I've created a custom azure policy, that checks if rg tag ID have one of the values I defined, but I want to be able to update allowedvalues list automatically on weekly basis for example. This is how my definition looks like:
{
"mode": "All",
"policyRule": {
"if": {
"allOf": [
{
"field": "type",
"equals": "Microsoft.Resources/subscriptions/resourceGroups"
},
{
"not": {
"field": "[concat('tags[', parameters('tagName'), ']')]",
"in": "[parameters('listofallowedtagValues')]"
}
}
]
},
"then": {
"effect": "[parameters('effect')]"
}
},
"parameters": {
"effect": {
"type": "String",
"metadata": {
"displayName": "Effect",
"description": "Enable or disable the execution of the audit policy"
},
"allowedValues": [
"Audit",
"Deny",
"Disabled"
],
"defaultValue": "Audit"
},
"tagName": {
"type": "String",
"metadata": {
"displayName": "Tag Name",
"description": "Name of the tag, such as id"
},
"defaultValue": "id"
},
"listofallowedtagValues": {
"type": "Array",
"metadata": {
"displayName": "Tag Values",
"description": "Value of the tag, such as 1"
},
"allowedValues": [
"1",
"2",
"3",
"4",
"5"
]
}
}
}
I want to set up either Automation Runbook or Azure Function to update "allowedValues" field for me, but I struggle to find out how should I do it. I can't find a good documentation about this, and MS one is really bad in that regard, no visual examples whatsoever. I tried to use either command, but I can't determine what should be put in params/parameter property:
az policy definition update --name $name --params ?
set-azpolicydefinition -name $name -parameter ?
MS documentation says that parameter property is:
The parameters declaration for policy definition. This can either be a path to a file name or uri containing the parameters declaration, or the parameters declaration as string.
which without declaration visualization says basically nothing. From errors I've seen there should be some kind of json definition put into params/parameters property, probably a part of the policy definition in json format with the new/updated allowedvalues list, but I tried many variations of that and it still fails. What should I put as a params and which additional properties I should define to update allowedvalues field? Should I keep trying to do it programatically using scripting or try to update it through API call? I'm not really familiar with APIs, hence why az ps module and cli were my first choice.
CodePudding user response:
What should I put as a params and which additional properties I should define to update allowedvalues field? Should I keep trying to do it programatically using scripting or try to update it through API call? I'm not really familiar with APIs, hence why az ps module and cli were my first choice.
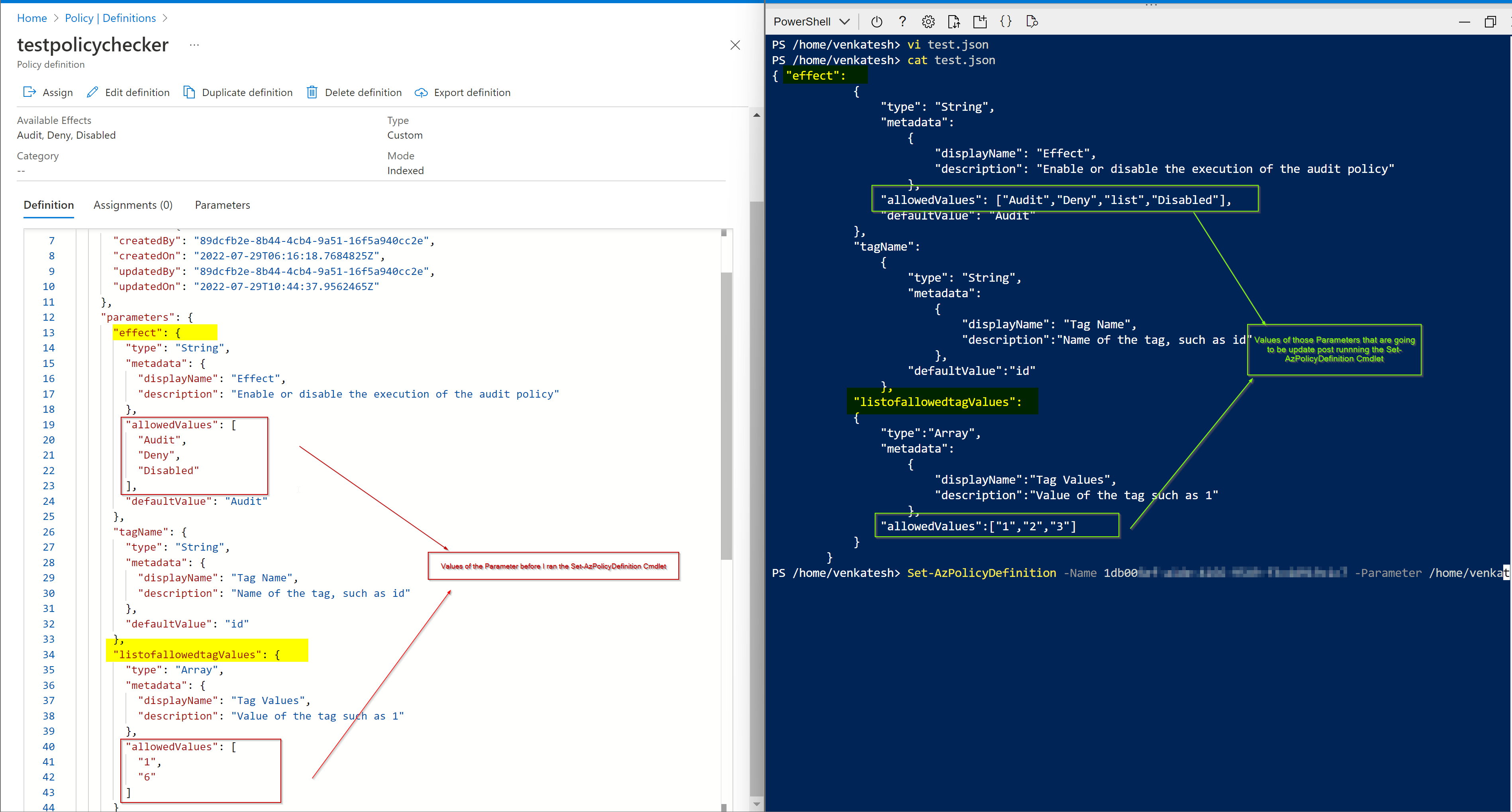
Using the above shared policy, I have created a policy definition in my subscription and using the below cmdlet's Set-AzPolicyDefinition or az policy definition update
- If you are using
Set-AzPolicyDefinitionthen you need create a separate JSON file to pass the parameter's and to update the policy definition.
Sample Parameters file :
{ "effect":
{
"type": "String",
"metadata":
{
"displayName": "Effect",
"description": "Enable or disable the execution of the audit policy"
},
"allowedValues": ["Audit","Deny","list"],
"defaultValue": "Audit"
},
"tagName":
{
"type": "String",
"metadata":
{
"displayName": "Tag Name",
"description":"Name of the tag, such as id"
},
"defaultValue":"id"
},
"listofallowedtagValues":
{
"type":"Array",
"metadata":
{
"displayName":"Tag Values",
"description":"Value of the tag such as 1"
},
"allowedValues":["1"]
}
Here is the cmdlet format that I have used.
Set-AzPolicyDefinition -Name <policyName> -Parameter /home/test.json
Here is the sample output for reference:
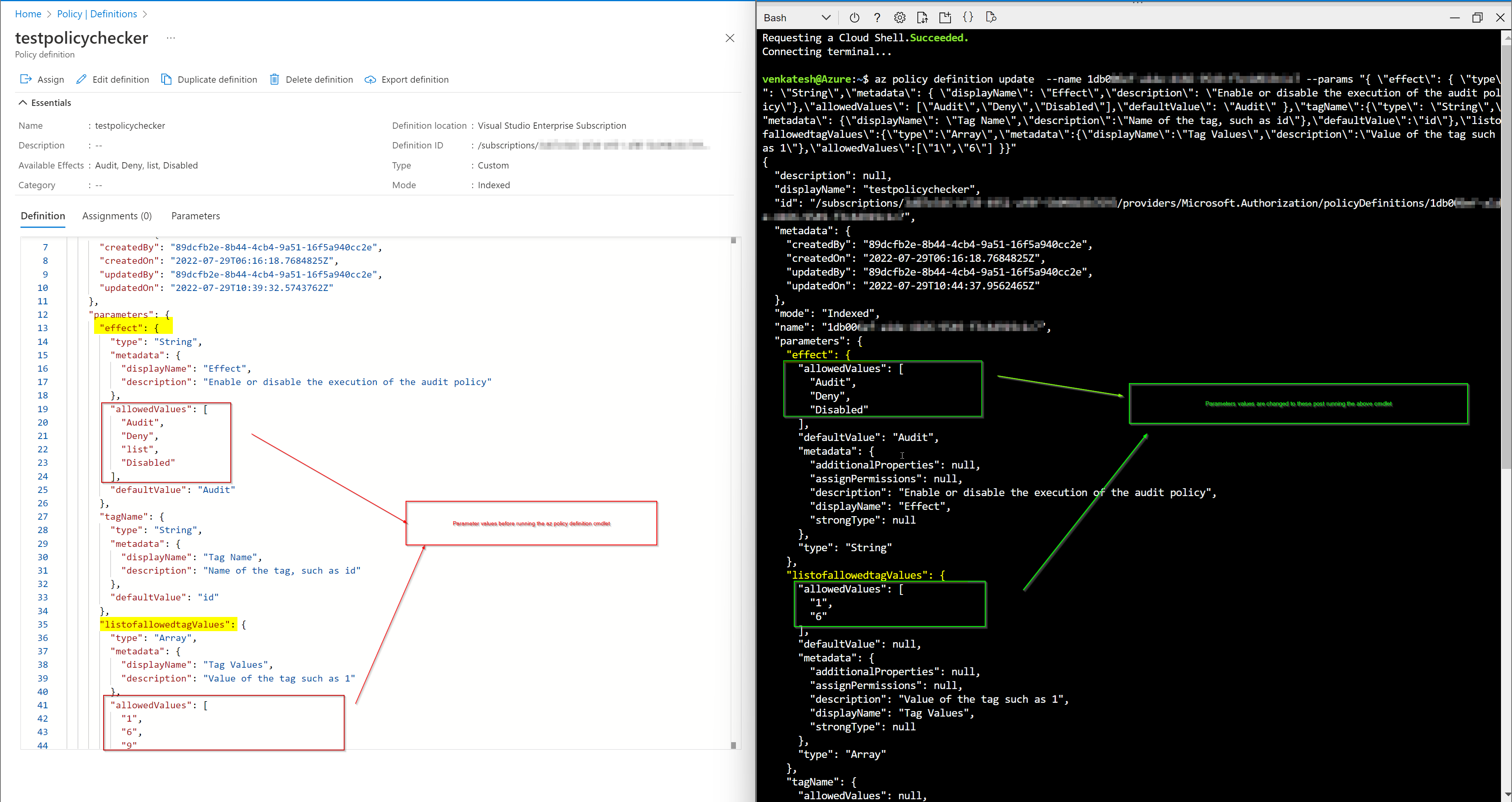
- If you are using
az policy definition updatecmdlet then you need to pass the parameter in the below format to update the policy definition.
az policy definition update --name <policyName> --params "{ \"effect\": { \"type\": \"String\",\"metadata\": { \"displayName\": \"Effect\",\"description\": \"Enable or disable the execution of the audit policy\"},\"allowedValues\": [\"Audit\",\"Deny\",\"list\",\"Disabled\"],\"defaultValue\": \"Audit\" },\"tagName\":{\"type\": \"String\",\"metadata\": {\"displayName\": \"Tag Name\",\"description\":\"Name of the tag, such as id\"},\"defaultValue\":\"id\"},\"listofallowedtagValues\":{\"type\":\"Array\",\"metadata\":{\"displayName\":\"Tag Values\",\"description\":\"Value of the tag such as 1\"},\"allowedValues\":[\"1\",\"6\",\"9\"] }}"
Here is the sample output for reference:
Note:
I have tested the above cmdlets from Azure cloud shell(Azure Portal) both are working fine from my end.