I've created an organization with a new management account call it MA and invited my personal account, call it A.
What I wanted is to share a dynamodb table created by MA with the members of an organization (for instance with A that is under root).
For that, I've created a policy that grants full access to that table, attached to a brand new role joined to A ( that is a full member to the org ), but unfortunately, from A account, I can't see the table.
Where did I make a mistake?
Policy JSON - dynamodb-products-table-full-access:
{
"Version": "2012-10-17",
"Statement": [
{
"Sid": "VisualEditor0",
"Effect": "Allow",
"Action": [
"dynamodb:ListContributorInsights",
"dynamodb:DescribeReservedCapacityOfferings",
"dynamodb:ListGlobalTables",
"dynamodb:ListTables",
"dynamodb:DescribeReservedCapacity",
"dynamodb:ListBackups",
"dynamodb:PurchaseReservedCapacityOfferings",
"dynamodb:DescribeLimits",
"dynamodb:ListExports",
"dynamodb:ListStreams"
],
"Resource": "*"
},
{
"Sid": "VisualEditor1",
"Effect": "Allow",
"Action": "dynamodb:*",
"Resource": "arn:aws:dynamodb:eu-central-1:<MA ID>:table/products"
}
]
}
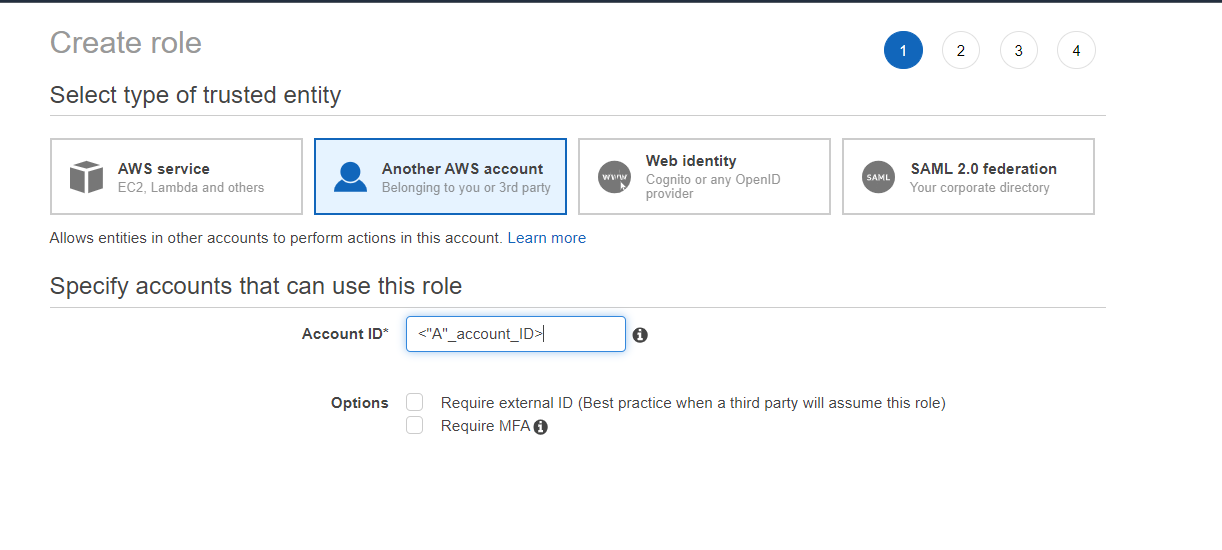
Another AWS account type role that attached to the A account.
CodePudding user response:
Follow the next steps:
- Create a role in the "MA" account (DynameDB table owner) allowed to access the DynamoDB table.
- Allow users in the "A" account to assume the role created in the "MA" account.
