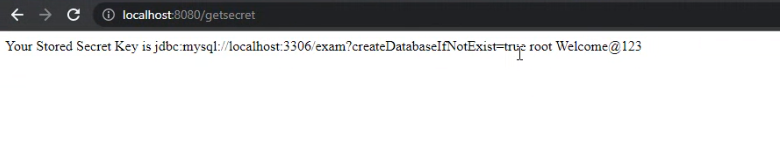
Am using azure keyvault to store my db username , url & password. I am using
<dependency>
<groupId>com.azure.spring</groupId>
<artifactId>spring-cloud-azure-starter-keyvault-secrets</artifactId>
</dependency>
this dependency to read the values configured in keyvaults in my spring boot application. But am getting Failed to determine suitable jdbc url error when the application loads. Can anyone help me one this
CodePudding user response:
spring-cloud-azure-starter-keyvault-secrets fetches values from the keyvault and makes them available as properties, but you have to use the properties somewhere.
You seem to be missing the basic datasource configuration. Assuming the keyvault contains entries for spring-datasource-url, db-username and db-password, in application.yml (or equivalent) you need somethings like:
spring:
datasource:
url: ${spring-datasource-url}
username: ${db-username}
password: ${db-password}
driver-class-name: com.microsoft.sqlserver.jdbc.SQLServerDriver
jpa:
database-platform: org.hibernate.dialect.SQLServer2012Dialect
CodePudding user response:
nested exception is java.lang.RuntimeException: Driver com.microsoft.sqlserver.jdbc.SQLServerDriver claims to not accept jdbcUrl, ${spring-datasource-url}
There could be a possibility that you might have given wrong MS SQL URL, that might be causing to throw the above exception. you can refer to the GITHUB documentation which I have followed.
I have tried the same from my end and got expected results:
Step 1:
Open the Azure Cloud Shell and run below command to get list of subscriptions
az account list
Step 2:
Setting the perticular Subscription
az account set -s your\_subscription\_id
Step 3 :
Creating service principal
az ad sp create-for-rbac --name myapp --role Contributor --scopes /subscriptions/mySubscriptionID
- Go to Active Directory and select service principal app and store below details:
Your Client_ID
Your Client\_Secret\_Value
Your Tenant_ID
Step 4 :
Follow Below Steps:
- Create Resource Group in Azure Portal
- Create KeyVault in Azure Portal by selecting resource group
- After Creating Key Vault create secret and store your secret key
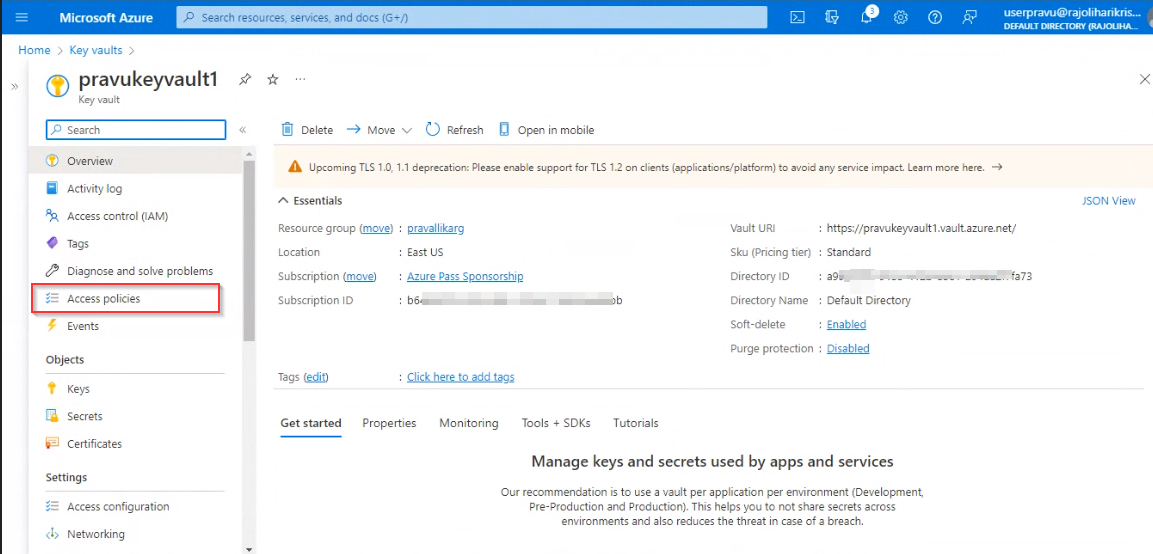
- Now select your key vault and in left hand side select option called “Access policies”.
