I could use some help with Azure AKS and ACR Integration. I create a ACR container and attach this container to the AKS cluster. I enable managed identity when creating AKS and I was hoping that ACR also uses managed identity
Here is the script I am using..
az group create --name $RESOURCEGROUP --location eastus
az acr create -n $REGISTRYNAME -g $RESOURCEGROUP --sku Basic
az aks create -n $CLUSTERNAME -g $RESOURCEGROUP --node-count $NODECOUNT --enable-addons monitoring --generate-ssh-keys --enable-managed-identity --attach-acr $REGISTRYNAME
az aks get-credentials -g $RESOURCEGROUP -n $CLUSTERNAME
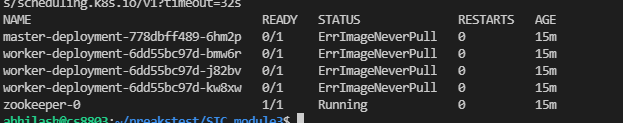
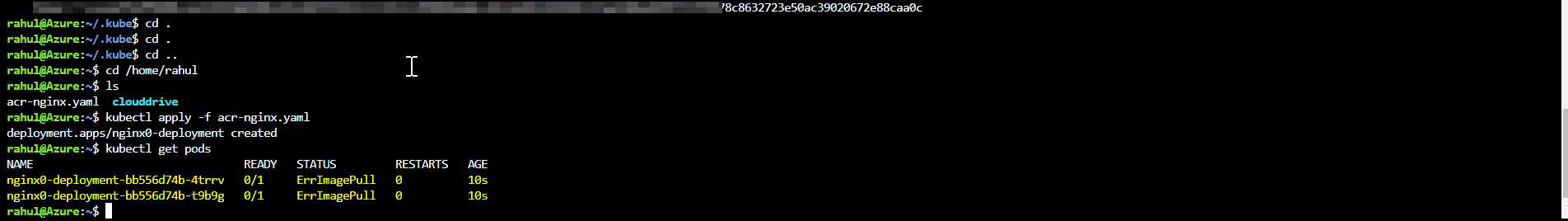
On AKS, when I get pods, I have a Image Pull error
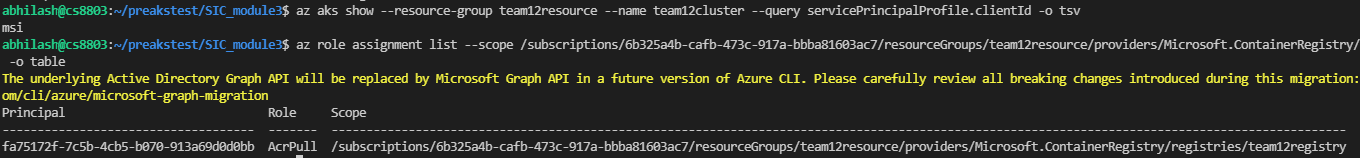
I see that AKS is using managed identity and ACR is using a Principal ID. How do I fix this issue
CodePudding user response:
Getting the simillar issue once i tried with same cmdlet which you given.
you need to try setting imagePullPolicy to Never and it just worked.
As kubectl describe pod mypd, Kubectl was trying to pull the image, and of course this image doesn't exis on remote server, hence the failure.
Above property will avoid connecting to registry and will use image from docker local images cache.
For Working with ACR & AKS
Import an image into your ACR Import an image from docker hub into your ACR by running the following:
az acr import -n <acr-name> --source docker.io/library/nginx:latest --image nginx:v1
Would suggest to you follow this Microsoft document Deploy the sample image from ACR to AKS
spec:
containers:
- name: nginx
image: <acr-name>.azurecr.io/nginx:v1
imagePullPolicy: Never
ports:
- containerPort: 80
Refernce : Why am I getting an ErrImagePull error in this Kubernetes deployment?
CodePudding user response:
The ErrImageNeverPull error suggests that your pod spec lists imagePullPolicy: Never, meaning that the kubelet will only look in the node's own cache and not try to pull from ACR. If you remove that, it should work.