How to add multiple subnets of multiple VNETS to azure ServiceBus firewall dynamically using terraform?
Below is the terraform code. VNETs and subnets is available in the locals section of tf code.
So I have three VNETs (vnet1, vnet2, and vnet3) in azure and each VNET has multiple subnets.
locals {
virtual_network_name1 = "vnet1"
virtual_network_name2 = "vnet2"
virtual_network_name3 = "vnet3"
subnets = {
sub1 : {
subnet1 = "vnet1-subnet1",
subnet2 = "vnet1-subnet2",
subnet3 = "vnet1-subnet3"
},
sub2: {
subnet1 = "vnet2-subnet1",
subnet2 = "vnet2-subnet2",
subnet3 = "vnet2-subnet3"
}
sub3: {
subnet1 = "vnet3-subnet1",
subnet2 = "vnet3-subnet2",
subnet3 = "vnet3-subnet3"
}
}
}
data "azurerm_virtual_network" "vnet" {
name = local.virtual_network_name
resource_group_name = "westy"
}
data "azurerm_subnet" "subnets" {
for_each = local.subnets
name = each.value
resource_group_name = "westy"
virtual_network_name = data.azurerm_virtual_network.vnet.name
}
resource "azurerm_resource_group" "example" {
name = "example-resources"
location = "West Europe"
}
resource "azurerm_servicebus_namespace" "example" {
name = "example-sb-namespace"
location = azurerm_resource_group.example.location
resource_group_name = azurerm_resource_group.example.name
sku = "Premium"
capacity = 1
}
resource "azurerm_servicebus_namespace_network_rule_set" "example" {
namespace_name = azurerm_servicebus_namespace.example.name
resource_group_name = azurerm_resource_group.example.name
default_action = "Deny"
trusted_services_allowed = true
network_rules {
subnet_id = data.azurerm_subnet.subnets
ignore_missing_vnet_service_endpoint = false
}
ip_rules = ["125.123.142.174"]
}
Actually, these are existing VNETs and subnets were already created
I want to iterate over those vnets like with vnet1 iterate the first group of subnets, with vnet2 iterate the second group subnets and same with vnet3. This is how respective subnets are associated with those vnets and add them inside the network block of "azurerm_servicebus_namespace_network_rule_set" resource dynamically using terraform?
Is it possible to achieve?
CodePudding user response:
You can use the below code for your requirement:
provider "azurerm"{
features{}
}
locals {
vnet_list = {
"vnet1" = [{"subnet_name"=[
"subnet1",
"subnet2",
"subnet3"
]
}],
"vnet2" = [{"subnet_name"=[
"subnet1",
"subnet2",
"subnet3"
]
}],
"vnet3" = [{"subnet_name"=[
"subnet1",
"subnet2",
"subnet3"
]
}]
}
vnet = merge([
for vnet_name, vnet in local.vnet_list : {
for subnet in vnet[0].subnet_name :
"${vnet_name}-${subnet}" => {
name = vnet_name
subnet_name = subnet
}
}
]...)
}
data "azurerm_resource_group" "example" {
name = "myresourcegroup"
}
resource "azurerm_servicebus_namespace" "example" {
name = "ansuman-sb-namespace"
location = data.azurerm_resource_group.example.location
resource_group_name = data.azurerm_resource_group.example.name
sku = "Premium"
capacity = 1
}
data "azurerm_subnet" "example"{
for_each = local.vnet
name=each.value.subnet_name
virtual_network_name=each.value.name
resource_group_name=data.azurerm_resource_group.example.name
}
resource "azurerm_servicebus_namespace_network_rule_set" "example" {
namespace_name = azurerm_servicebus_namespace.example.name
resource_group_name = data.azurerm_resource_group.example.name
default_action = "Deny"
trusted_services_allowed = true
dynamic "network_rules" {
for_each=data.azurerm_subnet.example
content{
subnet_id = network_rules.value["id"]
ignore_missing_vnet_service_endpoint = false
}
}
ip_rules = ["125.123.142.174"]
}
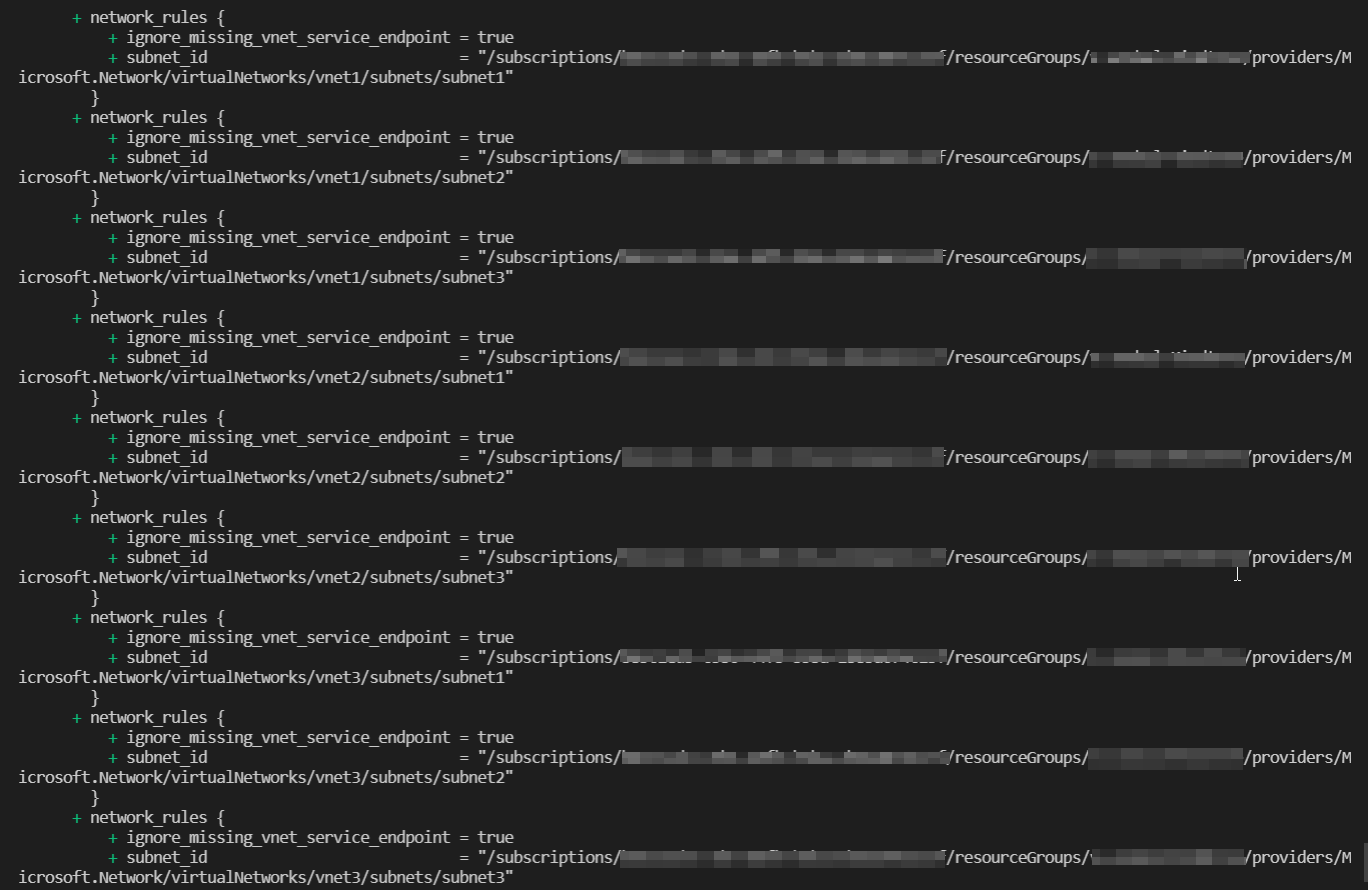
Output:
All the 9 Subnets have been added in the network rule:
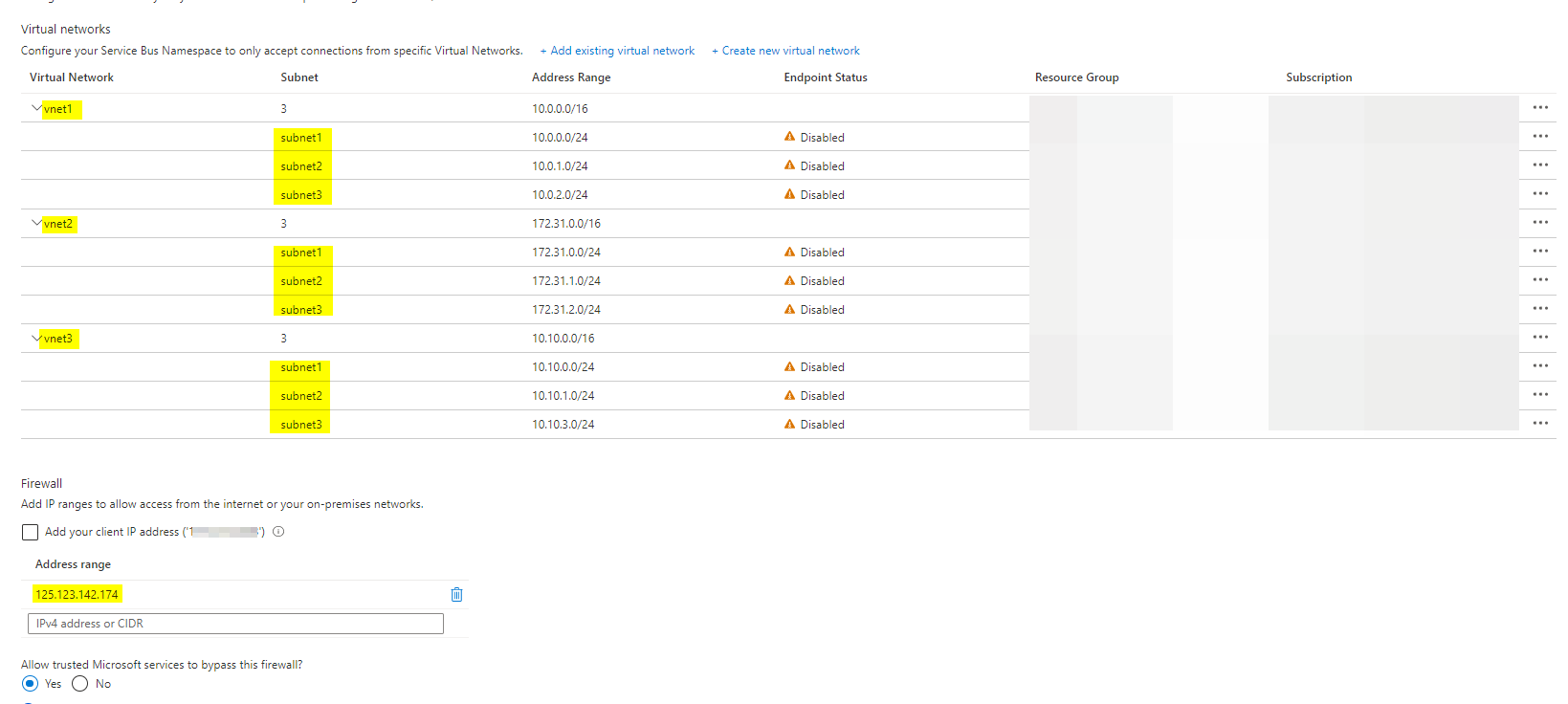
Portal: