According to git you can now sign your commits using your existing ssh key.
Now I have no idea any more.
CodePudding user response:
I presented that new option here, where I mention:
The
user.signingKeyconfig for ssh signing supports either a path to a file containing the key or for the sake of convenience a literal string with the ssh public key.To differentiate between those two cases we check if the first few characters contain "
ssh::" which is unlikely to be the start of a path.
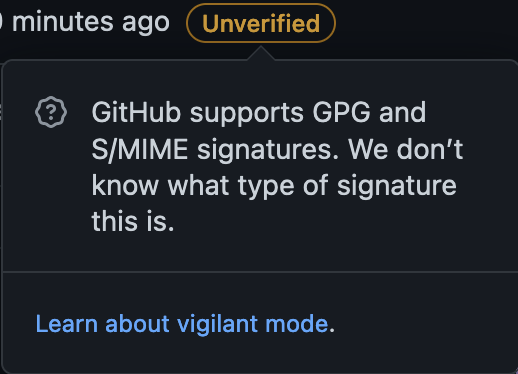
However, it is possible GitHub does not yet recognize an SSH-based signature.
This was mentioned in this thread and added to github-community/community discussion 7744.
Early June 2022 you had:
git does provide direct support for revoking SSH signing keys, beyond the valid-after|before flags mentioned above:
gpg.ssh.revocationFileEither a SSH KRL or a list of revoked public keys (without the principal prefix).
See ssh-keygen(1) for details.If a public key is found in this file then it will always be treated as having trust level "
never" and signatures will show as invalid.
Hopefully GitHub will surface a similar capability.
David Staheli (Product Manager at GitHub) answered:
Thanks for these great suggestions. We might get a first version released and then quickly follow up with some of these ideas. I'll try to share more details once the final scope is set. Though GitHub already recognizes when GPG keys are expired or revoked, I want to make sure we'll support the same for SSH, and if not in v1, how soon thereafter.