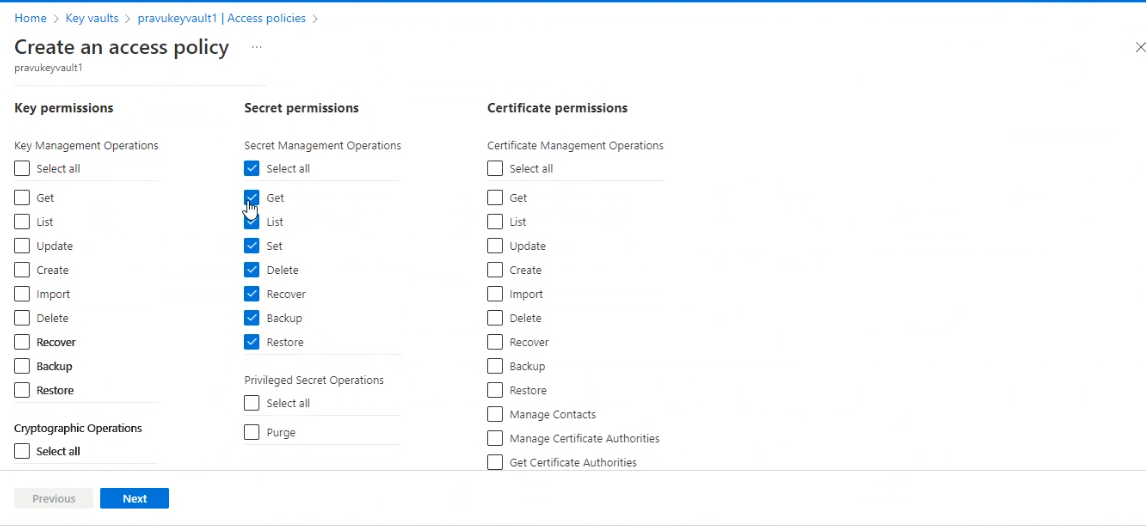
- Click on Create and select the permissions which you want such as “Get, List, Recover, Set, Delete, Backup, Restore” in secret permissions.
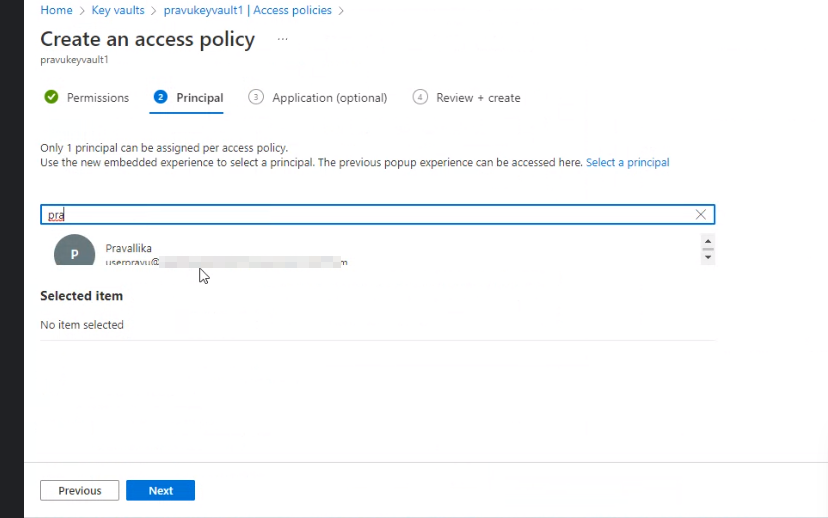
- Click “Next” and select your service principal app you created in “Step3” and click “Create”.
Step 5:
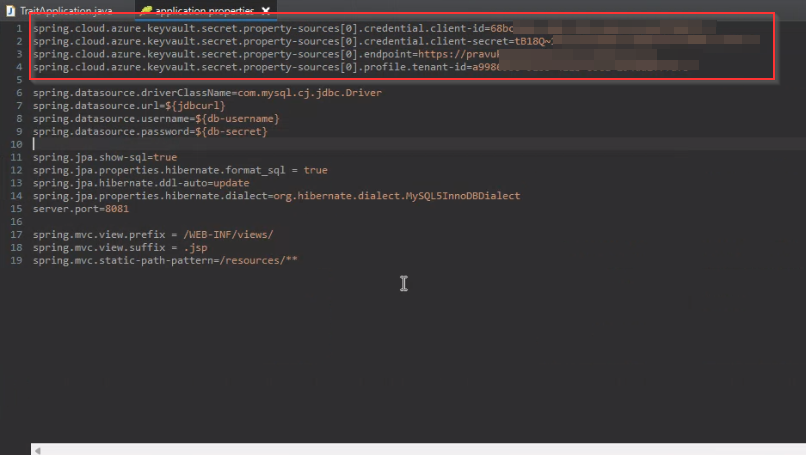
Now Copy Your Client_ID, Your Client_Secret_Value, Your Tenant_ID and Key Vault URL in Spring Boot application Under resources folder in application.properties file like below:
spring.cloud.azure.keyvault.secret.property-sources[0].credential.client-id=Client_ID
spring.cloud.azure.keyvault.secret.property-sources[0].credential.client-secret=Client_Secret
spring.cloud.azure.keyvault.secret.property-sources[0].endpoint=KeyVault_URL
spring.cloud.azure.keyvault.secret.property-sources[0].profile.tenant-id=Tenant_ID
Output: