I'm trying to create a multi-tenant application in AAD, where any organization can log in. I can get an authorization token using my credential of course it is our organization so it will work. what I'm trying to achieve is to acquire token using the username and password e.g:
u: [email protected] p: test1
u: [email protected] p: test2
u: [email protected] p: test3 etc...
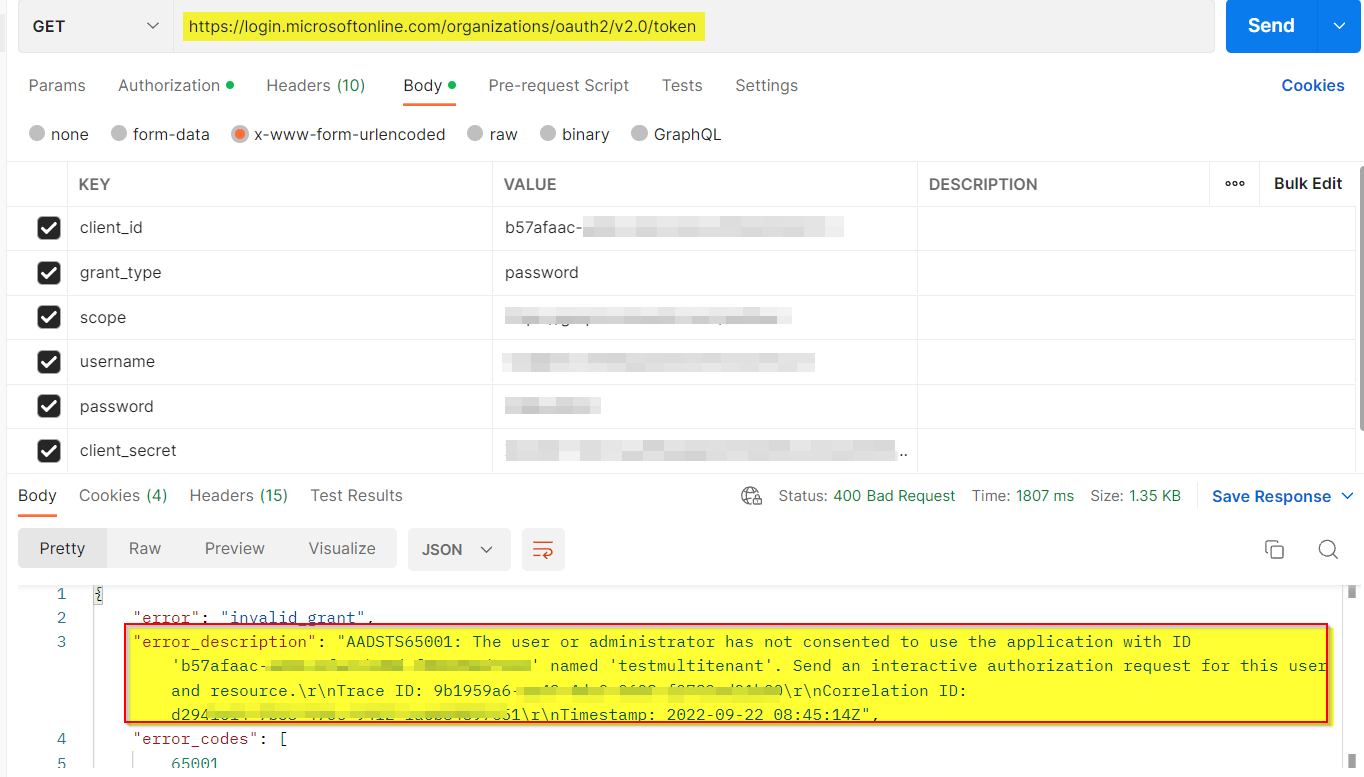
I get the following error: AADSTS65001: The user or administrator has not consented to use the application with ID [APP ID] Send an interactive authorization request for this user and resource.
I have already executed the grant admin consent from API permissions but still, I've got an error. what settings did I miss?
This is the way I initialize the IPublicClientAppliction:
var app = PublicClientApplicationBuilder
.Create(clientId)
.WithAuthority(AadAuthorityAudience.AzureAdMultipleOrgs)
.WithDefaultRedirectUri()
.Build();
var scopes = new string[]
{
"offline_access",
"email",
"https://outlook.office.com/IMAP.AccessAsUser.All"
};
var authToken = app.AcquireTokenByUsernamePassword(scopes,email,
password).ExecuteAsync();
Kind regards.
