[] enlightenment stage began in protection against reverse code obfuscation techniques
, the biggest characteristic is period, never still of code obfuscation techniques, has become the only effective protection against reverse technology, this should speak of the JAVA language was born in 1995, it let people enjoy a cross-platform work convenience, at the same time, due to its easy decompiled nature, also make the traditional machine code for security protection overnight become useless,
From then on, the once pariah code obfuscation techniques gradually attention by people, starting from Android 2.3, Google has joined a call in the SDK ProGuard code obfuscation tools, through which can confuse the JAVA code,
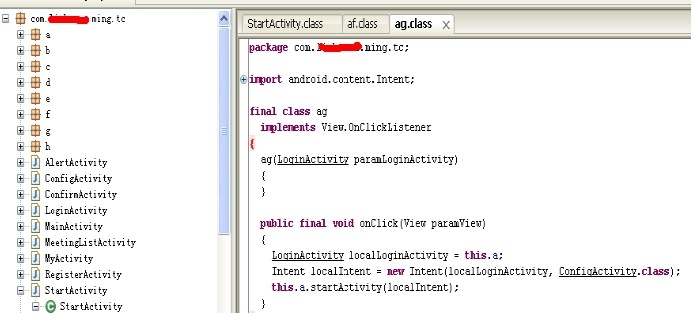
ProGuard obfuscated DEX file screenshot
From the picture above you can see, the code after the confusion to the left of the name of the class are turned into a, b and other custom letters, although machine execution logic is the same, but increase the difficulty of the hacker artificial analysis and time cost, and to some extent, the code obfuscation techniques well protect the JAVA source code, but this way is simple to change the name of the class or variable names, hackers, as long as find DEX file decompilation is a matter of time before, we have to see whether time costs more than hacker gains,
[development] DEX encryption technology become a mainstay application protection
As Android decompilation technology is more and more strong, even if the code obfuscation techniques do native layer, is take temporary solution not effect a permanent cure, in order to solve the code obfuscation techniques has shortcomings, more and more people use DEX whole hidden and DEX extract code encryption to protect their safety function, such as love encryption manufacturers such as early reinforcement products with this technology,
(1) overall DEX file encryption
To overall DEX file encryption, combined with shell APK to new DEX file, and then replace the shell program in DEX file can get new APK, new APK runtime will be encrypted DEX file in memory, dynamic loading and lets the Dalvik virtual machine implementation,

Overall DEX file encryption against static analysis, but also there are some defects, the technology for whole DEX file encryption, decryption operation, the runtime memory exists in the complete code in a row, by modifying the Dalvik virtual machine could obtain the decrypted code by means of memory Dump, while developers can take some patch method to increase the difficulty of crack, the end of the class loader, for example, erase or confusing memory
DEX file of the head or the tail information, but these methods cannot fundamentally solve the problem of memory Dump,
(2) the DEX function extraction encryption
To solve the DEX file encryption can be whole memory Dump this weakness, DEX function extraction encryption technology to separate encryption code each method in extracting the JAVA virtual machine before performing a method for the first time, began to load the code in this method, using the method of this mechanism will decrypt operation to a delay before execution to decrypt this method, and decrypted code in memory is discontinuous store, for example, by extracting the Dalvik virtual machine run a DEX essential parts of the DEXCode less, then the bytecode instructions to add the nop, greatly increase the code security, this way
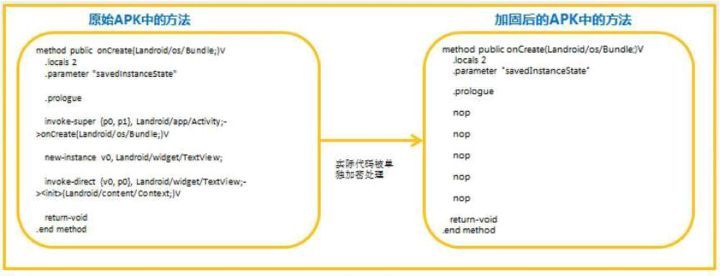
encryption code of DEX file comparison before and after the
The strengthening technology of the main advantages: (1) the smaller encryption granularity, from DEX file encryption granularity level into the method level; , (2) on-demand decryption decryption operation delay until a method before do execution triggered, if the method is not implemented, do not be decrypted; (3) memory of discontinuity, avoids the problem of memory Dump, greatly improve security,
[peak stage] VMP reinforcement to become "the ultimate big recruit" protection against reverse
EX extract encryption function to solve the problem is memory Dump, but in essence it is a hidden code technology, final code or by Dalvik virtual machine or ART performing, therefore, crackers can build a modified virtual machine to shell, it's need to seek more powerful and safe prevent reverse technology to ensure the safety of the APK, virtual machine software protection technology (VMP) to become the current cutting-edge mobile application security reinforcement technology,
VMP will first program to be protected target, "compile" the core code, will be used by the compiler to generate native code (Nativecode) into effect equivalent byte code, and then control the virtual machine, controlled by the virtual machine to perform, VMP is the most key technology need to customize a set of virtual machine instructions and the corresponding to the interpreter, then convert standard instruction into their instruction, by a custom interpreter explanation executes instructions,
So even the bytecode of crackers to custom is meaningless, unless you can reverse crack custom virtual machine to explain the engine, in addition, VMP can also build a number of different virtualization explain engine, different JAVA methods using different virtualization execution engine, this will further enhance the security of the application,
Although there are quite a number of manufacturers are in the market now released the VMP protection scheme for mobile applications, but there are many vendors use are code confusion or hiding technology, the author thinks that a set of high quality custom instruction set and the interpreter is the only standard to determine VMP technology facts, and understand, currently in the domestic security vendor only love encryption on the VMP technology development is relatively mature,
written in finally:
Any safety technical change is a history, mobile application security development also is such, to some extent, the Android anti reverse technology evolution is equal to the mobile application security basic evolutionary history, such as domestic love encryption, the reinforcement technique is also from the early evolution of code obfuscation techniques to the current the most advanced virtual machine protection technology, security attack and prevention is an eternal topic, also is a dynamic spiral development process, developers need to constantly improve their safety awareness and skills, to better cope with various security issues that emerge in endlessly,
