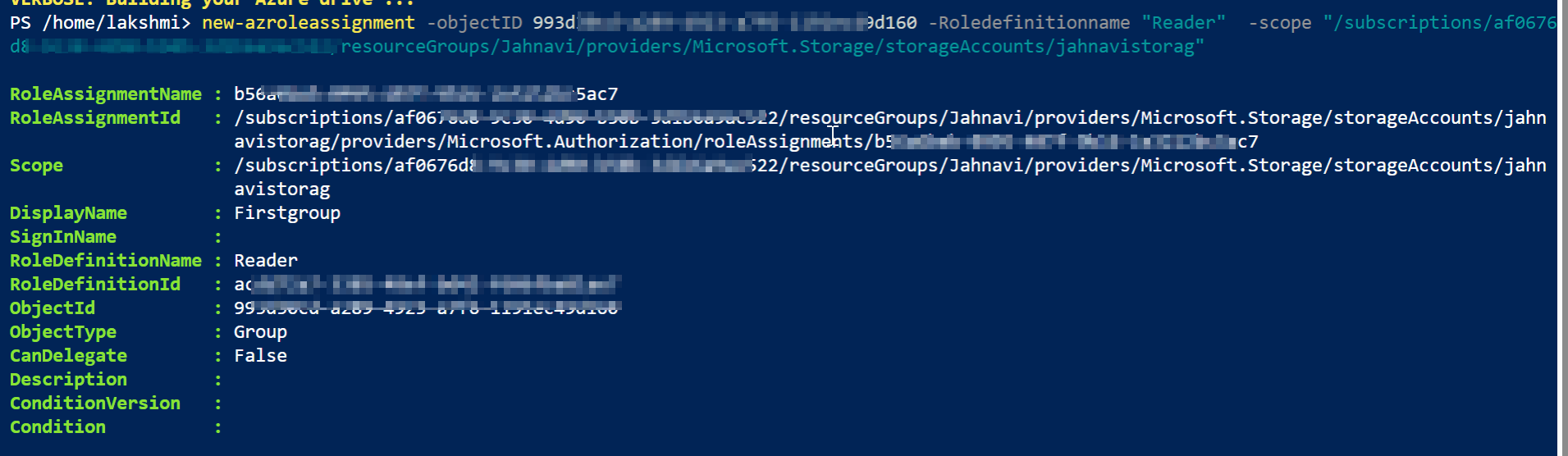
I have requirement to assign Azure Roles to multiple users on subscription scope and Reader role to Managed Identity-Storage Account.
1.Assign Azure RBAC roles to multiple users
2.Assign system assigned managed identity to existing Virtual Machine, Role Reader
Here is the script.
$vm-(Get-Azum-ResourceGroupName <Resourcegrpupname> -Name <VMName>),identity.principalid
New-AzRoleAssignment -Objectid <Objectid> -RoleDefinitionName "Reader" -Scope "/subscriptions/<Id>/resourceGroups/VResourcregroup Name>/providers/Microsoft.Storage/StoragrAccounts/<storageaccoumt>
New-AzRoleAssignment -ObjectId <ID> -RoleDefinationName <RBACRule> -Scope '/Subscription/<I'D>`
`
Script is working,butneed to assign same roles to multiple users.
CodePudding user response:
Assign Azure RBAC roles to multiple users":
To assign roles to multiple users at the same time, simply form a group by adding users who need the "reader" role assignments.
Created a group under AzureAD -> Groups:
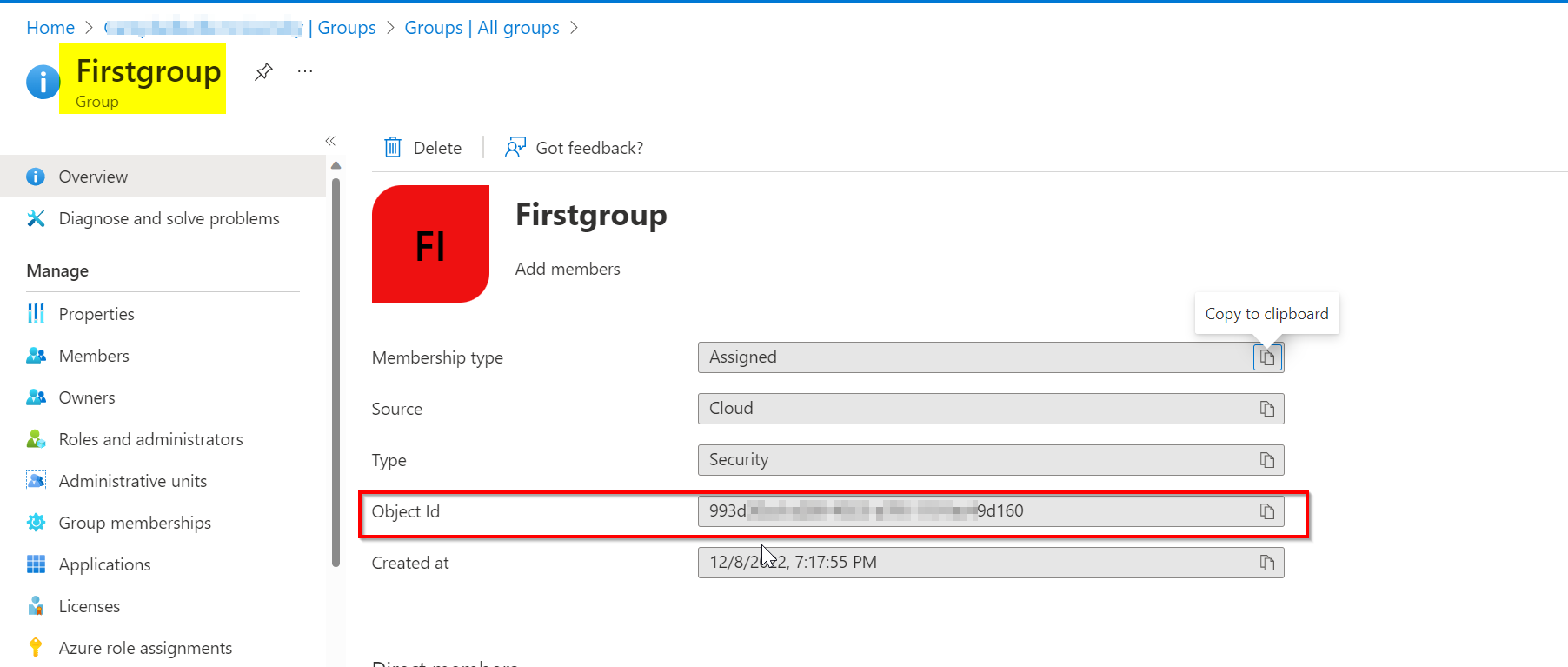
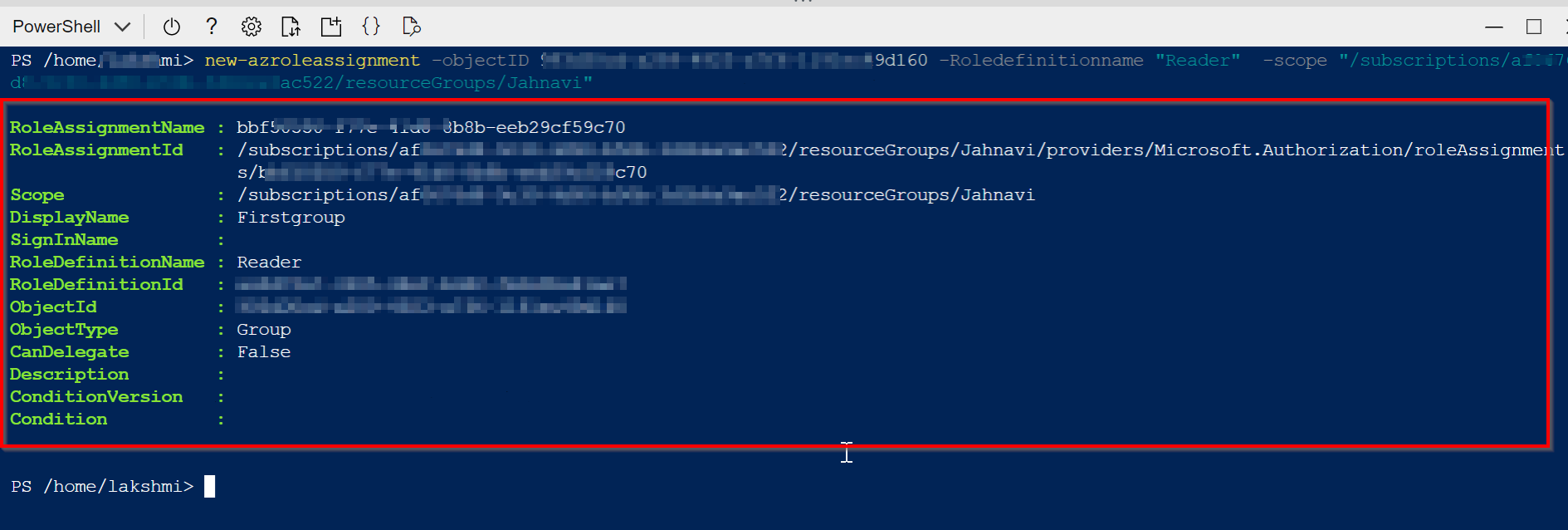
new-azroleassignment -objectID <ObjectId of group> -Roledefinitionname "Reader" -scope "/subscriptions/<subscriptionID>/resourceGroups/xxxxRG/..." #Give scope of the resource as per the requirements.
Output:
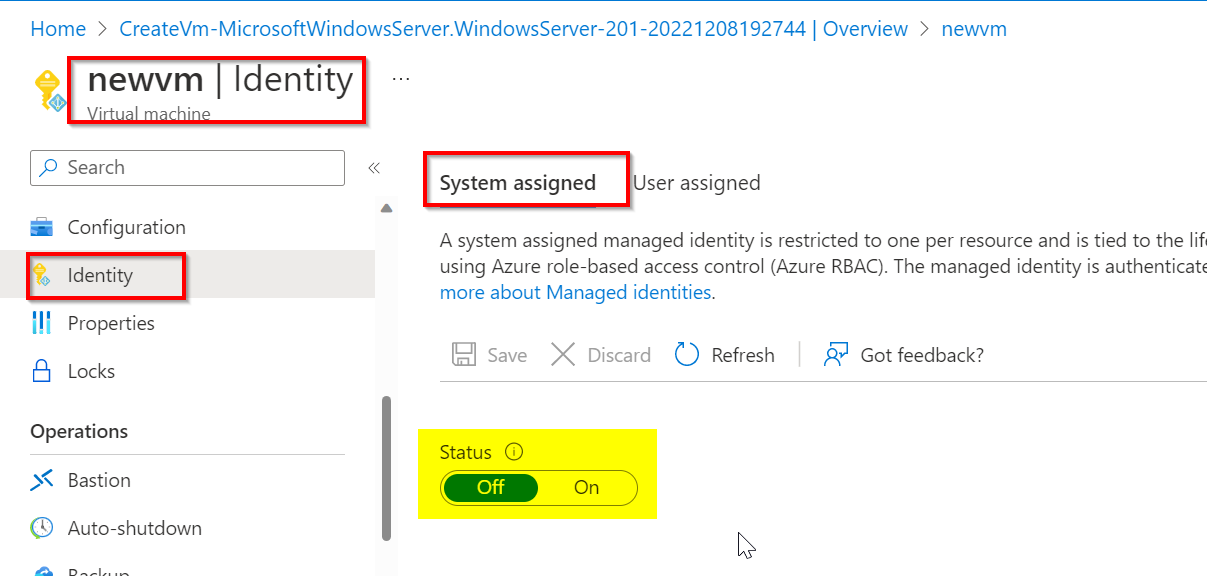
- Assign system assigned managed identity to existing Virtual Machine:
Previously, System assigned identity status is Off:
If not for any particular roles, You can directly update VM configurations/identities by using below commands:
$vminfo = Get-AzVM -ResourceGroupName xxxxxxRG -Name xxxxVM
Update-AzVM -ResourceGroupName xxxxxxRG -VM $vminfo -IdentityType SystemAssigned
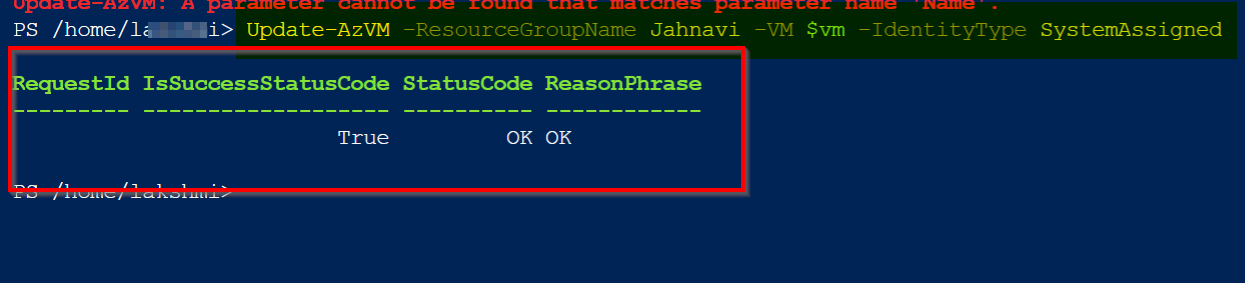
System assigned identity status is "ON" now:
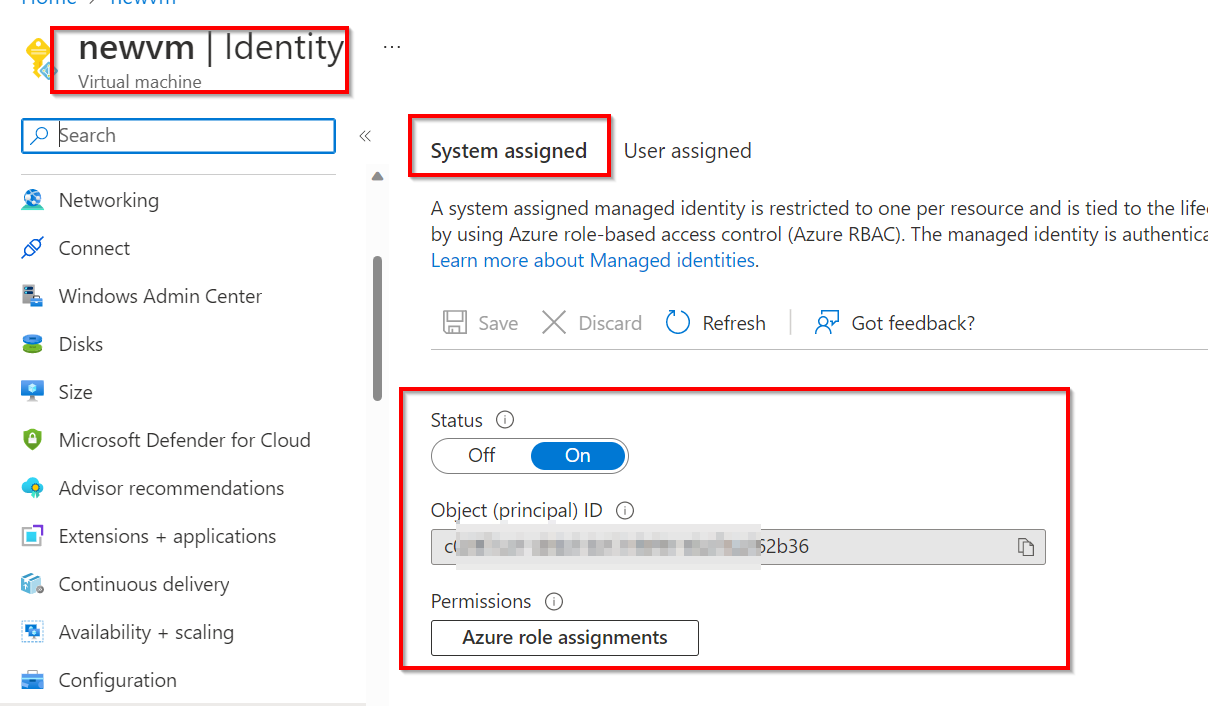
- Assign system assigned managed identity to existing Virtual Machine, Role Reader:
Using PowerShell, you may configure identities for the appropriate app roles under App services. To work with VMs, use AzCLI command
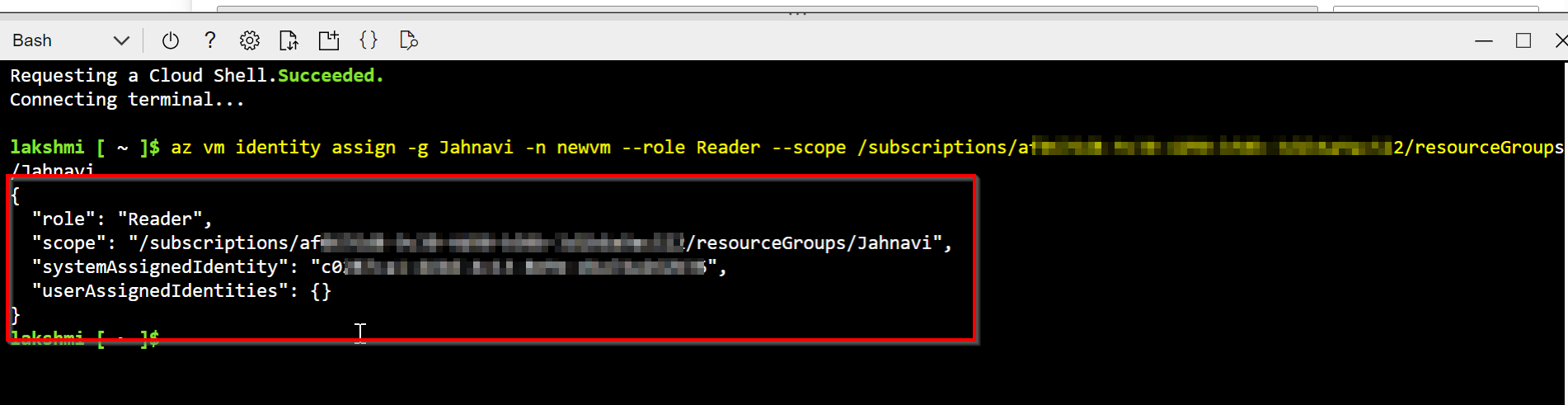
az vm identity to assign the system-assigned identity as shown here:
az vm identity assign -g xxxxResourceGroup -n xxxxVirtualMachineName --role Reader --scope /subscriptions/<subscriptionID>/resourceGroups/xxxxRG
Assigned:
Updated:
- Assigning 'reader' role from VM managed identity to access a storage account:
SID=$(az resource list -n newVM --query [*].identity.principalId --out tsv)
az role assignment create --assignee $SID --role 'Reader' --scope /subscriptions/<subscriptionID>/resourceGroups/xxxxRG/providers/Microsoft.Storage/storageAccounts/<storageaccount>
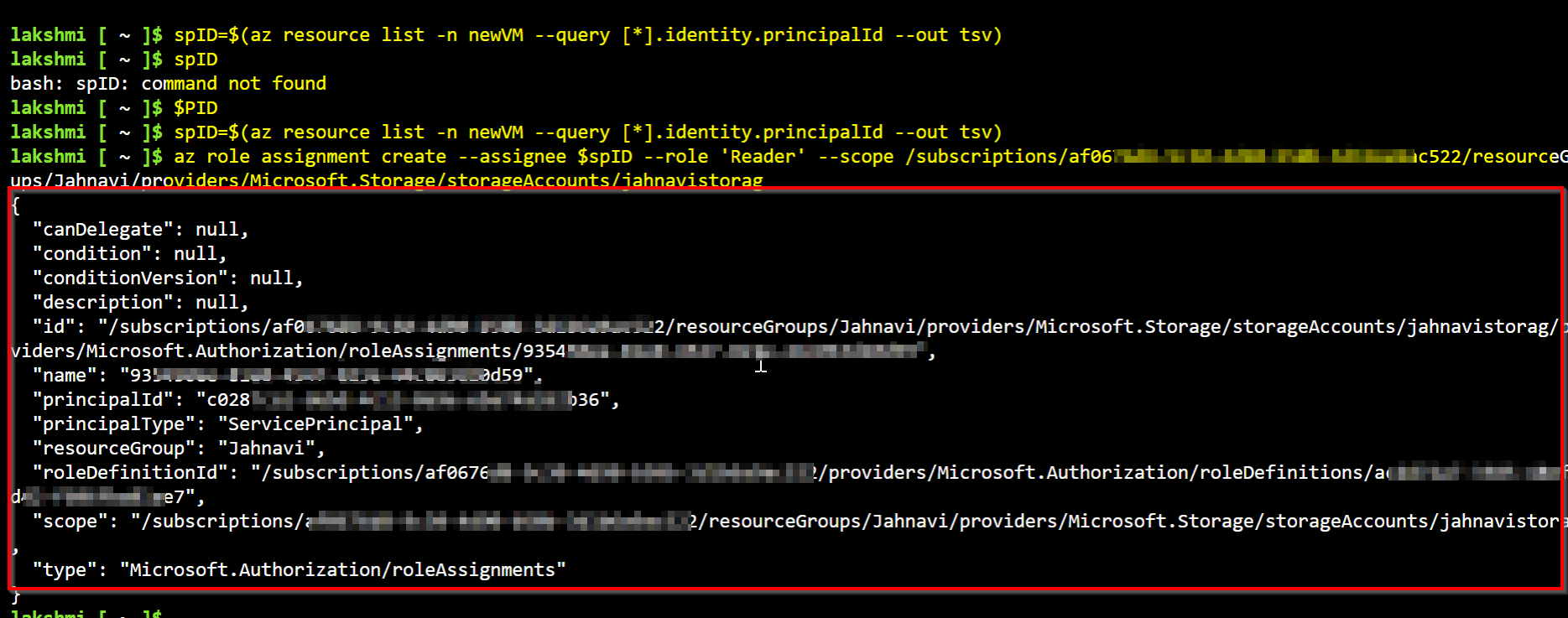
- Assigning Azure RBAC roles with scope as storage account:
new-azroleassignment -objectID <ObjectId of group> -Roledefinitionname "Reader" -scope "/subscriptions/<subscriptionID>/resourceGroups/xxxxRG/providers/Microsoft.Storage/storageAccounts/<storageaccount>