I have a droplet on DigitalOcean with IPv4 and IPv6 enabled. The droplet is behind a digital ocean network firewall with the following rules:
Inbound:
- SSH TCP 22 All IPv4, All IPv6
- HTTP TCP 80 All IPv4, All IPv6
- HTTP TCP 443 All IPv4, All IPv6
Outbound:
- ICMP ICMP All IPv4 All IPv6
- All TCP TCP All ports All IPv4 All IPv6
- All UDP UDP All ports All IPv4
My understanding and expectation is that will block all ssh attempts on ports other than port 22. However when checking the sshd unit in systemd journal. I see the following entries:
2022-12-29 03:00:32 Disconnected from invalid user antonio 43.153.179.44 port 45614 [preauth]
2022-12-29 03:00:32 Received disconnect from 43.153.179.44 port 45614:11: Bye Bye [preauth]
2022-12-29 03:00:31 Invalid user antonio from 43.153.179.44 port 45614
2022-12-29 02:58:37 Disconnected from invalid user desliga 190.129.122.3 port 1199 [preauth]
2022-12-29 02:58:37 Received disconnect from 190.129.122.3 port 1199:11: Bye Bye [preauth]
2022-12-29 02:58:37 Invalid user desliga from 190.129.122.3 port 1199
and many more of these lines, which means the firewall is not blocking ssh connections on ports other than 22.
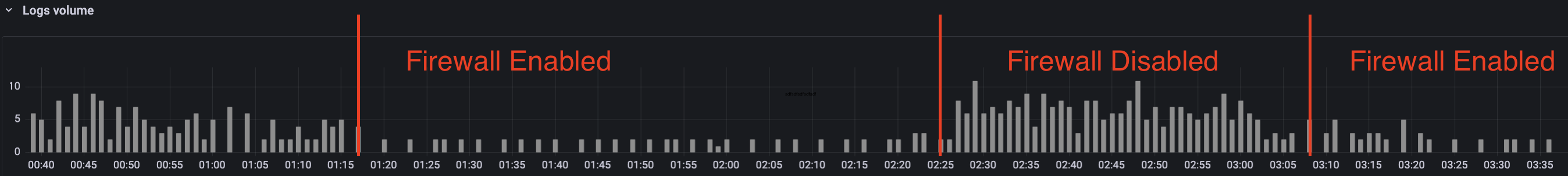
The following graph shows the number of ssh connections to ports other than 22 in the last hour. The connections are reduced with enabling the Network Filter, but they not diminished.
Could it be that the Network Firewall of DigitalOcean is broken?
What am I missing?
Anyone is seeing the same situation on their infrastructure?
CodePudding user response:
The ports being shown in the log are the remote ports that the connections are coming from on the remote IPs, and not indicating that those ports are listening on your server or through the firewall. The firewall is configured from your description to allow for any remote IP and port to connect to your droplet on local ports 22, 80, and 443.