i have a Question about an Azure SQL Server and the Azure Firewall.
I have configured the Azure SQL Server with Private Endpoints. The Network Hub and Spoke are with peerings connected. The Private DNS Zone is linked to both Virtual Networks. The Public Access is disabled on the Azure SQL Server.
No i would like to Use Azure Firewall Rules to Connect from External (WWW) trough the Azure Firewall the Azure SQL Server with Management Studio.
I can find nothing to this Scenario.
I have to tried it with "DNAT / Application NAT / Network Nut" but nothing works.
is it even possible to reach the SQL Database over the Public through the Firewall when the public Access is disabled on the SQL Database?
Thanks a lot.
Regards, Phil
CodePudding user response:
I tried to reproduce to reproduce the same and tried "DNAT / Application / Network rule it work fine:
I have created a firewall rule with firewall policy like below:
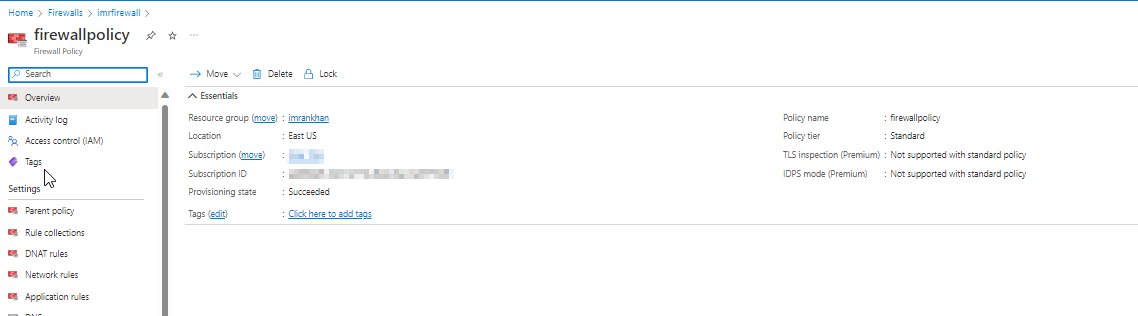
Added application rule:
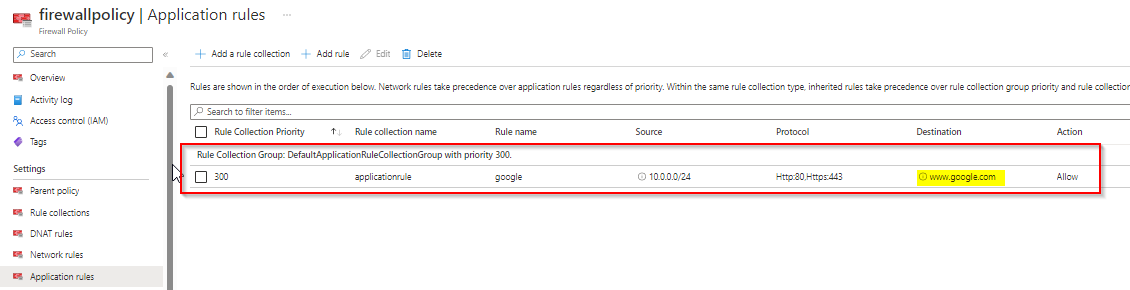
Network rule:
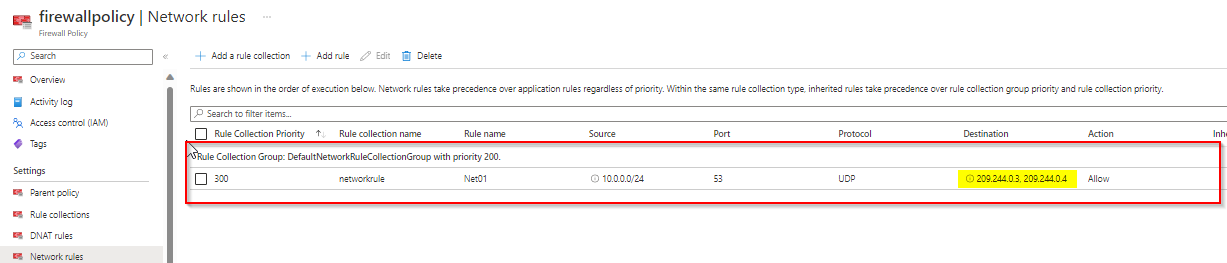
DNAT rule:
- Check your source ip should be your virtual network subnet
- Use destination address as the public ip of your firewall and port and translated port as 3389
- Translated Address should be your virtual machine private ip address
Then, Go to virtual machine -> Networking -> click on network interface -> under setting DNS server -> custom
Add your destination server 209.244.0.3, 209.244.0.4 same like below:
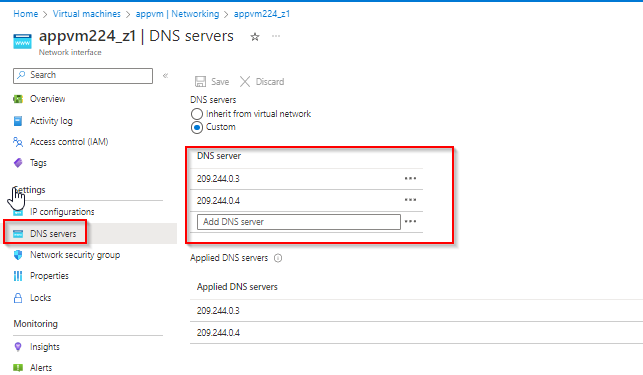
Make sure to Restart your virtual machine and try to connect remote desktop with you firewall public ip.
After restart when I try to connect with my external www.google.com it works successfully like below:
You can refer my previous answer to connect sql server to access private endpoints.
CodePudding user response:
The Problem is solved.
It workes only when i connect with the Azure SQL Server FQDN and it dont works with other FQDNs for Example CNAMES etc...
I must to edit my Hosts File on the local Machine and Point the FQDN from the SQL Server to the Public IP Address of the Azure Firewall.
On my DNAT Rule i check the Public IP of the Firewall and forward it to the FQDN or the Private IP from the Private Endpoint (both oft this works).
After this the DNAT Rule works and i can connect to the Firewall when i diable the public Access on the Azure SQL Server Firewall directly.
Regards, Phil