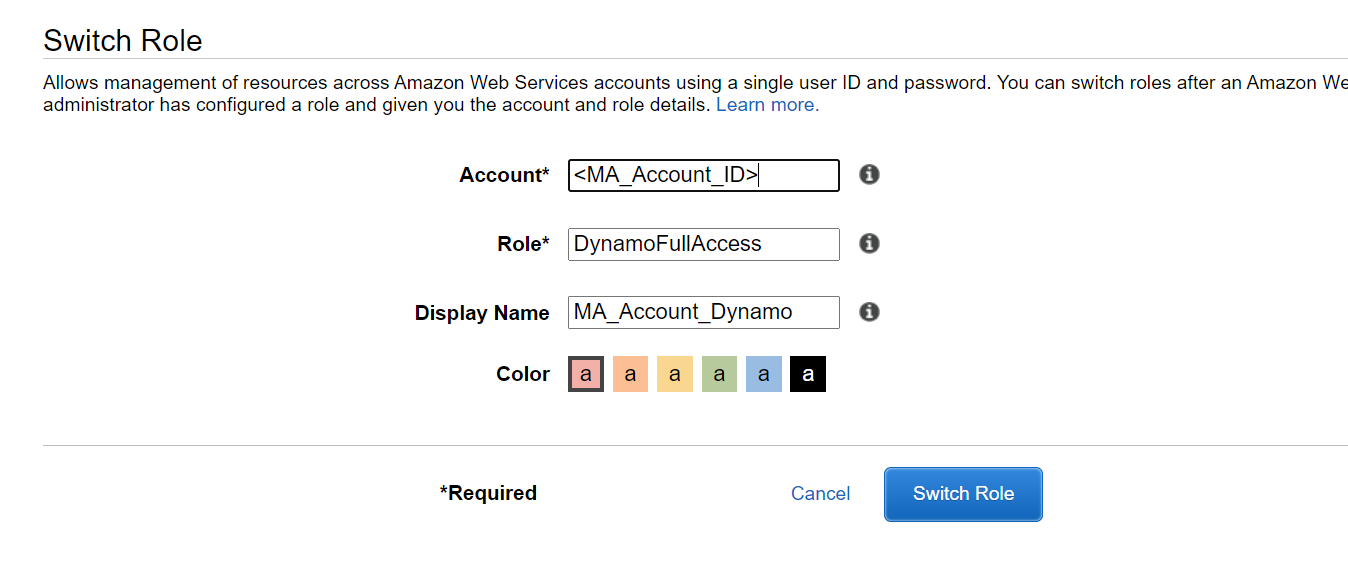
- Use the 'Switch Role' AWS Console feature
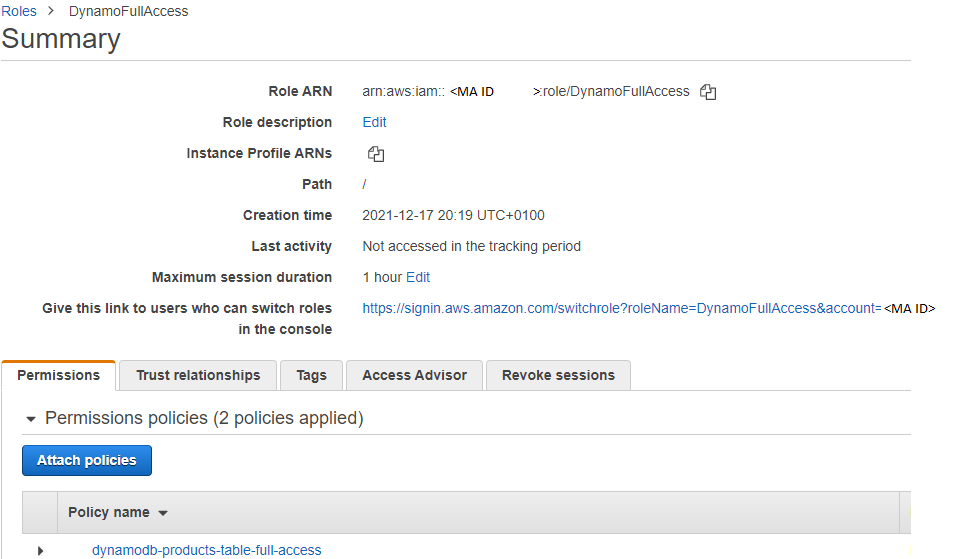
Role in the "MA" account
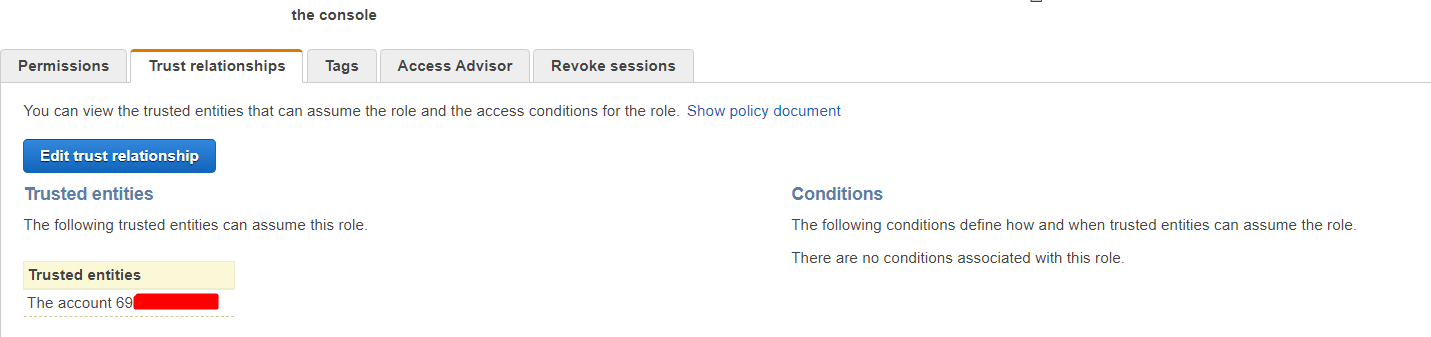
It needs the permissions to access DynamoDB table. Statements showed on "dynamodb-products-table-full-access" policy are enough. Additionally, when creating the role, you need to define the "A" account as a trusted entity.
Users in the "A" account allowed to assume the role
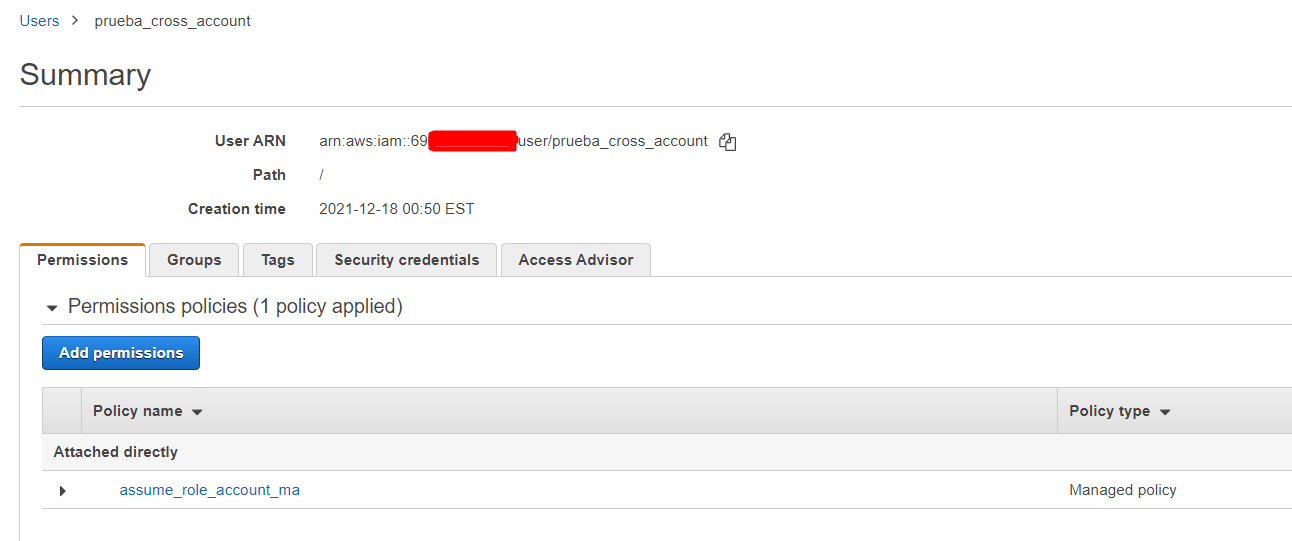
On account "A" create a policy with the proper permissions to assume the role created on the previous step:
{
"Version": "2012-10-17",
"Statement": {
"Effect": "Allow",
"Action": "sts:AssumeRole",
"Resource": "arn:aws:iam::<MA_Account_ID>:role/DynamoFullAccess"
}
}
Add that policy to the Permissions policies of the corresponding IAM User or IAM User Group:
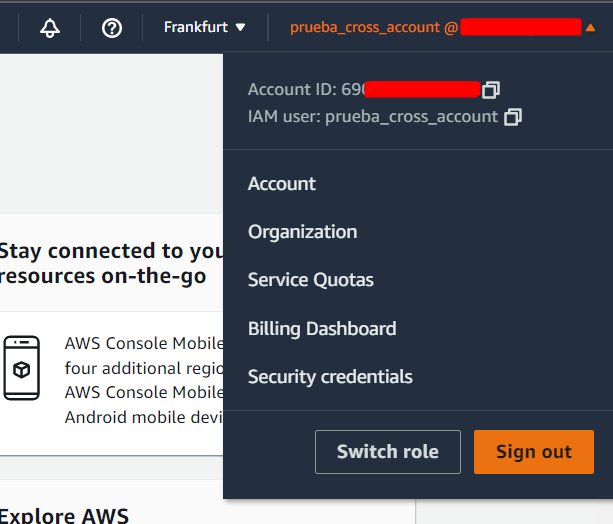
Using the 'Swith Role' feature
Finally, when the account "A" user enter to the AWS Console, needs to use the "Switch role" feature:
Enter the MA Account ID and the name of the role created on that account:
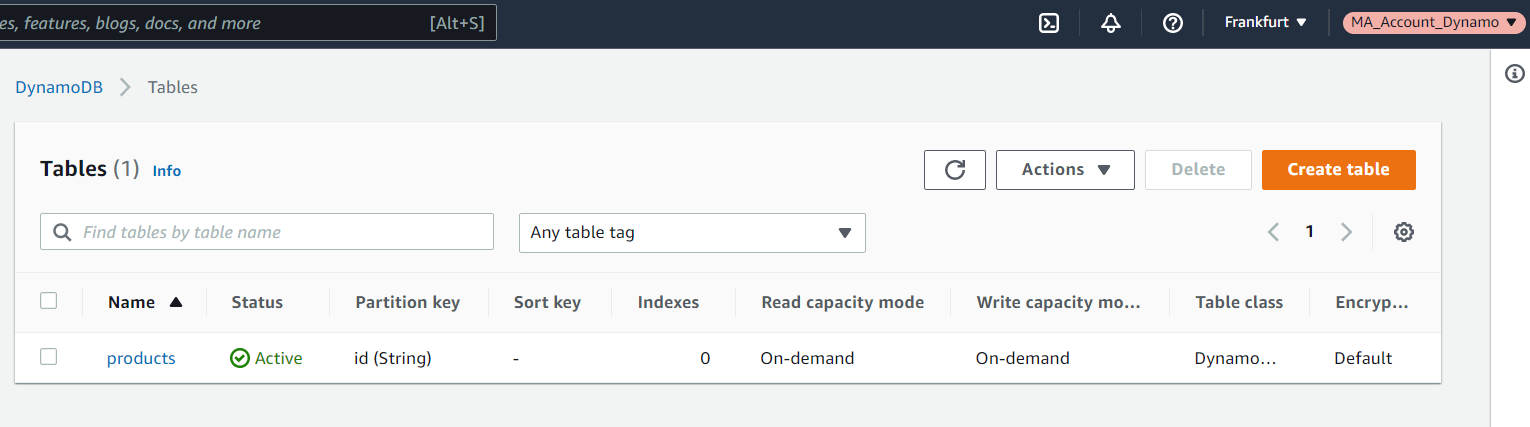
And he will be able to use the table (note on the role assumed 'MA_Account_Dynamo'):
Reference: