I am looking to access the secret keys that I set up in Databricks in Azure Synapse.
I had gone through a process to attach the keys to the Databricks cluster so that I could access them with the following Python code:
spark.conf.get("spark.example_client_id")
How can I set this up and replicate this in Azure Synapse?
It looks like the solution is to do something like mssparkutils.credentials.getSecret("example_client_id") in Synapse, but how exactly do you set it up so that you've hidden the keys to the desired variable names? And is getSecret() the right way to access the newly stored keys?
Do we attach these new keys to the Synapse pool like we did in the cluster? Let's say my pool is called my_new_pool.
CodePudding user response:
Yes, you can hide and retrieve secret keys using the Key Vault and Azure Synapse.
Please follow these steps:
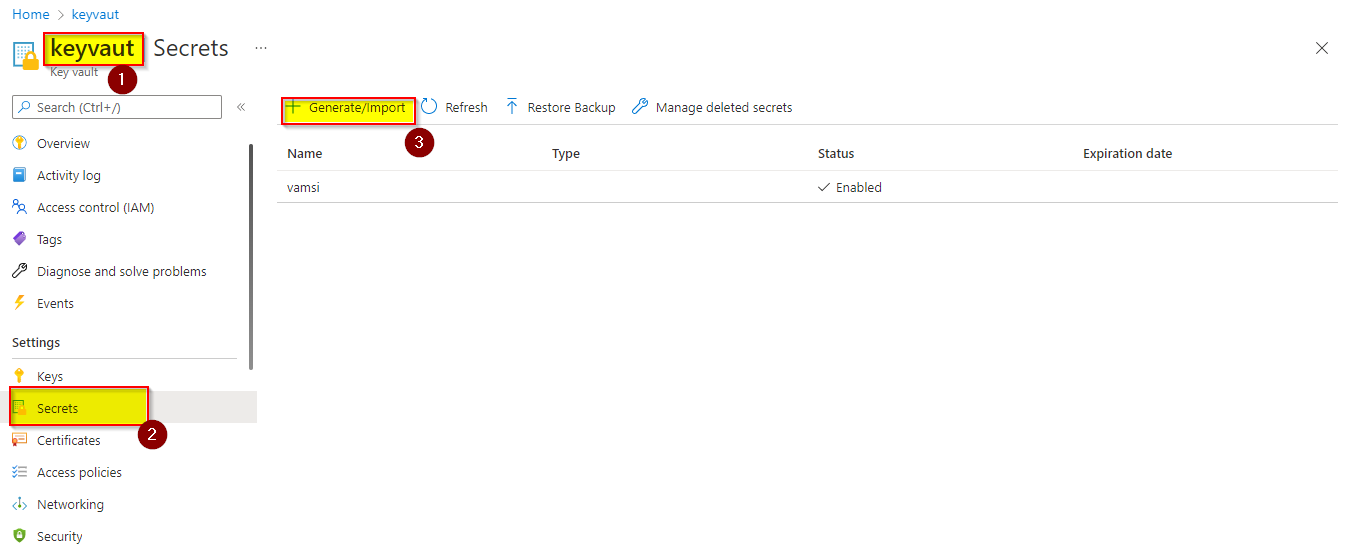
- Go to Azure Key Vault, create a secret and store a secret value
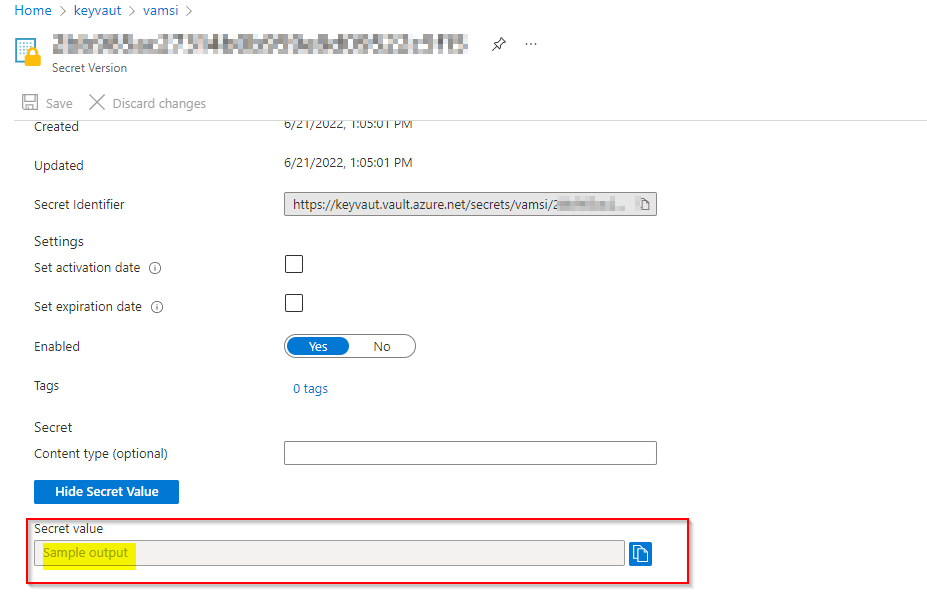
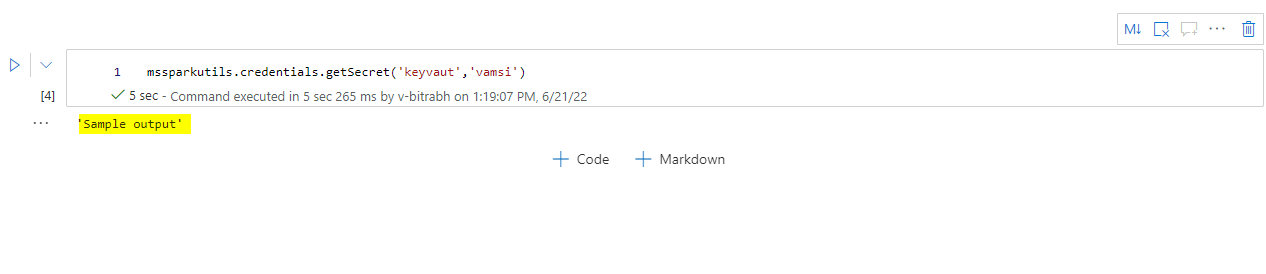
- In my case, I store secrete value as
sample outputas shown in the below image.
