I have created a web application that allows two devices to transfer files to each other through a web server.
The application does not support peer-to-peer connections.
I am trying to achieve a point where the server can serve all pair of clients file transferring, without having a way to know the file's contents.
After a bit of research I've found one way and it is to use PKI. So I don't really understood the part of how it makes it secure.
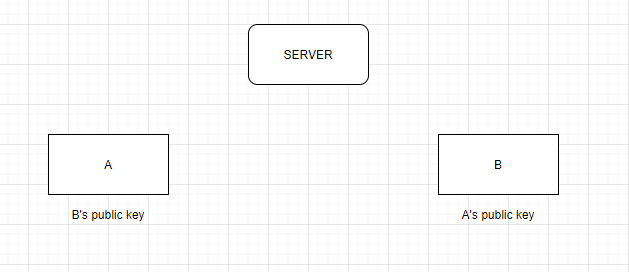
So currently I reached this point:
Where client A get's B's public key and vice-versa, and use the public key to encrypt the file and the other side has the private key to unlock the file.
However this can be cheated, if the server sends a fake public key, for instance, his own public key, and then unlocks the file and save it locally, and then encrypt using the real public key which makes it not 100% trusted.
Now the PKI part comes in, and it is to use a CA like LetsEncrypt, but how can A get B's public key through the server without giving the server an option to cheat and see the real data? Even if you send a signed certificate, if the other client can use it, then the server can do it as-well?
CodePudding user response:
Where client A get's B's public key and vice-versa, and use the public key to encrypt the file and the other side has the private key to unlock the file.
Server does not have private key of either A or B, thus sending file or public keys though server is quite safe. This is what PKI is...!!
Only Asymmetric cryptography can't help encrypt and decrypt large files but it does help you establish symmetric key.
On browser side, you may use any browser extension to access user's certificate store for certificate sharing or for decryption. My Co. provides free Signer.Digital browser extension which is documented in this SO Answer