In Windows Server, if you create and run a Process, say in .NET, it can, by default, access all (or almost all) the folders on the box. This is also true of ASP.NET w3wp.exe processes. It may not be able to write all the folders, but it can certainly read almost anything it wants and it can write to many folders, too.
I want to create an environment where a given Process, or ideally all non-Administrator processes, can't access anything by default, and can only access 1 or 2 specifically allowed folders. This is ideal for minimizing security footprint.
What is the best way to achieve this? It is really not that clear to me how to actually do this in a systematic way. Any guidance would be greatly appreciated. I am guessing that in newer versions e.g. Windows Server 2022, this may be possible.
CodePudding user response:
Well, for one, often better to NOT join the server to the network domain. That can help huge in terms of security.
Next up? Create a user on the server (not a system wide domain user).
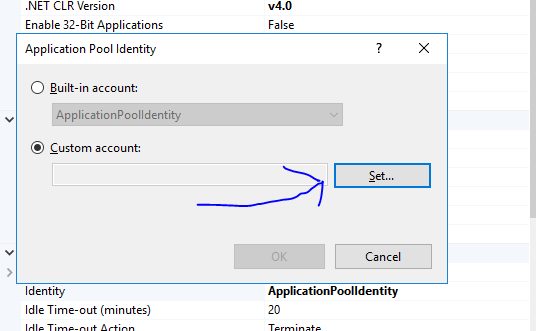
Now, assign that user to the applcation pool. And thus you can now assign rights to that user - say only the few folders you want and need.
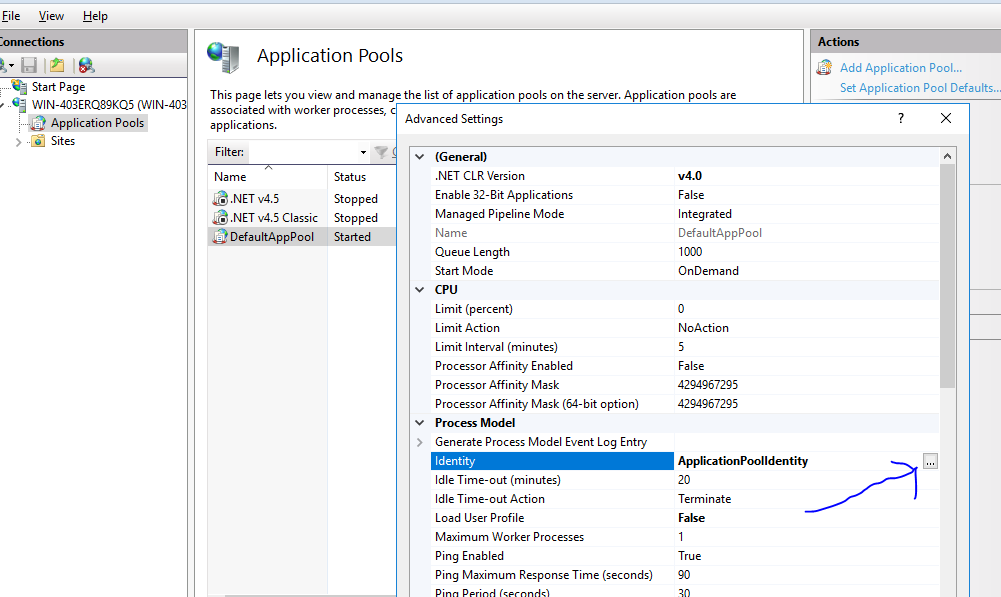
So, in applcation pool, you see this: (right click on app pool - advanced settings)
And then clicking on [...], then you get this:
So, before you do the above, add a local user to the server. That user now will be used for all code that behind access files, and you can thus restrict what your code behind in the web site will use.