I'm an iOS Developer and I have one question about security that I can't answer.
Security experts say that using the "certificate pinning" will make your app more secure (for example against man in the middle attacks).
I agree that with this technique you can guarantee that your app is communicating with your backend (and that no-one "in the middle" can sniff the traffic), but as we are using HTTPS, the traffic is already encrypted, so how could someone see the traffic?
There is one possible way, that you get the certificate of the attacker and you install it on your iPhone, but is this really something that can happen ? Or are other ways to make this kind of attack?
CodePudding user response:
Yes, you need to install a root CA certificate on the iOS device and trust it for making an man-in-the-middle attack on an HTTPS connection used by an iOS app.
But you forget one major case: What happens if the attacker and the iPhone user are the same person? Having access to the transmitted data makes it easier to analyze you app and find potential flaws. So an attacker can install your app on a prepared device, analyze it, find all the mistakes you made and afterwards attack use this knowledge to attack your server(s) and/or your app users.
Another scenario is that people are forced to install root CA certificates may be because the phone is used in a company with own network inspection or at a border control.
CodePudding user response:
HTTPS and Ceritificate Pinning
Security experts say that using the "certificate pinning" will make your app more secure (for example against man in the middle attacks). That a best practice in terms of security in order to avoid the MitM attacks that you already know, but do you know what certificate pinning works?
I know that your question is about iOS but in my article Securing HTTPS with Certificate Pinning on Android you can learn for what certificate pinning is for and why is needed, because this is agnostic of the mobile platform being used. Please read the article and feel free to ignore the part about implementing pinning in Android.
To give you some context I will quote some of the more relevant parts of my article, that will help clarifying your doubts.
Lets' start with the part about why we need Certificate Pinning:
While HTTPS gives you confidentiality, integrity and authenticity in the communication channel between the mobile app and the API server, certificate pinning will protect these same guarantees from being broken.
Let's see two examples from the article on how the HTTPS guarantees can be broken.
First Example:
To prevent trust based assumptions
Incorrectly issuing leaf certificates to the wrong domain names by Root and Intermediate Certificate Authorities (CAs) would allow an attacker to intercept any HTTPS traffic using them, without the end user noticing anything.
Do you think that is very unlike for this to happen? Just take a look to the famous cases of DigiNotar, GlobalSign and Comodo.
Second Example
Another scenario where the HTTPS guarantees are usually broken is when the device is running in hostile environments:
A good example of a hostile environment is public WiFi, where users can be tricked by an attacker into installing a self signed root certificate authority into the trusted store of the device as a requirement for them to have internet for free. This will allow the attacker to perform a MitM attack and intercept, modify or redirect all HTTPS traffic, because the device will now accept all intercept traffic which is now signed by the root CA of the attacker - now trusted by the device.
Both examples will allow for attackers to see the HTTPS encrypted, thus I hope it answers your question:
I agree that with this technique you can guarantee that your app is communicating with your backend (and that no-one "in the middle" can sniff the traffic), but as we are using HTTPS, the traffic is already encrypted, so how could someone see the traffic?
So, HTTPS will encrypted your traffic in transit and certificate pinning will try to prevent it from being decrypted. Wait, did you said try? Yes, because pinning can also be bypassed in a device the attacker controls. I have several articles (1, 2) on it, but on Android, and for iOS it can also be done, and its on my backlog, thus I will update this answer when done.
Possible Attacks to your Mobile App
There is one possible way, that you get the certificate of the attacker and you install it on your iPhone, but is this really something that can happen ? Or are other ways to make this kind of attack?
An attacker will reverse engineer your mobile app in order to understand how everything fits together and will try then to exploit flaws in your logic and security. For example, the attacker can use the MobSF - Mobile Security Framework to statically reverse engineer your mobile app binary:
Mobile Security Framework is an automated, all-in-one mobile application (Android/iOS/Windows) pen-testing framework capable of performing static analysis, dynamic analysis, malware analysis and web API testing.
Attackers will often perform attacks to your code at runtime to modify its behaviour or bypass certificate pinning and a popular tool used for this propose is Frida:
Inject your own scripts into black box processes. Hook any function, spy on crypto APIs or trace private application code, no source code needed. Edit, hit save, and instantly see the results. All without compilation steps or program restarts.
Bear in mind that the attacker can be a legit user of your mobile app trying to bypass some of the limitations of the plan is on in order to get more then what he is entitled to.
Want to Implement Certificate Pinning on iOS?
If you want to go ahead and implement certificate pinning in your iOS mobile app then you can use the Mobile Certificate Pinning Generator free tool to get the iOS configuration generated for you.
First you need to provide the API domains you want to pin:
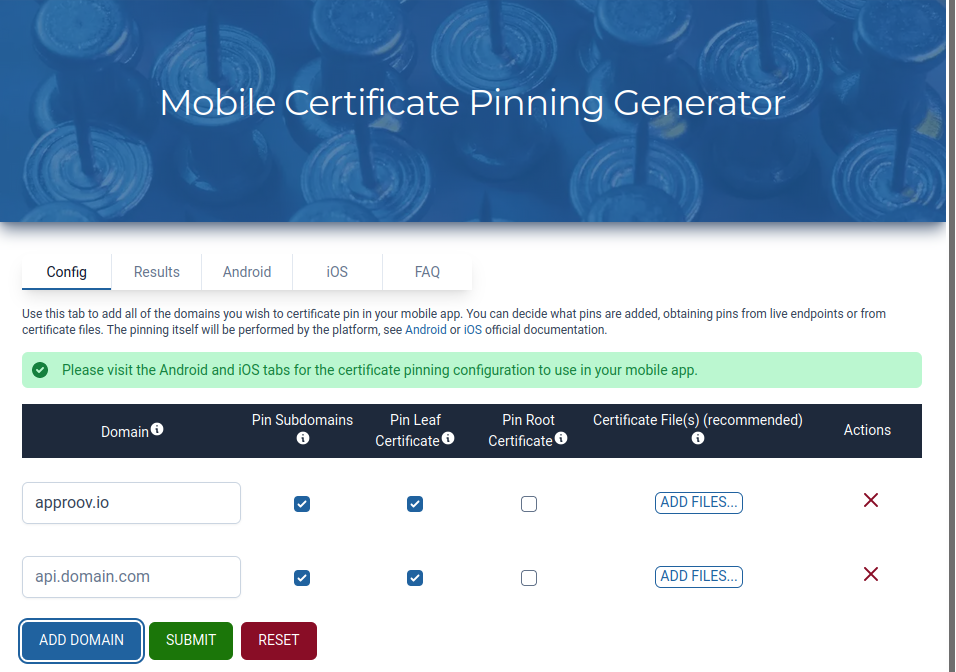
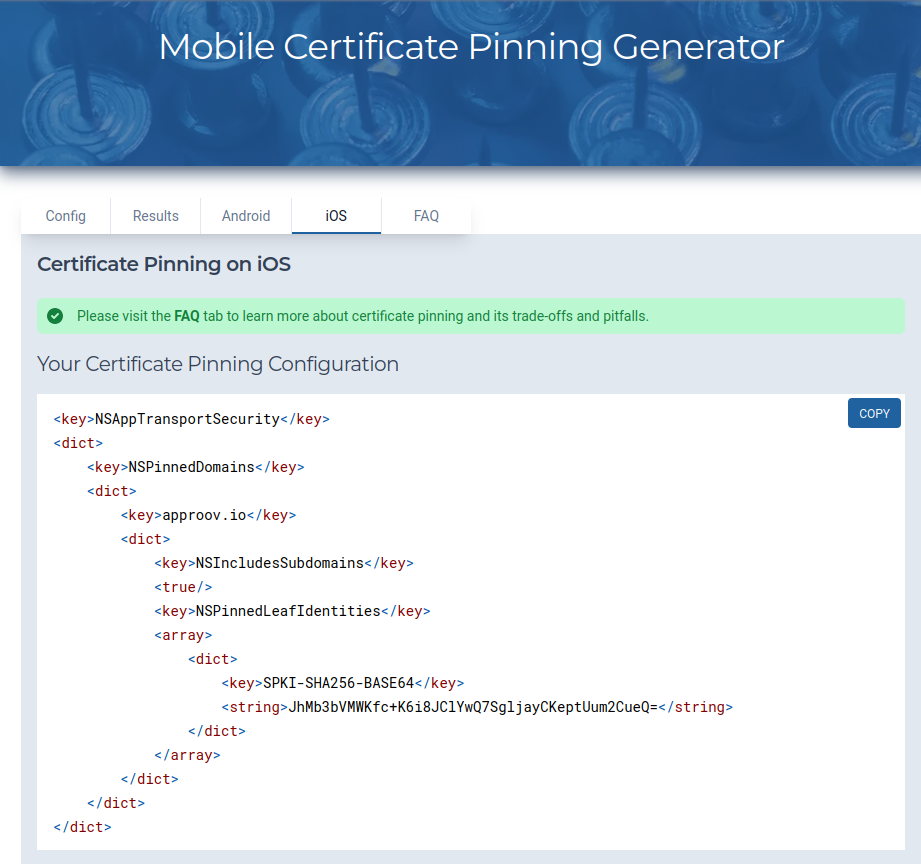
After you submit the form you need to go to the iOS tab to see your iOS configuration and copy/paste it into your mobile app code:
Do You Want To Go The Extra Mile?
In any response to a security question I always like to reference the excellent work from the OWASP foundation.
For APIS
The OWASP API Security Project seeks to provide value to software developers and security assessors by underscoring the potential risks in insecure APIs, and illustrating how these risks may be mitigated. In order to facilitate this goal, the OWASP API Security Project will create and maintain a Top 10 API Security Risks document, as well as a documentation portal for best practices when creating or assessing APIs.
For Mobile Apps
OWASP Mobile Security Project - Top 10 risks
The OWASP Mobile Security Project is a centralized resource intended to give developers and security teams the resources they need to build and maintain secure mobile applications. Through the project, our goal is to classify mobile security risks and provide developmental controls to reduce their impact or likelihood of exploitation.
OWASP - Mobile Security Testing Guide:
The Mobile Security Testing Guide (MSTG) is a comprehensive manual for mobile app security development, testing and reverse engineering.
