I am learning about Azure Blob storage using the Microsoft documentation. When I came across this page
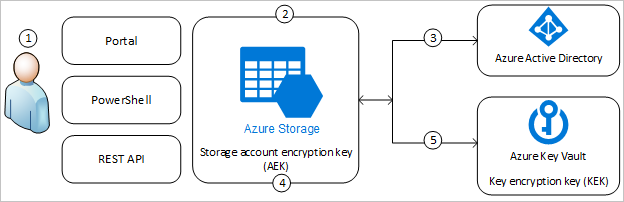
- An Azure Key Vault admin grants permissions to encryption keys to the managed identity that's associated with the storage account.
- An Azure Storage admin configures encryption with a customer-managed key for the storage account.
- Azure Storage uses the managed identity that's associated with the storage account to authenticate access to Azure Key Vault via Azure Active Directory.
- Azure Storage wraps the account encryption key with the customer-managed key in Azure Key Vault.
- For read/write operations, Azure Storage sends requests to Azure Key Vault to unwrap the account encryption key to perform encryption and decryption operations.
On the contrary, when using customer provided keys, you need to provide 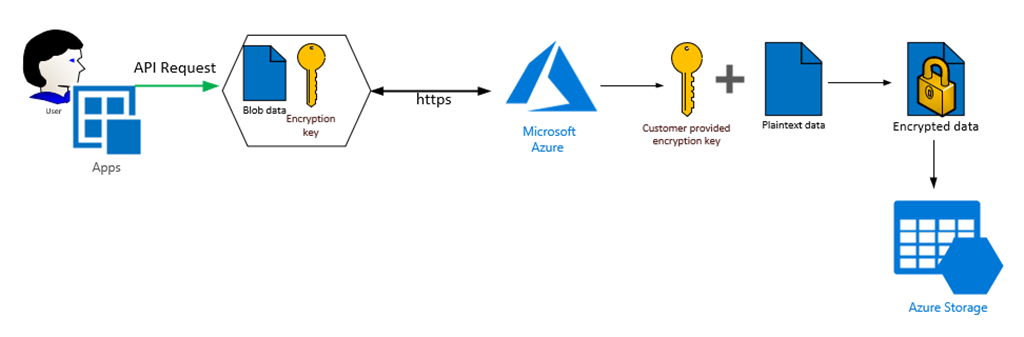
Again, now from the second document I cited:
When a client application provides an encryption key on the request, Azure Storage performs encryption and decryption transparently while reading and writing blob data. Azure Storage writes an SHA-256 hash of the encryption key alongside the blob's contents. The hash is used to verify that all subsequent operations against the blob use the same encryption key.
When a client creates or updates a blob using a customer-provided key on the request, then subsequent read and write requests for that blob must also provide the key.
To send the encryption key as part of the request, a client must establish a secure connection to Azure Storage using HTTPS.
This article could be of help as well.