Me and my team are using Azure Synapse Analytics to ingest data from a REST API to a Azure Data Lake Storage Gen2, in order to create views automatically.
The only way we could manage to do this in our Workspace was by previously changing the Public Access Level to the Container inside our Storage Account to "Container (anonymous read access for containers and blobs)".
Is there any way to avoid doing this, and just enable this level of access to specific containers for a limited amount of users / IPs, while keeping it "Private (no anonymous access)"?
Click to Azure Portal view of the Containers inside a certain Storage Account resource
CodePudding user response:
Yes, you can use Shared Access Signatures for it. You can find more information in here:
https://learn.microsoft.com/en-us/azure/storage/common/storage-sas-overview
CodePudding user response:
I do agree with @Thiago Custodio and @Nandan, we can use SAS Token and URL for limited access to Container in the storage accounts.
To get SAS token:
- Firstly, open the storage account, then click on container.
- Then click on your container and then click on Shared Access tokens as below.
- Then you can select what access you want to give access as below. Then Generate the token.
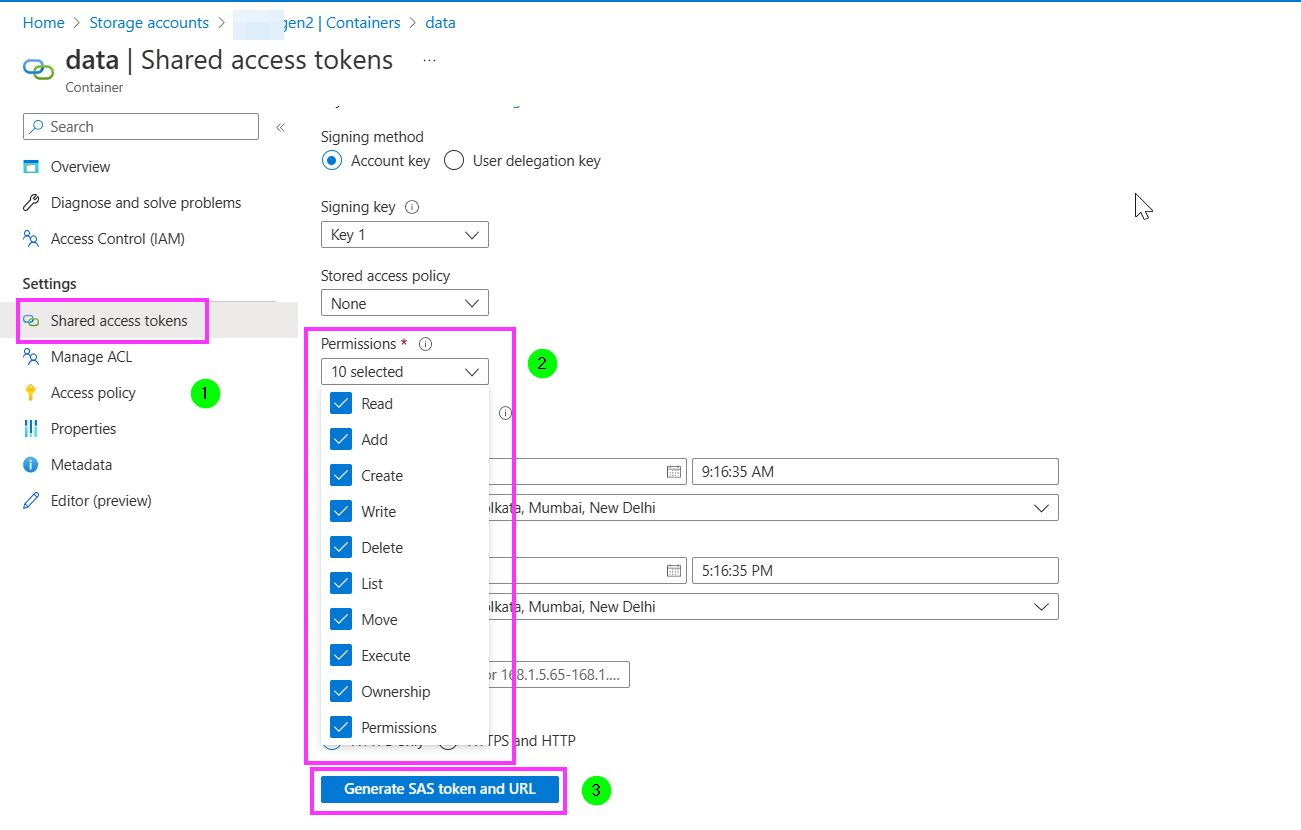
The token comes as below, now you can send this token to whom you want to give access your container.

Alternatively, you can also create a private endpoint as below:
- Firstly, click on Networking, the click on Private endpoint connections and then ( ) create a end point.
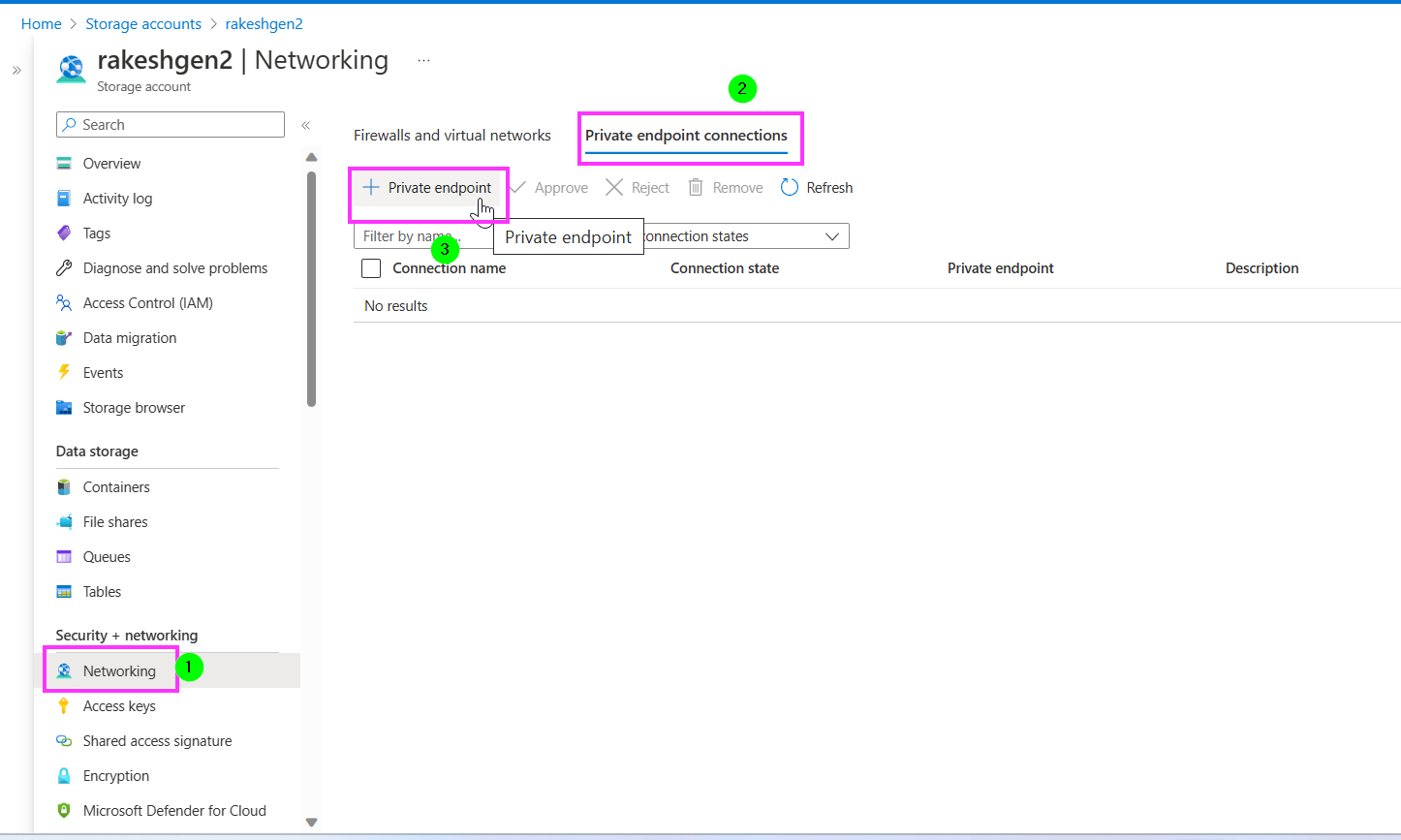
Now this Container can be accessed from the Virtual Machine integrated with this private endpoint.
