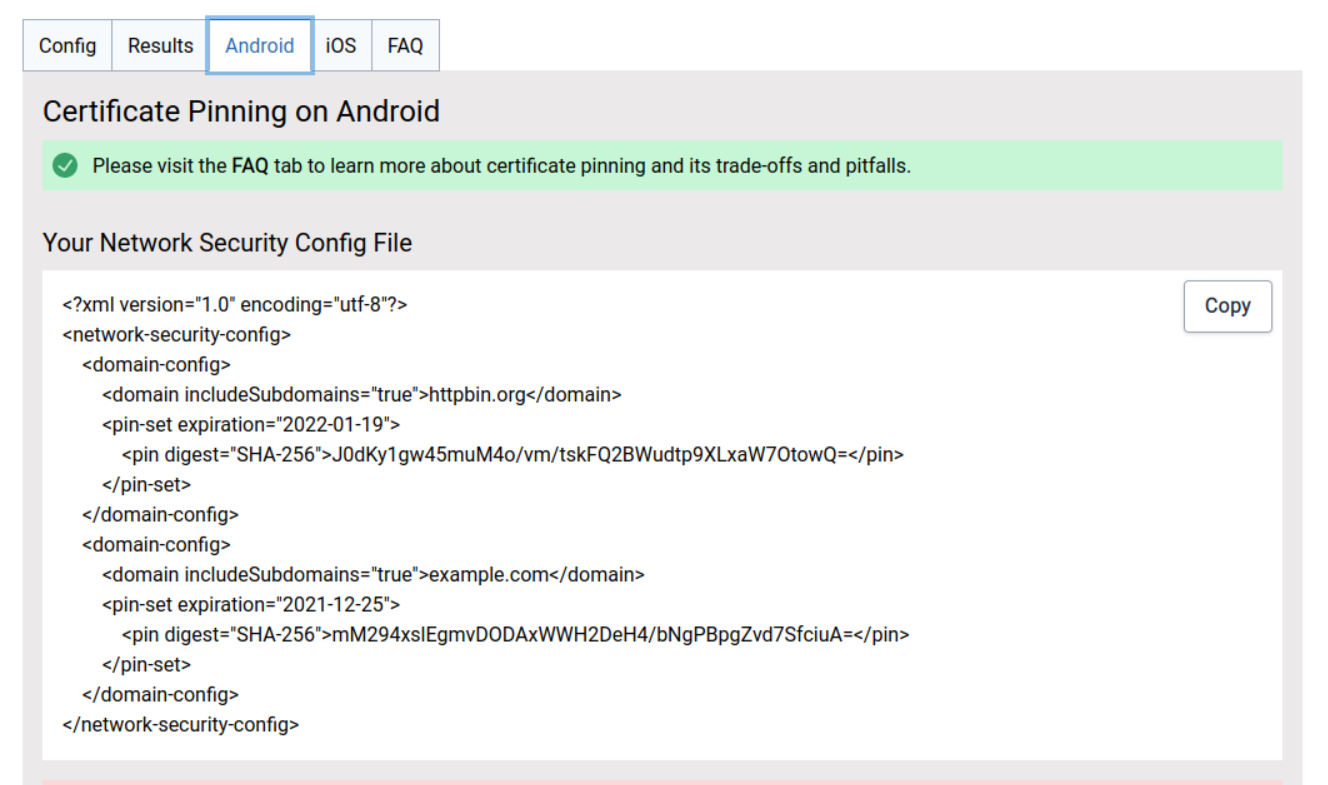
And the tool generates for you the Android configuration:
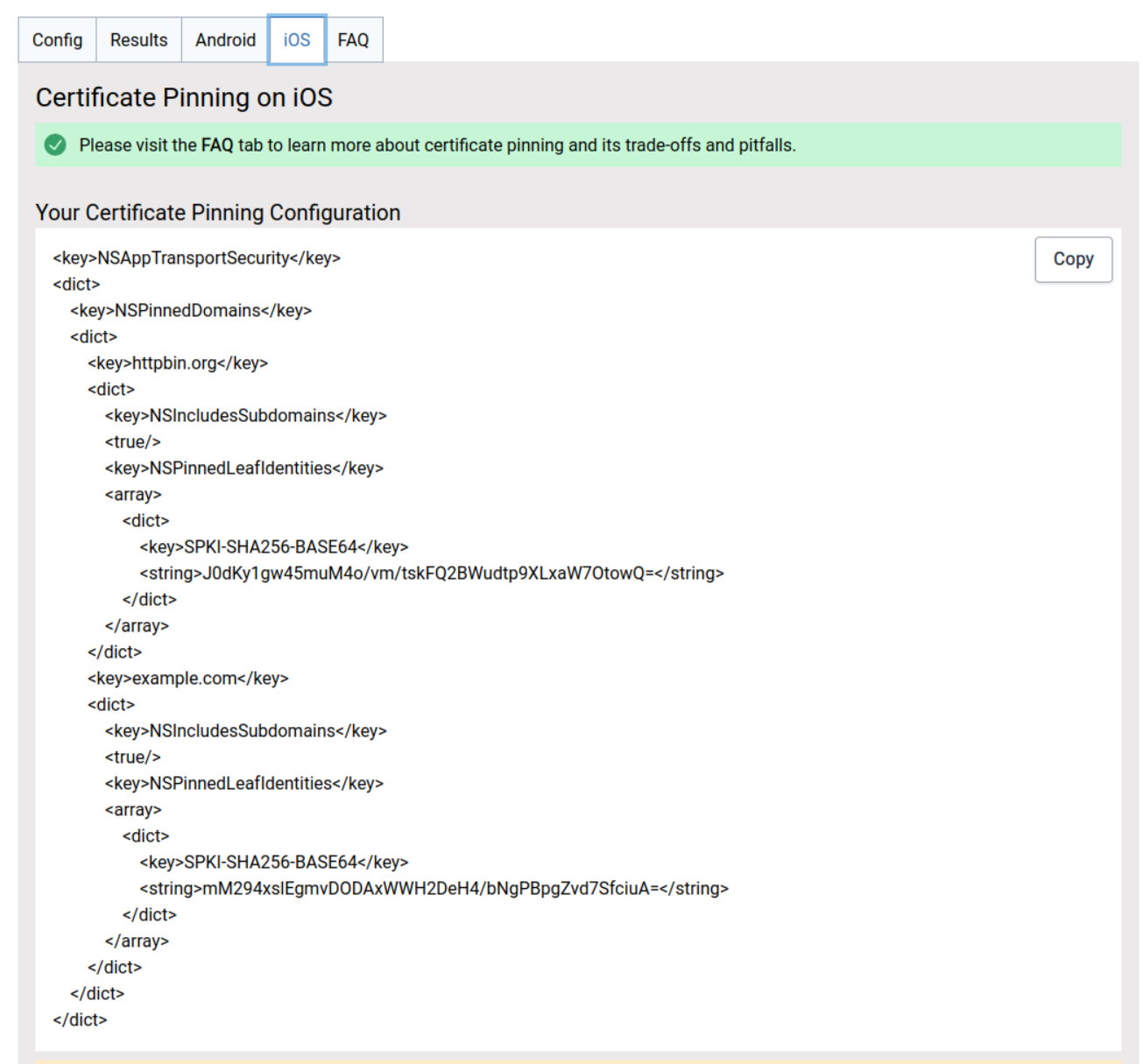
And the iOS configuration too:
The tool even as instructions how to go about adding the configurations to your mobile app, that you can find below the certificate pinning configuration box. They also provide an hands on example Pin Test App for Android and for iOS that are a step by step tutorial.
Bypass Certificate Pinning
It's important that any developer that decides to implement certificate pinning in their mobile apps also understands how it can be bypassed in order to learn the threat model and evaluate if further protections are needed to prevent certificate pinning bypass.
I wrote two articles on how to bypass certificate pinning on Android where you can learn in one of them how to do it by extracting, modifying and repackaging the APK, while in the other article you learn how to use the Frida instrumentation framework to hook at runtime into the mobile app in order to bypass certificate pinning:
Bypassing Certificate Pinning on Android via APK
In this article you will learn how to repackage a mobile app in order to make it trust custom ssl certificates. This will allow us to bypass certificate pinning.
How to Bypass Certificate Pinning with Frida on an Android App:
Today I will show how to use the Frida instrumentation framework to hook into the mobile app at runtime and instrument the code in order to perform a successful MitM attack even when the mobile app has implemented certificate pinning.
Bypassing certificate pinning is not too hard, just a little laborious, and allows an attacker to understand in detail how a mobile app communicates with its API, and then use that same knowledge to automate attacks or build other services around it.
Summary
Despite being possible to bypass certificate pinning I still strongly recommend you to implement it in your mobile app, because it reduces a lot the attack surface of your mobile app.
Being aware of how certificate pinning can be bypassed gives you the insights to decide if further protections are needed to be in place. Dynamic certificate pinning and Runtime Application Self-Protection(RASP) may be the next steps to take in your security ladder.