CodePudding user response:
I tried to reproduce the same in my environment and got the results like below:
I created an Azure AD Multi-Tenant Application like below:
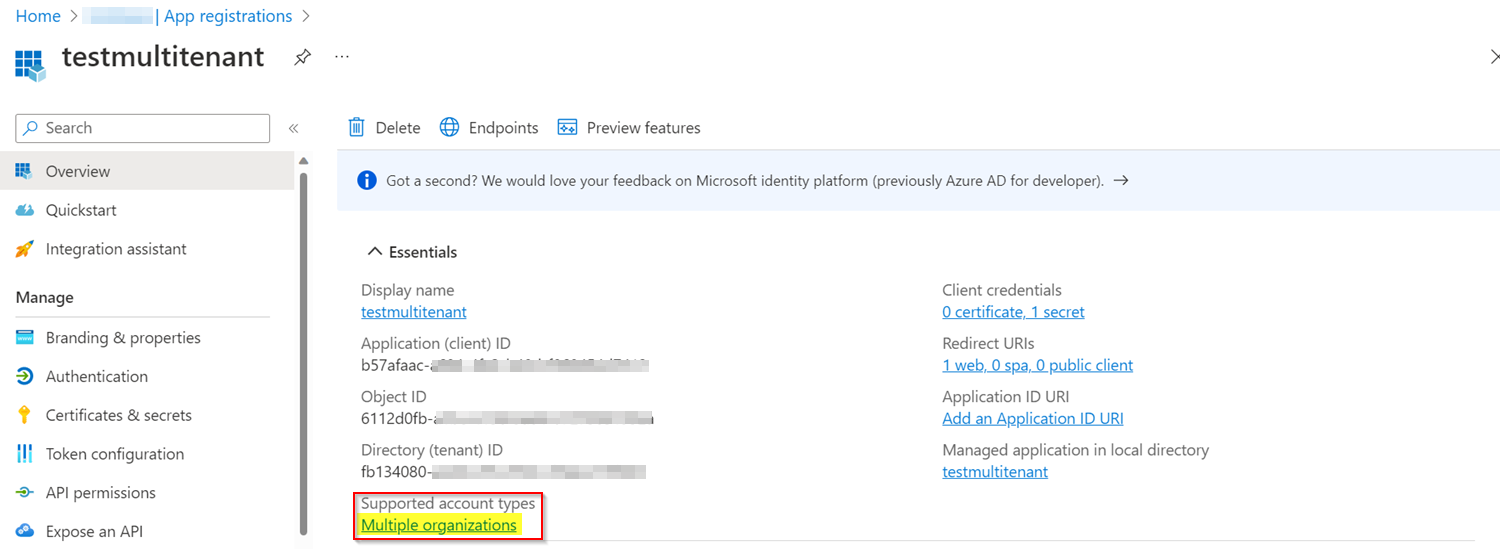
I tried to generate the access token via ROPC flow in Postman by using the credentials of the same tenant user by using parameters like below:
POST https://login.microsoftonline.com/organizations/oauth2/token
client_id : xxxxxx-xxx-xxx-xxxx-xxxxxxxx
grant_type : password
scope : scope
username : user@********.onmicrosoft.com
password : ******
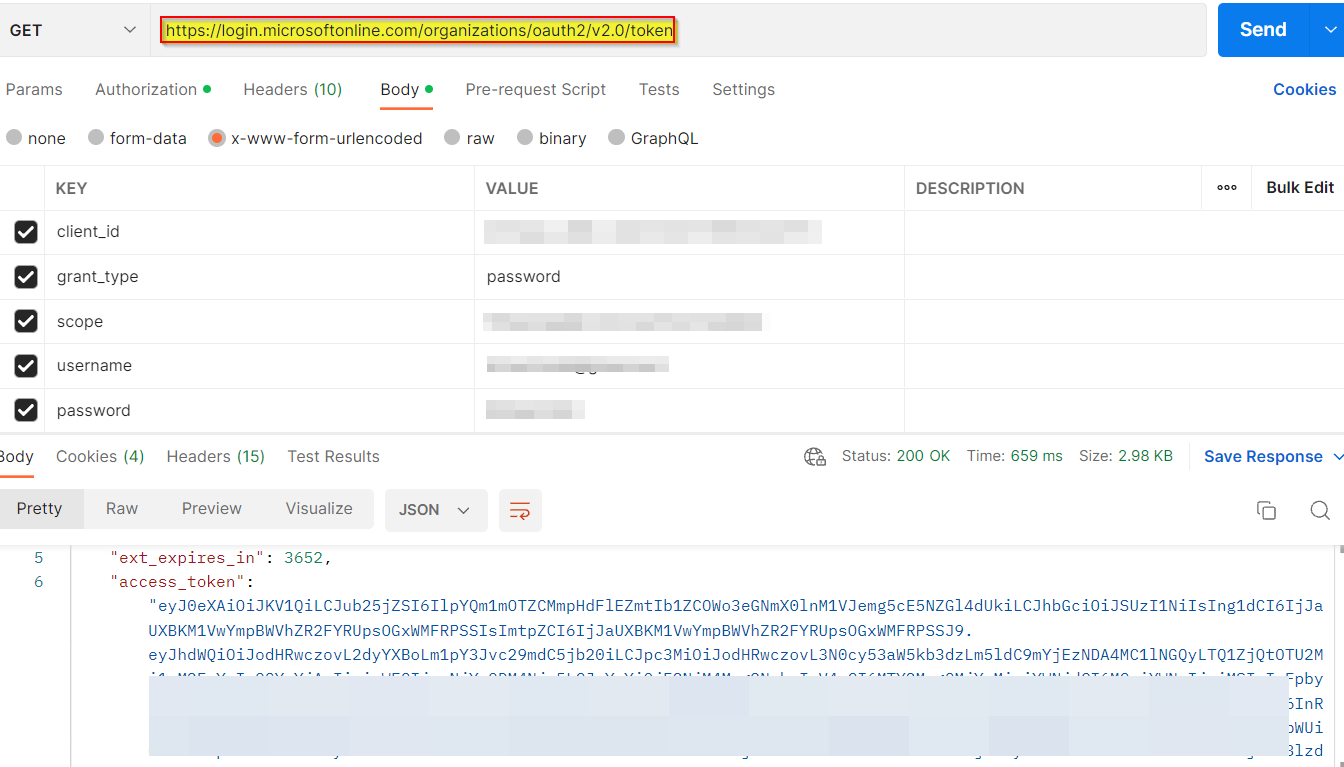
Please note that, ROPC flow supports only Local accounts (Azure AD user accounts originally created in AAD tenant where application is created). It doesn't support other tenant users/guest users.
When I tried to generate the token by using credentials of other tenant user, I got the same error as below:
Reference:
Sign in with resource owner password credentials grant - Microsoft Entra
