Can anyone help me how to write a CLI script to Enable Function Application Authentication to use Microsoft Azure AD ID Provider?
Thanks,
CodePudding user response:
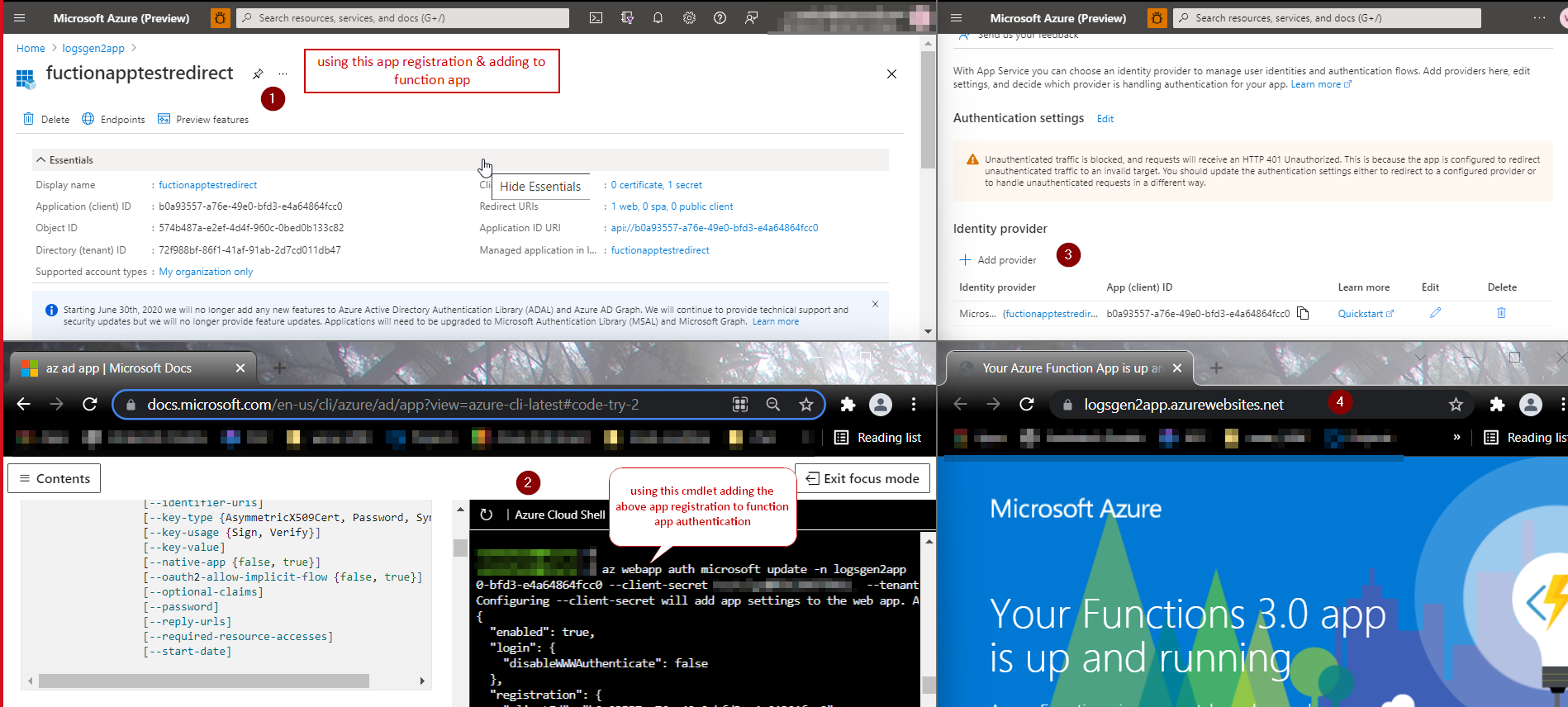
We have tested in our local environment , using the below cmdlets we are able to create Microsoft identity provider authentication for the function app & these cmdlets are working fine.
Below are the steps to be followed:
You Need to create a app registration in AAD & add the required permissions to that app registration using the below cmdlet.
az ad app create --display-name <NameofappRegistration> --password <clientsecret> --reply-urls https://<functionappName>.net/.auth/login/aad/callback --required-resource-accesses @manifest.json
The below resource access will create user.read permission to that app registration
how to declare permission in manifest.json file :
"requiredResourceAccess": [
{
"resourceAppId": "00000003-0000-0000-c000-000000000000",
"resourceAccess": [
{
"id": "e1fe6dd8-ba31-4d61-89e7-88639da4683d",
"type": "Scope"
}
]
}
]
- You need to add identifier-uris/application uri for that app registration.
az ad app update --id <appId/clientId> --identifier-uris api://<clientId>
- Creating the webapp authentication and authorization of the Microsoft identity provider for the function app to that app registration using the below cmdlet
az webapp auth microsoft update -n <functionAppName> -g <ResourceGroupName> --client-id <appRegistrationClientId> --client-secret <appresgistrationPassword> --tenant-id <TenantID>
Sample Output for reference post running the above cmdlets:
Here are the reference CLI cmdlet documentation for creation of Microsoft auth for a webapp & for app registration
