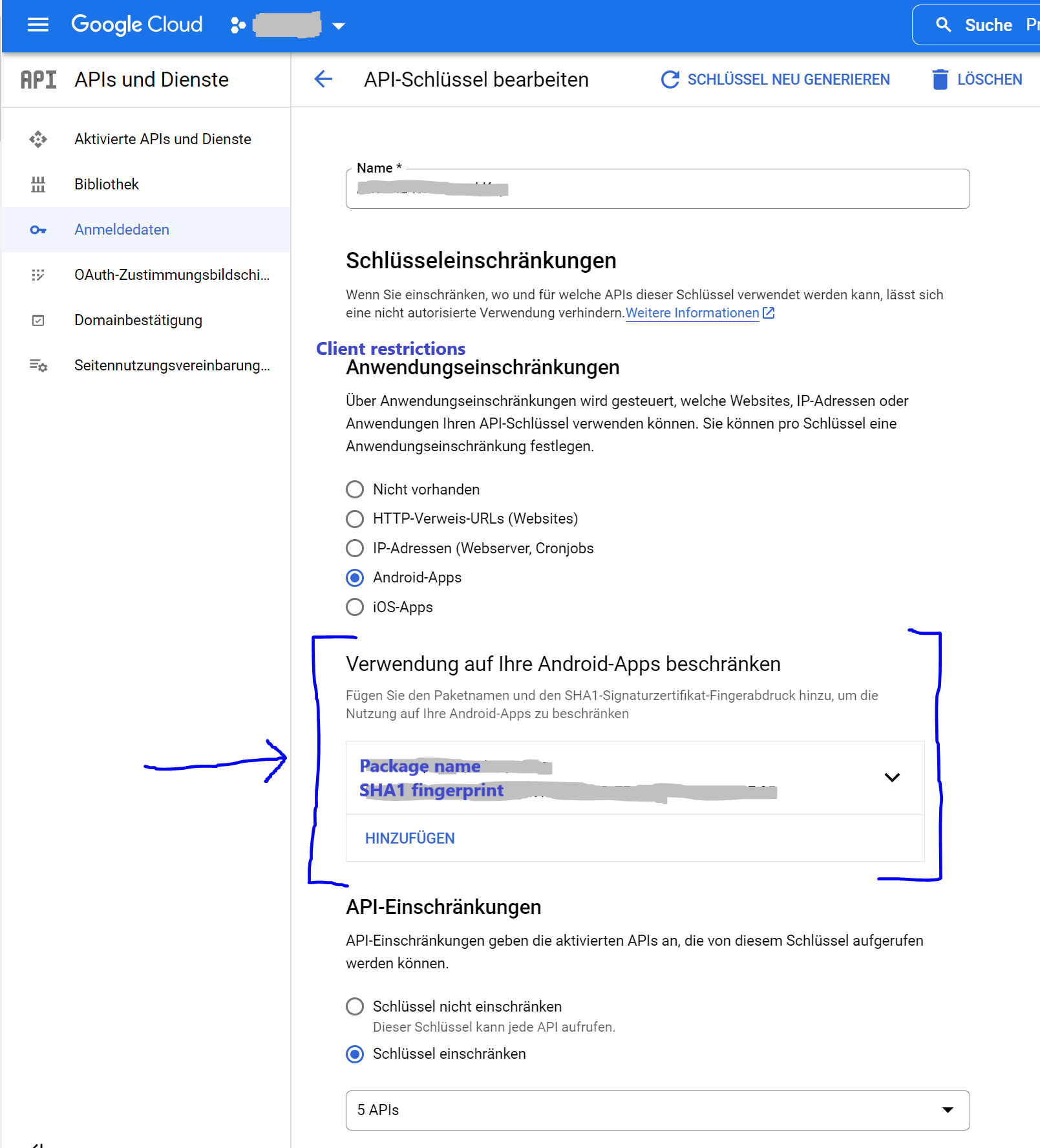
I develop an Android App, that uses some of Googles APIs (e.g. Firebase Cloud Messaging API, Places API...). The API Keys should be restricted to my specific App and to the subset of all Google APIs, that the app uses. So calls to the API should be possible just from my app and it should also be possible to call just a set of defined APIs, not all of them.
It is easy to select the subset of APIs. It was also possible to add the Android App, that is allowed to call the APIs: I needed to add the package-name and the SHA1-fingerprint. All of that is fine for release builds. But debug builds use the AndroidDebugKey, that gets automatically created. So every developer has her/his own AndroidDebugKey. How does this interplay with the API restrictions? Does this mean I would have to add every certificate of every developer to the console? Or gets the AndroidDebugKey ignored by default?
See my (german) screenshot below.
CodePudding user response:
The easiest way is to share the debug keystore between developers, just choosing 1 keystore between your team members (or creating one from scratch) and committing it into the repository of your app.
Then you just need to change your gradle file to point to this debug keystore for debug builds. For example if you choose to use the AS generated one you can have something like:
android {
...
signingConfigs {
debug {
storeFile file("../local-build/debug.keystore")
storePassword "android"
keyAlias "androiddebugkey"
keyPassword "android"
}
}
...
buildTypes {
debug {
....
signingConfig signingConfigs.debug
}
}
}
The debug.keystore is safe enough to commit because PlayStore does not accept an APK signed with this keystore.
In this way you decouple the developers/machines they are working on and you just need to add one SHA-1 in Google Console for local testing and for securing the API.
Be careful to not commit in your repo any data (keystore and passwords) that is used to sign your PROD and/or TEST app accepted by Play Store.
An alternative way could be to having an authenticated remote service which signs your local builds in place of developers, it is more secure but it is more complex to setup.