I Have users created in AWS, but I am not able to locate if they have been only given programmatic access or console access or they have been provided with both.
is there a way to check , edit, or know what type of access is being used by a user.
CodePudding user response:
In the console, you can see it in the Security Credentials Tab of the User in IAM:
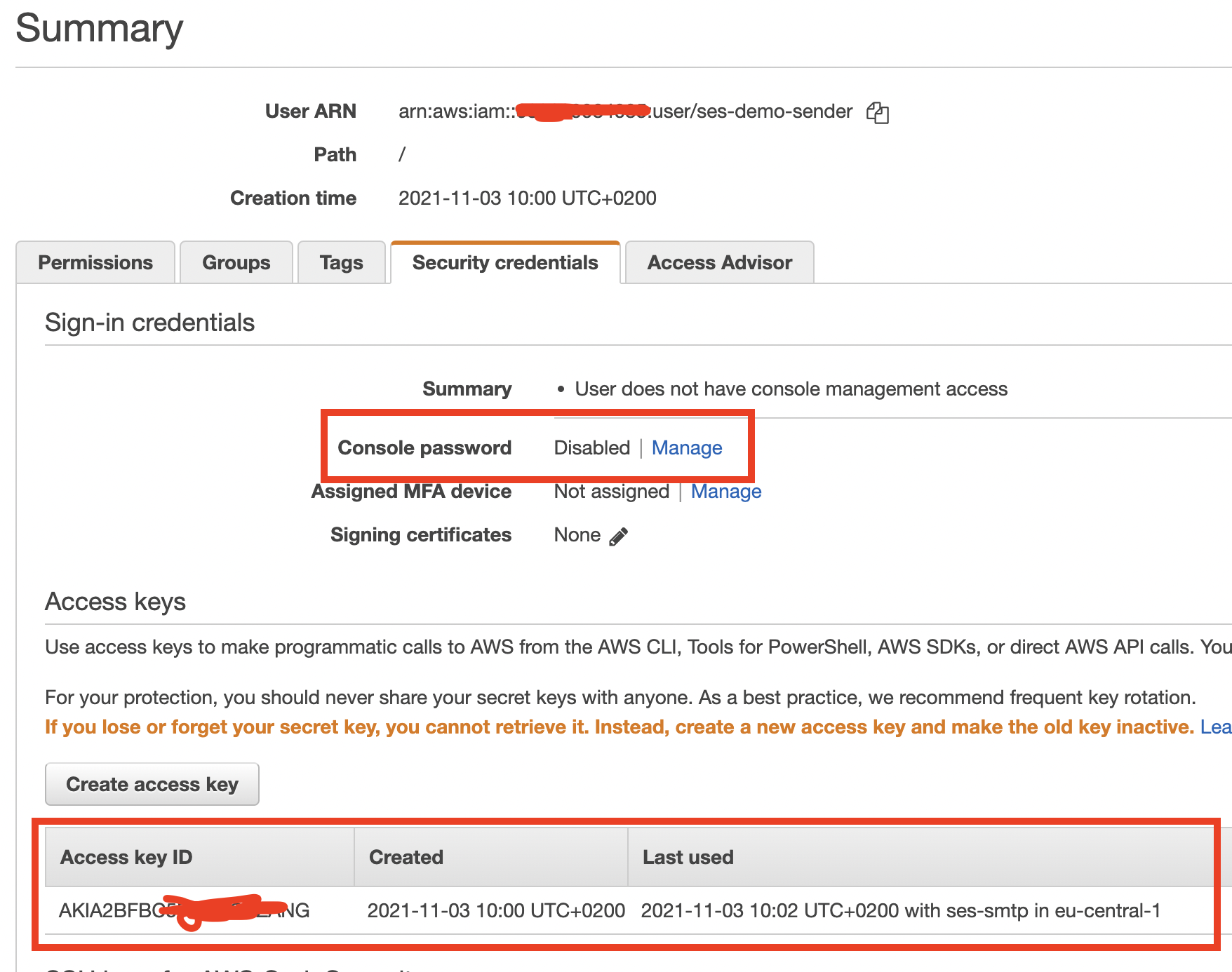
If the list of Access keys is not empty and at least one entry is active, it means they have programmatic access.
From the CLI you can also get this information. Erik showed you the command to list the access keys for a user to check if they have programmatic access.
$ aws iam list-access-keys --user-name raspi --no-cli-pager
{
"AccessKeyMetadata": [
{
"UserName": "raspi",
"AccessKeyId": "AKIA2BFBC12345KHW4",
"Status": "Active",
"CreateDate": "2021-07-07T07:42:37 00:00"
}
]
}
To figure out if a user can log in to the console, you need to check if they have a login profile:
$ # This user can login
$ aws iam get-login-profile --user-name raspi --no-cli-pager
{
"LoginProfile": {
"UserName": "raspi",
"CreateDate": "2021-07-07T07:42:37 00:00",
"PasswordResetRequired": false
}
}
$ # This user can't login to the console
$ aws iam get-login-profile --user-name ses-demo-sender --no-cli-pager
An error occurred (NoSuchEntity) when calling the GetLoginProfile operation: Login Profile for User ses-demo-sender cannot be found.
CodePudding user response:
You can check If a user has access keys. If a user has programatic access it needs access keys.
Here is a Cli command:
aws iam list-access-keys --user-name Bob