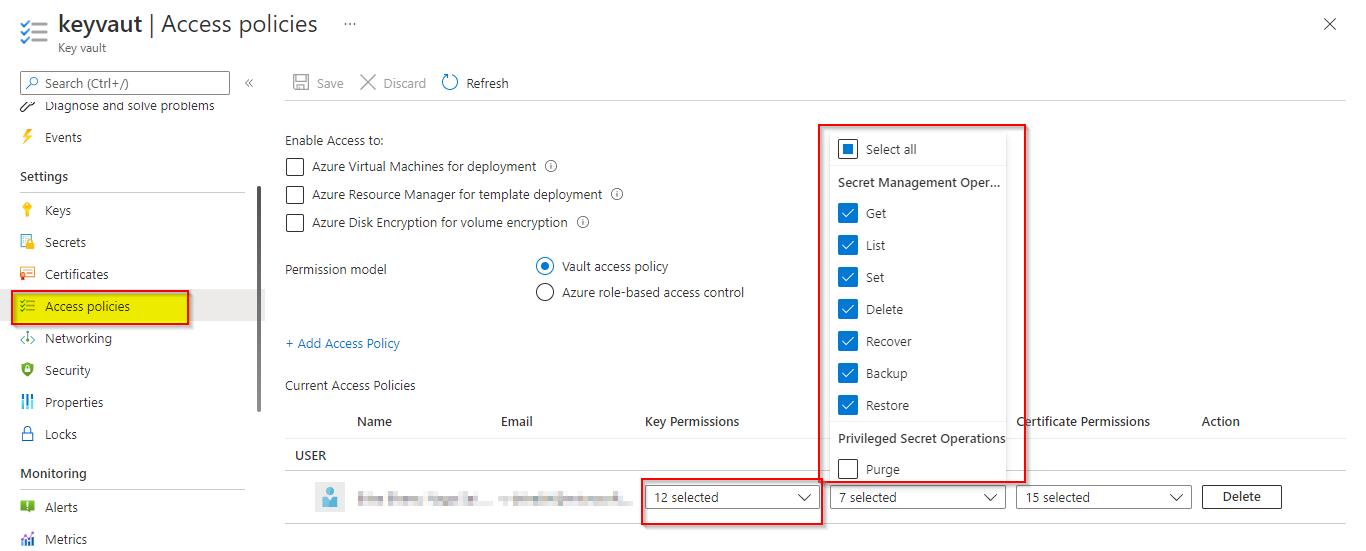
- Make sure to check whether access policies permission given or not.
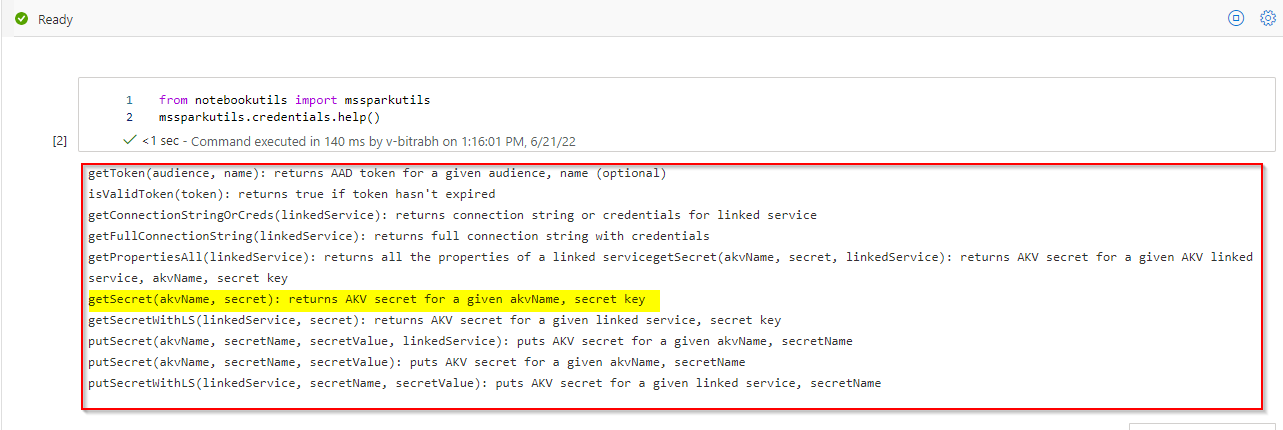
Go to azure Synapse studio and follow this sample code.
from notebookutils import mssparkutils mssparkutils.credentials.getSecret('azure key_vault_name' , 'secret_name')
Here, you can see my secrete value.
Reference: